SCF - Make Compliance A Natural Byproduct of Secure Practices
The SCF's mission is to provide a powerful catalyst that will advance how cybersecurity and privacy controls are utilized at the strategic, operational and tactical layers of an organization, regardless of its size or industry.
|
The Secure Controls Framework™ (SCF) focuses on internal controls. These are the cybersecurity and privacy-related policies, standards, procedures, technologies and associated processes that are designed to provide reasonable assurance that business objectives will be achieved and undesired events will be prevented, detected and corrected. This page will covers the following topics:
For your off-line reading pleasure, you can download the PDF version of this helpful information |
The Secure Controls Framework™ (SCF) Is The Common Controls Framework™ (CCF)
|
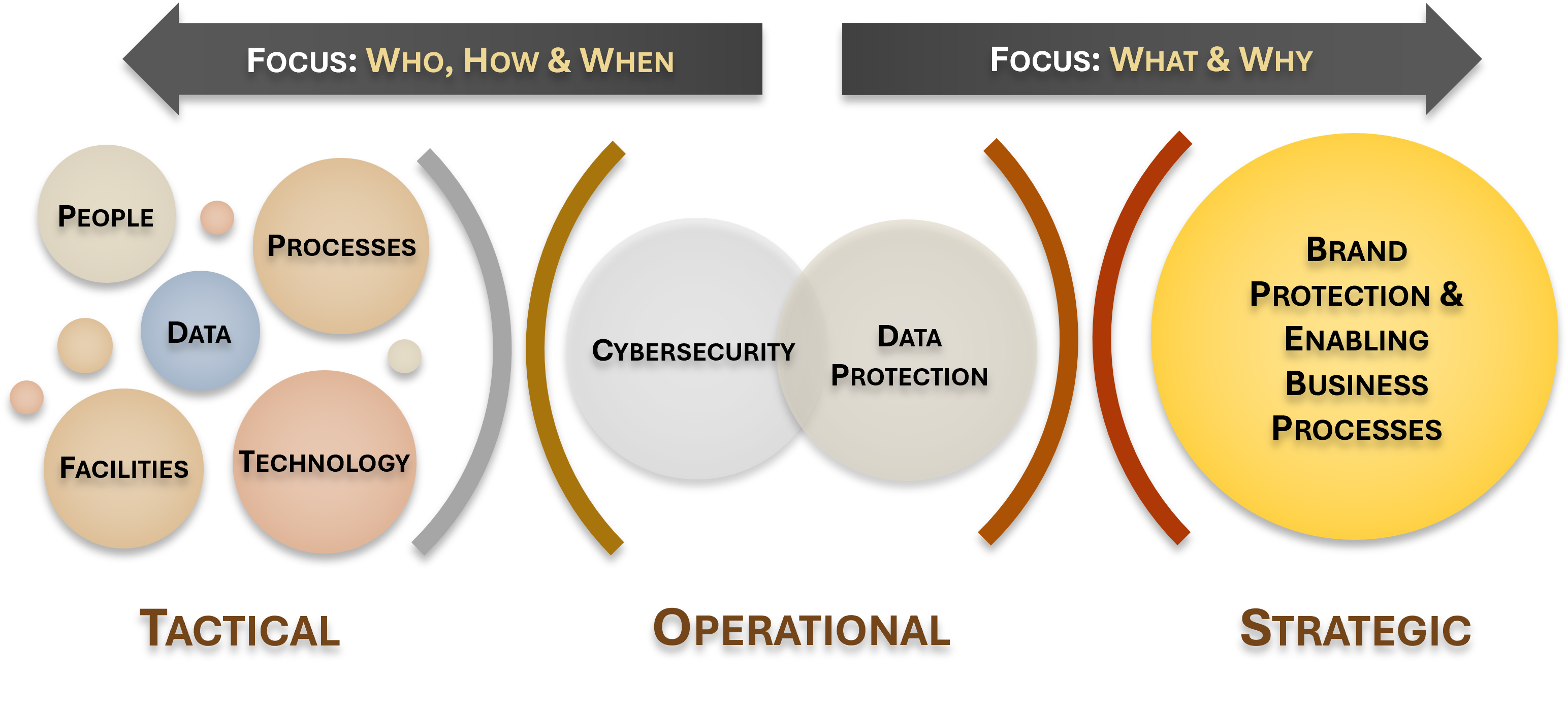
The SCF is a "Rosetta Stone" approach to cybersecurity and privacy controls, which makes it the Common Controls Framework™. The concept of the SCF is to have a metaframework (e.g., framework of frameworks) that is capable of addressing the broader People, Processes, Technology, Data & Facilities (PPTDF) that are what controls fundamentally exists to govern. The SCF can be used to assist with strategic planning down to tactical needs that impact the people, processes and technologies directly impacting your organization. The graphic to the right helps illustrate the relationship between the tactical, operational & strategic levels of governance and where they align based on their focuses. |
 |
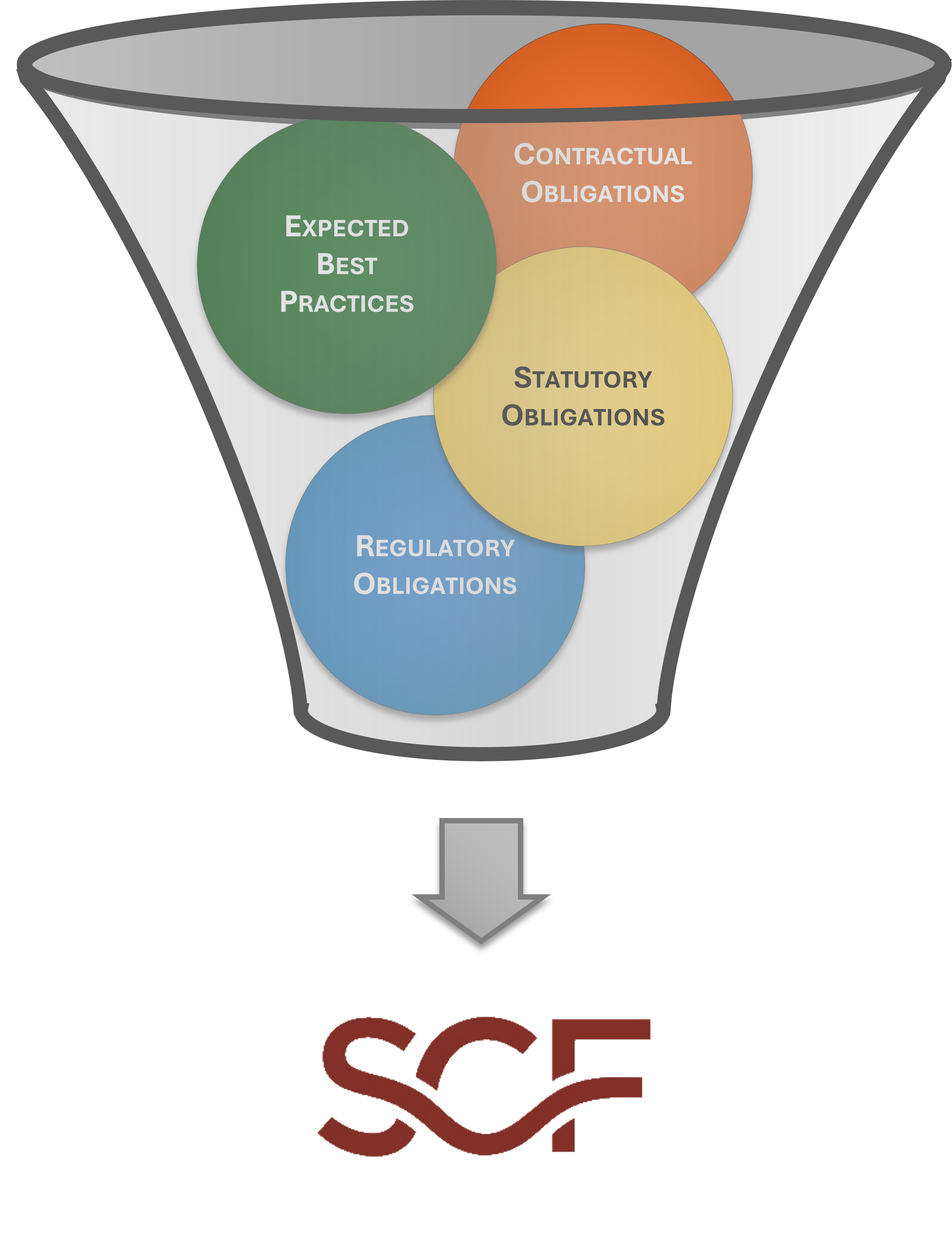 |
