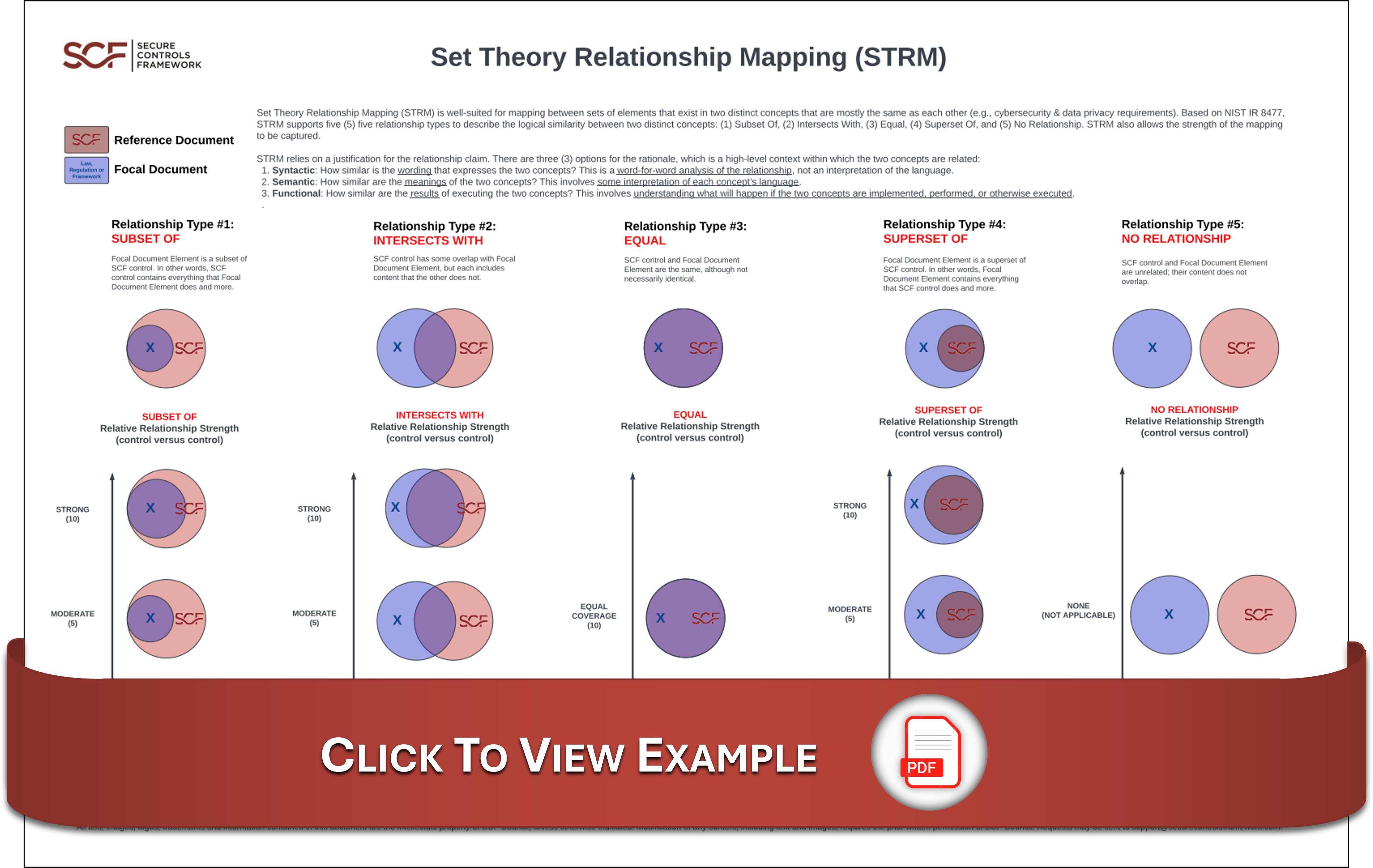
Set Theory Relationship Mapping (STRM)
Starting with release 2024.1, the SCF now leverages the Set Theory Relationship Mapping (STRM) for crosswalk mapping, since STRM is generally well-suited to evaluate cybersecurity and data privacy laws, regulations and frameworks. With the publishing of NIST IR 8477, Mapping Relationships Between Documentary Standards, Regulations, Frameworks, and Guidelines: Developing Cybersecurity and Privacy Concept Mappings it establishes the US Government's playbook for how to perform crosswalk mapping between different cybersecurity and data privacy laws, regulations and frameworks. This document is part of NIST’s broader NIST OLIR Program that is an “effort to facilitate Subject Matter Experts (SMEs) in defining standardized online informative references (OLIRs) between elements of their documents, products, and services and elements of NIST documents…” The SCF currently participates in the National Online Informative References (OLIR) Program and with NIST's preference for STRM, we decided an aligned crosswalk mapping methodology makes sense.
NIST IR 8477 Crosswalk Mapping
What NIST IR 8477 does is provide the “gold standard” practice for how an individual can perform crosswalk mapping with no technology needed, where it can literally be performed with a pencil and piece of paper. Children learn the process of diagramming sentences in grade school (e.g., Reed–Kellogg model) with pencils and paper. This is the process of graphically identifying nouns, verbs, adjectives and modifiers to teach proper sentence structure for how various components of language work together to communicate an idea. With the advent of Artificial Intelligence (AI), the ability to diagram sentences in both computer and human-readable format is achievable through Natural Language Processing (NLP). From a cybersecurity crosswalking perspective, NLP can be used to evaluate a control statement (e.g., must have firewall) to identify the noun (e.g., firewall) and verb (e.g., must have) to determine the relative strength it maps to a different control (e.g., shall have network defense appliances). Where that becomes interesting is both in protecting the underlying content (e.g., Intellectual Property (IP)) and patentability.
Expert-Derived Content (EDC) vs Natural Language Processing (NLP)
While the SCF leverages expert-derived content (e.g., human subject-matter experts), other solutions use NLP to create their crosswalk mapping. One significant downside for those solutions leveraging NLP is their forfeit of IP since AI-generated content is currently prohibited from copyright protections due to the content not being the work of a human creator. Therefore, NLP-generated content could be considered free content from an IP perspective, since a copyright of AI-generated content would not be enforceable.
Where it gets even more fascinating with AI-based solutions in the compliance space is with patentability for inventions due to the "mental steps" doctrine. In 2014, the US Supreme Court ruled that inventions are ineligible for patenting if the patent claim is something a human could do in their mind or with paper and pencil (e.g., a human performing sentence diagramming on a piece of paper and comparing the results of that sentence diagram with another). That landmark case (Alice Corp. v. CLS Bank International) established a new uncertainty about patent eligibility of AI and machine learning technologies. The result of Alice is that patents issued for compliance solutions leveraging NLP to perform crosswalk mapping may not hold up to scrutiny by the Patent Trial and Appeal Board (PTAB) given NIST published a document that describes how to perform crosswalk mapping without the assistance of technology.