Using the SCF should be viewed as a long-term tool to not only help with compliance-related efforts but to ensure security and privacy principles are properly designed, implemented and maintained. The SCF helps implement a holistic approach to protecting the Confidentiality, Integrity, Availability and Safety (CIAS) of your data, systems, applications and other processes. Understanding the requirements for both cybersecurity and privacy principles involves a simple process of distilling expectations. This process is all part of documenting reasonable expectations that are “right-sized” for an organization, since every organization has unique requirements. The approach looks at the following spheres of influence to identify applicable controls:
It is best to visualize the SCF as a buffet of cybersecurity and privacy controls, where there is a selection of 1,000+ controls available to you. Once you know what is applicable to you, you can generate a customized control set that gives you the controls you need to address your statutory, regulatory and contractual obligations. |
Why You Should Use The SCF
There is no sales pitch for using the SCF – the SCF is a free resource, so there is no financial incentive for us to make companies use it:
- For companies that have just one 1-2 compliance requirements, the SCF might be considered overkill for your needs.
- For companies that have 3+ compliance requirements (e.g., organization that has requirements to address ISO 27002, SOC 2, PCI DSS and GDPR), then the SCF is a great tool to streamline the management of cybersecurity and privacy controls.
In developing the SCF, we identified and analyzed over 100 statutory, regulatory and contractual frameworks. Through analyzing these thousands of legal, regulatory and framework requirements, we identified commonalities and this allows several thousand unique controls to be addressed by the controls that makeup the SCF. For instance, a requirement to maintain strong passwords is not unique, since it is required by dozens of laws, regulations and frameworks. This allows one well-worded