How The SCF Is Utilizing STRM
You can click on the image below to see a PDF version of how the SCF is utilizing STRM, as well as an example for what that looks like with a few NIST CSF 2.0 controls:
STRM Examples
You can purchase Excel versions of the Set Theory Relationship Mappings (STRM) mappings at the SCF Store. The current list of Set Theory Relationship Mappings (STRM) include the following:
- General - Critical Security Controls (CSC) version 8.1 - https://securecontrolsframework.com/content/strm/scf-strm-general-cis-csc-8-1.pdf
- General - GovRAMP - https://securecontrolsframework.com/content/strm/scf-strm-general-govramp.pdf
- General - IEC TR 60601-4-5:2021 - Medical electrical equipment - Part 4-5: Guidance and interpretation - Safety-related technical security specifications - https://securecontrolsframework.com/content/strm/scf-strm-general-iec-tr-60601-4-5.pdf
- General - International Maritime Organization (IMO) Guidelines on Maritime Cyber Risk Management - https://securecontrolsframework.com/content/strm/scf-strm-general-imo-maritime-cyber-risk-management.pdf
- General - ISO/IEC 27001:2022 - Information Security Management Systems (ISMS) - Requirements - https://securecontrolsframework.com/content/strm/scf-strm-general-iso-27001-2022.pdf
- General - ISO/IEC 27002:2022 - Information security, cybersecurity and privacy protection - Information security controls - https://securecontrolsframework.com/content/strm/scf-strm-general-iso-27002-2022.pdf
- General - ISO/IEC 27701: 2025 - Privacy information management systems - https://securecontrolsframework.com/content/strm/scf-strm-general-iso-27701-2025.pdf
- General - ISO/IEC 29100:2024 Information technology — Security techniques — Privacy framework - https://securecontrolsframework.com/content/strm/scf-strm-general-iso-29100-2024.pdf
- General - ISO/IEC 42001:2023 - Information technology - Artificial intelligence - Management system - https://securecontrolsframework.com/content/strm/scf-strm-general-iso-42001-2023.pdf
- General - Insurance Data Security Model Law (MDL-668) - https://securecontrolsframework.com/content/strm/scf-strm-general-naic-insurance-data-security-model-law-668.pdf
- General - NIST AI 100-1 (Artificial Intelligence Risk Management Framework 1.0) - https://securecontrolsframework.com/content/strm/scf-strm-general-nist-ai-100-1-rmf.pdf
- General - NIST AI 600-1 (AI RMF Generative Artificial Intelligence Profile) - https://securecontrolsframework.com/content/strm/scf-strm-general-nist-ai-600-1.pdf
- General - NIST SP 800-53 R5 - Security and Privacy Controls for Information Systems and Organizations - https://securecontrolsframework.com/content/strm/scf-strm-general-nist-800-53-r5-2.pdf
- General - NIST SP 800-161 R1 - Cybersecurity Supply Chain Risk Management Practices for Systems and Organizations - https://securecontrolsframework.com/content/strm/scf-strm-general-nist-800-161-r1.pdf
- General - NIST SP 800-171 R2 - Protecting CUI in Nonfederal Systems and Organizations - https://securecontrolsframework.com/content/strm/scf-strm-general-nist-800-171-r2.pdf
- General - NIST SP 800-171 R3 - Protecting CUI in Nonfederal Systems and Organizations - https://securecontrolsframework.com/content/strm/scf-strm-general-nist-800-171-r3.pdf
- General - NIST SP 800-171A - Assessing Security Requirements for Controlled Unclassified Information - https://securecontrolsframework.com/content/strm/scf-strm-general-nist-800-171a.pdf
- General - NIST SP 800-171A R3 - Assessing Security Requirements for Controlled Unclassified Information - https://securecontrolsframework.com/content/strm/scf-strm-general-nist-800-171a-r3.pdf
- General - NIST SP 800-172 - Protecting Controlled Unclassified Information in Nonfederal Systems and Organizations: Enhanced Security Requirements for Critical Programs and High Value Assets - https://securecontrolsframework.com/content/strm/scf-strm-general-nist-800-172.pdf
- General - NIST SP 800-207 - Zero Trust Architecture - https://securecontrolsframework.com/content/strm/scf-strm-general-nist-800-207.pdf
- General - NIST SP 800-218 - Secure Software Development Framework (SSDF) Version 1.1 - https://securecontrolsframework.com/content/strm/scf-strm-general-nist-800-218.pdf
- General - NIST Cybersecurity Framework (CSF) v2.0 - https://securecontrolsframework.com/content/strm/scf-strm-general-nist-csf-2-0.pdf
- General - OECD Privacy Principles - https://securecontrolsframework.com/content/strm/scf-strm-general-oecd-privacy-principles.pdf
- General - Payment Card Industry Data Security Standard (PCI DSS) v4.01 - https://securecontrolsframework.com/content/strm/scf-strm-general-pci-dss-4-0-1.pdf
- General - Space Attack Research & Tactic Analysis (SPARTA) Countermeasures - https://securecontrolsframework.com/content/strm/scf-strm-general-sparta.pdf
- General - Trusted Information Security Assessment Exchange (TISAX) ISA 6.0.3 - https://securecontrolsframework.com/content/strm/scf-strm-general-tisax-6-0-3.pdf
- US - CISA Cross-Sector Cybersecurity Performance Goals (CPG) - https://securecontrolsframework.com/content/strm/scf-strm-us-fed-dhs-cisa-cpg.pdf
- US - Criminal Justice Information Services (CJIS) Security Policy v5.9.3 - https://securecontrolsframework.com/content/strm/scf-strm-us-fed-cjis-5-9-3.pdf
- US - Cybersecurity Maturity Model Certification (CMMC) v2.0 Level 1 - https://securecontrolsframework.com/content/strm/scf-strm-us-fed-dod-cmmc-2-level-1.pdf
- US - Cybersecurity Maturity Model Certification (CMMC) v2.0 Level 1 Assessment Objectives - https://securecontrolsframework.com/content/strm/scf-strm-us-fed-dod-cmmc-2-level-1-aos.pdf
- US - Cybersecurity Maturity Model Certification (CMMC) v2.0 Level 2 - https://securecontrolsframework.com/content/strm/scf-strm-general-nist-800-171a.pdf
- US - Data Privacy Framework (DPF) - https://securecontrolsframework.com/content/strm/scf-strm-us-fed-data-privacy-framework.pdf
- US - DoD Zero Trust Execution Roadmap - https://securecontrolsframework.com/content/strm/scf-strm-us-fed-dod-zt-roadmap.pdf
- US - DoD Zero Trust Reference Architecture v2 - https://securecontrolsframework.com/content/strm/scf-strm-us-fed-dod-zta-reference-architecture-2-0.pdf
- US - CISA Secure Software Development Attestation Form (SSDAF) - https://securecontrolsframework.com/content/strm/scf-strm-us-fed-dhs-cisa-ssdaf.pdf
- US - Department of Homeland Security (DHS) Cybersecurity and Infrastructure Security Agency (CISA) Trusted Internet Connections 3.0 Security Capabilities Catalog - https://securecontrolsframework.com/content/strm/scf-strm-us-fed-dhs-cis-tic-3-0.pdf
- US - Executive Order 14028 (EO 14028) - https://securecontrolsframework.com/content/strm/scf-strm-us-eo-14028.pdf
- US - Farm Credit Administration (FCA) Cyber Risk Management - https://securecontrolsframework.com/content/strm/scf-strm-us-fed-fca-crm.pdf
- US - Fair Information Practice Principles (FIPPs) - https://securecontrolsframework.com/content/strm/scf-strm-us-fed-fipps.pdf
- US - Gramm Leach Bliley Act (GLBA) - CFR 314 (Dec 2023) - https://securecontrolsframework.com/content/strm/scf-strm-us-fed-glba-cfr-314.pdf
- US - HHS § 155.260 Privacy and Security of Personally Identifiable Information - https://securecontrolsframework.com/content/strm/scf-strm-us-fed-45-cfr-155-260.pdf
- US - HIPAA Administrative Simplification (2013) - https://securecontrolsframework.com/content/strm/scf-strm-us-fed-hipaa-simplification-2013.pdf
- US - HIPAA Security Rule (includes mapping to NIST SP 800-66 R2) - https://securecontrolsframework.com/content/strm/scf-strm-us-fed-hipaa-security-rule.pdf