SCF control to address multiple requirements. This focus on simplicity and sustainability is key to the SCF, since it can enable various teams to speak the same controls language, even though they may have entirely different statutory, regulatory or contractual obligations that they are working towards.
The SCF targets silos, since siloed practices within any organization are inefficient and can lead to poor security, due to poor communications and incorrect assumptions.
What The SCF Is
The SCF is a comprehensive catalog of controls that is designed to enable companies to design, build and maintain secure processes, systems and applications. The SCF addresses both cybersecurity and privacy, so that these principles are designed to be “baked in” at the strategic, operational and tactical levels.
The SCF is:
- A control set.
- A useful tool to provide a “Rosetta Stone” approach to organizing cybersecurity and privacy controls so that the same controls can be used among companies and teams (e.g., privacy, cybersecurity, IT, project, procurement, etc.).
- Free for businesses to use. A result of a volunteer-led effort that uses “expert derived assessments” to perform the mapping from the controls to applicable laws, regulations and other frameworks.
The SCF also contains helpful guidance on possible tools and solutions to address controls. Additionally, it contains maturity criteria that can help an organization plan for and evaluate controls, based on a target maturity level.
What The SCF Is Not
While the SCF is a comprehensive catalog of controls that is designed to enable companies to design, build and maintain secure processes, systems and applications, the SCF will only ever be a control set and is not a “magic bullet” technology solution to address every possible cybersecurity and privacy compliance obligation that an organization faces.