- US - North American Electric Reliability Corporation Critical Infrastructure Protection (NERC CIP) 2024 - https://securecontrolsframework.com/content/strm/scf-strm-us-fed-nerc-cip-2024.pdf
- US - Cybersecurity Final Rule (Cybersecurity Risk Management, Strategy, Governance, and Incident Disclosure) - 17 CFR Parts 229, 232, 239, 240, and 249 - https://securecontrolsframework.com/content/strm/scf-strm-us-fed-sec-cybersecurity-rule.pdf
- US - CA - California Consumer Privacy Act (CCPA) January 2026 (amended California Privacy Rights Act (CPRA)) - https://securecontrolsframework.com/content/strm/scf-strm-us-state-ca-ccpa-2026.pdf
- US - NV - Nevada Operation of Gaming Establishments - Regulation 5.260 (Cybersecurity) - https://securecontrolsframework.com/content/strm/scf-strm-us-state-nv-regulation-5.pdf
- US - NY - Cybersecurity Requirements for Financial Services Companies (DFS 23 NYCRR500) - 2023 Amendment 2 - https://securecontrolsframework.com/content/strm/scf-strm-us-state-ny-dfs-23-nycrr500-amd2.pdf
- US - OR - Consumer Privacy Act (SB 619) - https://securecontrolsframework.com/content/strm/scf-strm-us-state-or-cpa.pdf
- US - TN - Information Protection Act - https://securecontrolsframework.com/content/strm/scf-strm-us-state-tn-information-protection-act.pdf
- US - TX - SB 2610 (Safe Harbor Law) - https://securecontrolsframework.com/content/strm/scf-strm-us-state-tx-sb2610.pdf
- US - VA - Virginia Consumer Data Protection Act (2023) - https://securecontrolsframework.com/content/strm/scf-strm-us-state-va-cdpa.pdf
- EMEA - EU Artificial Intelligence (AI)I Act (Regulation (EU) 2024/1689) - https://securecontrolsframework.com/content/strm/scf-strm-emea-eu-ai-act.pdf
- EMEA - EU Cyber Resilience Act - https://securecontrolsframework.com/content/strm/scf-strm-emea-eu-cyber-resilience-act.pdf
- EMEA - EU Cyber Resilience Act - Annexes - https://securecontrolsframework.com/content/strm/scf-strm-emea-eu-cyber-resilience-act-annexes.pdf
- EMEA - Digital Operational Resilience Act (DORA) (2023) - https://securecontrolsframework.com/content/strm/scf-strm-emea-eu-dora.pdf
- EMEA - General Data Protection Regulation (GDPR) - https://securecontrolsframework.com/content/strm/scf-strm-emea-eu-gdpr.pdf
- EMEA - ENISA NIS2 (Directive (EU) 2022/2555) - https://securecontrolsframework.com/content/strm/scf-strm-emea-eu-nis2.pdf
- EMEA - ENISA NIS2 Annex - https://securecontrolsframework.com/content/strm/scf-strm-emea-eu-nis2-annex.pdf
- EMEA - Saudi Arabia IoT CGIoT-1:2024 - https://securecontrolsframework.com/content/strm/scf-strm-emea-sa-cybersecurity-guidelines-iot.pdf
- EMEA - Saudi Arabia Personal Data Protection Law (PDPL) - https://securecontrolsframework.com/content/strm/scf-strm-emea-sa-pdpl.pdf
- EMEA - BOE-A-2022-7191 - https://securecontrolsframework.com/content/strm/scf-strm-emea-spain-boe-a-2022-7191.pdf
- EMEA - UAE National Information Assurance Framework (NIAF) - https://securecontrolsframework.com/content/strm/scf-strm-emea-uae-niaf.pdf
- EMEA - Cyber Assessment Framework (CAF) v4.0 - http://securecontrolsframework.com/content/strm/scf-strm-emea-uk-caf-4-0.pdf
- EMEA - Ministry of Defence Standard 05-138 (14 May 2024) - https://securecontrolsframework.com/content/strm/scf-strm-emea-uk-def-stan-05-138.pdf
- APAC - Australia Essential Eight - https://securecontrolsframework.com/content/strm/scf-strm-apac-australia-essential-8.pdf
- APAC - Australian Government Information Security Manual (ISM) (June 2024) - https://securecontrolsframework.com/content/strm/scf-strm-apac-australia-ism-june-2024.pdf
- APAC - China Cybersecurity Law of the People's Republic of China (China Cybersecurity Law) 2017 - https://securecontrolsframework.com/content/strm/scf-strm-apac-china-cybersecurity-law-2017.pdf
- APAC - India Digital Personal Data Protection Act 2023 - https://securecontrolsframework.com/content/strm/scf-strm-apac-india-dpdpa-2023.pdf