The SCF is not:
- A substitute for performing due diligence and due care steps to understand your specific compliance needs.
- A complete technology or documentation solution to address all your security & privacy needs (e.g., the policies, standards, procedures and processes you need to have in place to be secure and compliant).
- Infallible or guaranteed to meet every compliance requirement your organization offers, since the controls are mapped based on expert-derived assessments to provide the control crosswalking that relies on human expertise and that is not infallible.
Integrated Controls Management (ICM) Approach To Building A Security Program
Building a security program that routinely incorporates security and privacy practices into daily operations requires a mastery of the basics. A useful analogy is with the children's toy, LEGO®. With LEGO® you can build nearly anything you want — either through following directions or using your own creativity. However, it first requires an understanding of how various LEGO® shapes either snap together or are incompatible.
Once you master the fundamentals with LEGO®, it is easy to keep building and become immensely creative since you know how everything interacts. However, when the fundamentals are ignored, the LEGO® structure will be weak and include systemic flaws. Security and privacy really are not much different, since those disciplines are made up of numerous building blocks that all come together to build secure systems and processes. The lack of critical building blocks will lead to insecure and poorly architected solutions.
When you envision each component that makes up a security or privacy “best practice” is a LEGO® block, it is possible to conceptualize how certain requirements are the foundation that form the basis for others components to attach to. Only when the all the building blocks come together and take shape do you get a functional security / privacy program!
Think of the SCF as a toolkit for you to build out your overall security program domain-by-domain so that cybersecurity and privacy principles are designed, implemented and managed by default!
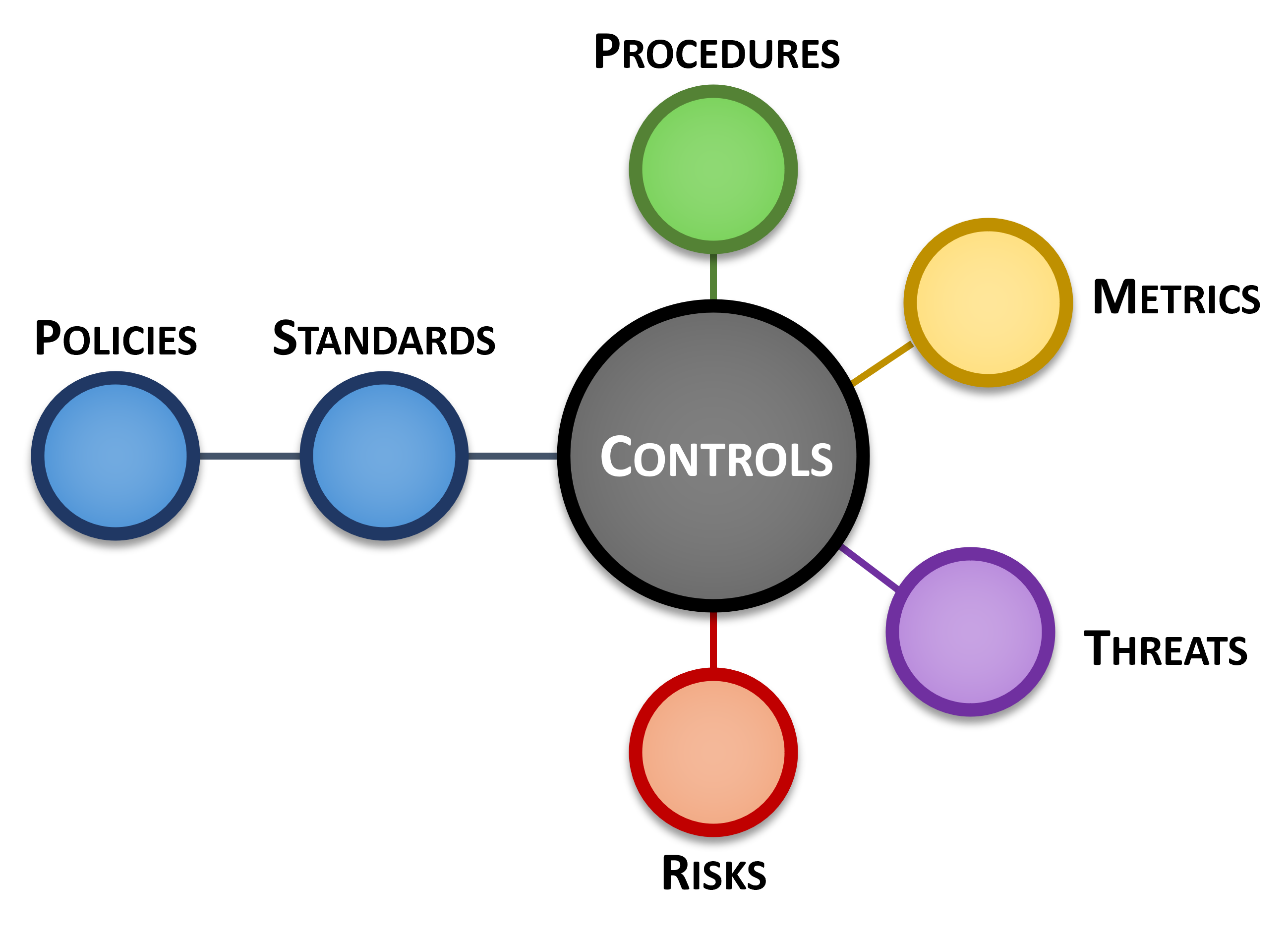
Controls Are Key To Everything In Cybersecurity & Data Protection
|
The premise of ICM is that controls are central to cybersecurity & data privacy operations, as well as the overall business rhythm of an organization. This premise is supported by the Cybersecurity & Data Privacy Risk