- APAC - SEBI Cybersecurity and Cyber Resilience Framework (CSCRF) - https://securecontrolsframework.com/content/strm/scf-strm-apac-india-sebi.pdf
- APAC - NZ Health Information Security Framework (2022) - https://securecontrolsframework.com/content/strm/scf-strm-apac-nz-hisf-2025.pdf
- APAC - HISO 10029:2024 NZ Health Information Security Framework Guidance for Suppliers - https://securecontrolsframework.com/content/strm/scf-strm-apac-nz-hisf-suppliers-2025.pdf
- Americas - B-13 - https://securecontrolsframework.com/content/strm/scf-strm-americas-canada-osfi-b13.pdf
- Americas - Protecting controlled information in non-Government of Canada systems and organizations (ITSP.10.171) - https://securecontrolsframework.com/content/strm/scf-strm-americas-canada-itsp-10-171.pdf
The SCF welcomes community involvement and we provide the ability for community-suggested mapping. The SCF Council provides a downloadable SCF Community STRM Template, that SCF Practitioners can then use to perform their own STRM and submit it to the SCF Council, where it can be evaluated for the possible inclusion in a future SCF release.
Step 1. Define The Focal Document To Be Mapped
We are not here to teach you STRM, so if you want to participate in any community mapping, it is expected that you (1) are very familiar the practices described in NIST IR 8477 and (2) possess the professional competence to conduct crosswalk mapping in accordance with those principles.
The first tab on the STRM template is called "STRM Overview" and there are two highlighted cells near the top of the sheet: the focal document cell and the focal document URL cell.
- In the focal document cell, you must provide the official name of the law, regulation, or framework you are providing mapping for.
- In the focal document URL cell, you must provide a valid hyperlink where the focal document can be downloaded.
Without either of these two pieces of information, the SCF Council will not review your STRM submission.
Step 2. Perform STRM
The second tab of the STRM template is called "Community STRM submission." This is purposely left as a blank template for you to perform your crosswalk mapping:
- Column A is the Focal Document Element #. This is the specific law, regulation, or framework control number. This is a mandatory field. Without a unique FDE value, there is no granularity and means there is nothing that can be mapped to.
- Column B is the Focal Document Element Name. Most laws, regulations and frameworks do not have FDE names, so this is required only if it is available.
- Column C is the Focal Document Element Description. This is the actual text of the law, regulation, or framework. Essentially, it is a cut & paste effort to populate this cell.
- Column D is the proposed SCF Control Name that you feel maps to the Focal Document Element.
- Column E is tied to Column D. This is the SCF control number.
- Column F is tied to Column D. This is the SCF control description.
- Column G is the proposed STRM relationship. There are only 5 options. The relationship can be (1) a Subset Of, (2) Intersects With, (3) Equal to, (4) a Superset Of, or (5) there is No Relationship.
- Column H is the proposed strength of the STRM relationship that has a 1 to 10 rating. A rating of 1 indicates a nominal relationship, a rating of 5 indicates a moderately strong relationship, and a rating of 10 indicates a strong relationship. Realistically, a rating of 10 is going to be given if the STRM relationship is either equal to or where the F-D-E is a subset of the SCF control.
- Column I is an optional notes section where you can provide textual justification for your recommendations.
Step 3. Submit To SCF Council
Once you complete your STRM exercise, you can then email it to the SCF Council for review. Just email the Excel spreadsheet as an attachment to [email protected].