Management Model (C|P-RMM), that describes the central nature of controls, where not just policies and standards map to controls, but procedures, metrics, threats and risks, as well. ICM takes a different approach from the traditional definition of Governance, Risk Management and Compliance (GRC) and/or Integrated Risk Management (IRM), since ICM is controls-centric, where controls are viewed as the nexus, or central pivoting point, for an organization’s cybersecurity and data privacy operations. OCEG defines GRC as, “GRC is the integrated collection of capabilities that enable an organization to reliably achieve objectives, address uncertainty and act with integrity,” while Gartner jointly defines GRC/IRM as, "a set of practices and processes supported by a risk-aware culture and enabling technologies, that improves decision making and performance through an integrated view of how well an organization manages its unique set of risks." |
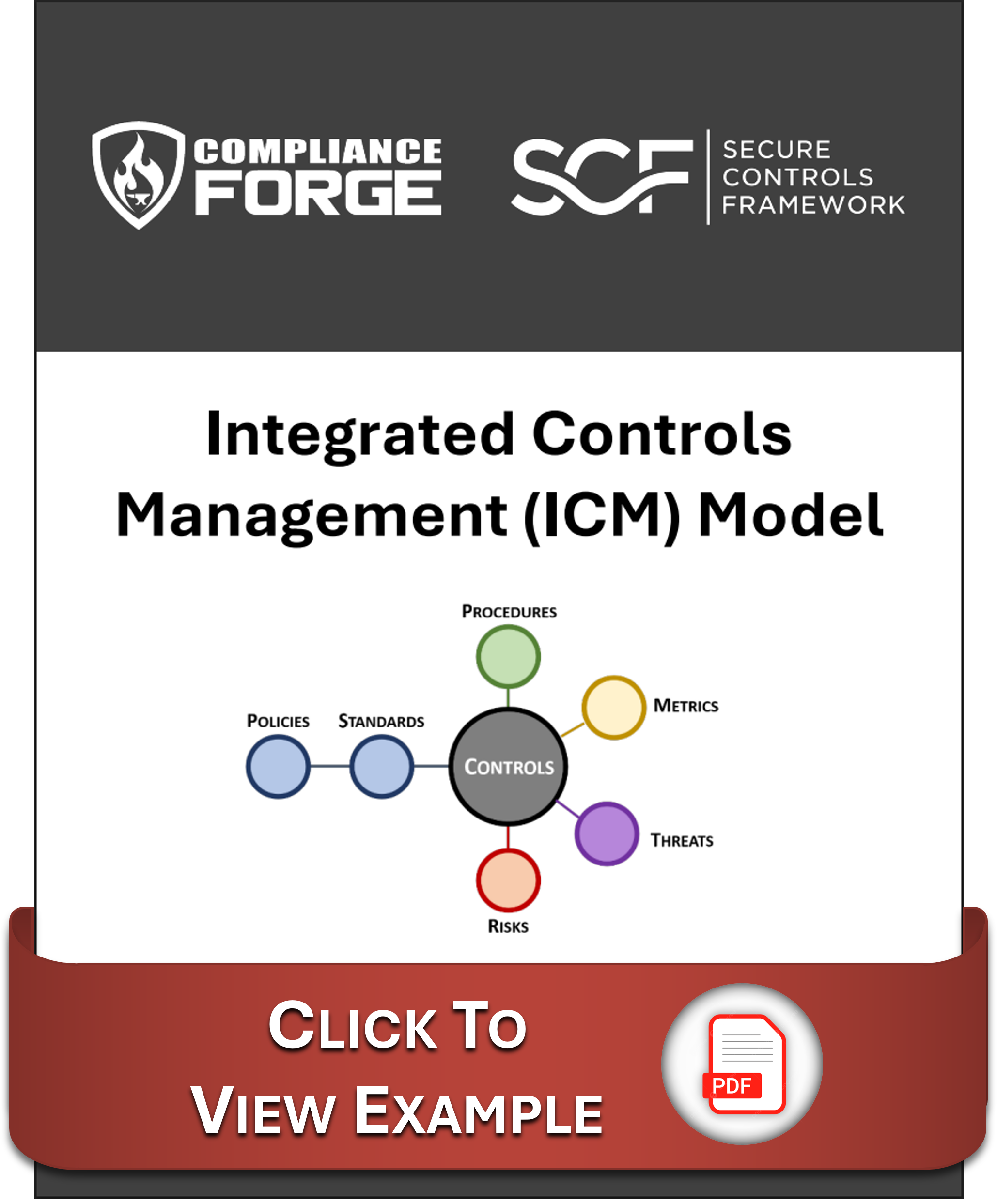 |
|
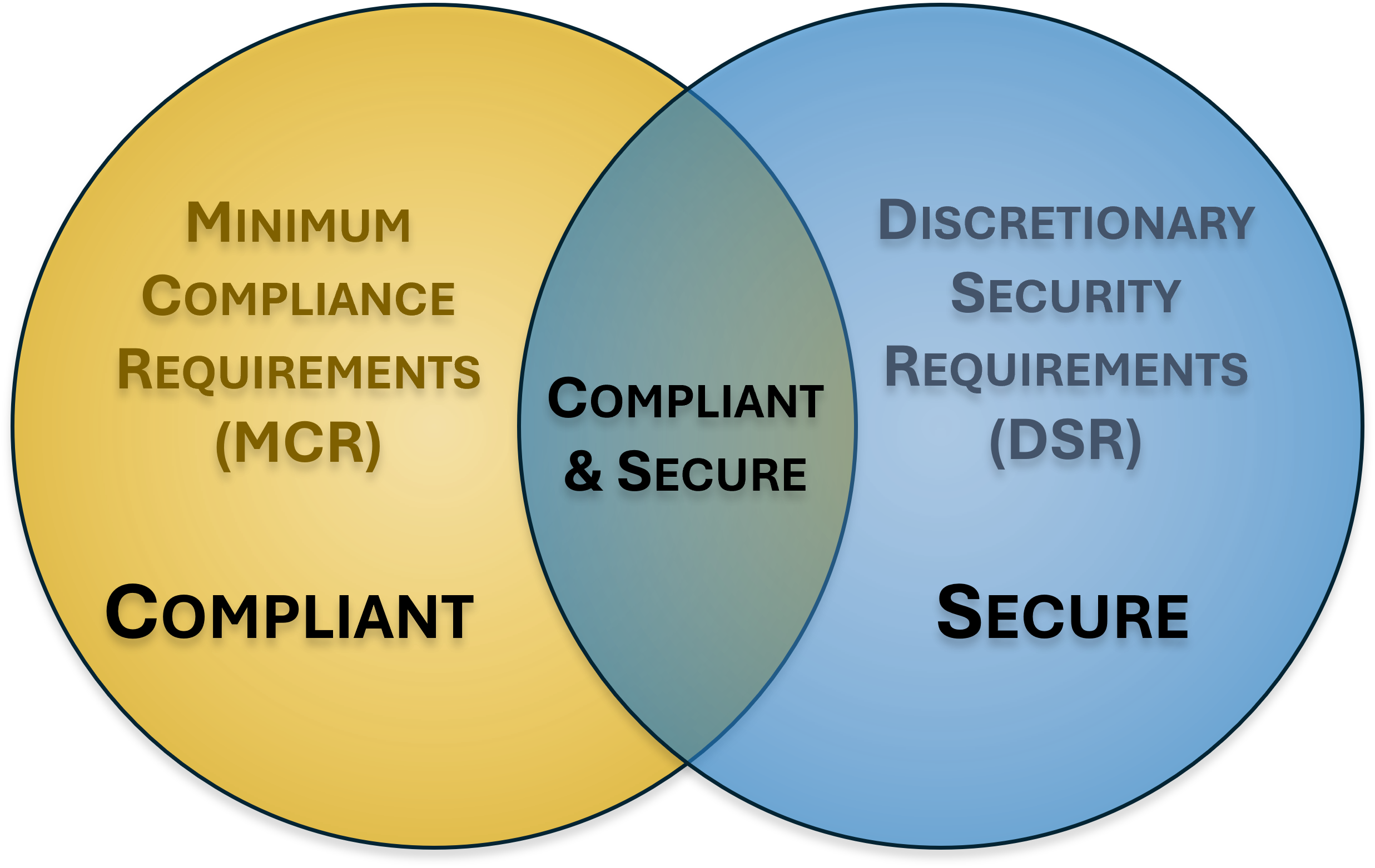
ICM specifically focuses on the need to understand and clarify the difference between "compliant" versus "secure" since that is necessary to have coherent risk management discussions. To assist in this process, an organization’s applicable controls are categorized according to “must have” vs “nice to have” requirements:
|
Using The SCF Starts With Defining "Must Have" & "Nice to Have" Requirements
|
As described above, the concept of MCR & DSR are a crucial step to get right, otherwise you will likely design it incorrectly that will leave gaps that can expose your organization to issues of non-compliance and/or inadequate security practices. When you add MCR & DSR, you are able to define "what right looks like" for your organization, which equates to your Minimum Security Requirements (MSR) that can be published to project teams, risk management, engineers, etc. The MSR is the blueprint for an organization to build security and privacy in by design across the SDLC and business-as-usual operations. |
 |
Plan, Do, Check & Act (PDCA) Approach To Cybersecurity & Data Protection
Within the ICM, its principles are overlaid onto the following graphic to show how a PDCA approach for continuous improvement of your cybersecurity and data protection program is possible:
- Establish Context
- Define Applicable Controls
- Assign Maturity-Based Criteria
- Publish Policies, Standards & Procedures
- Assign Stakeholder Accountability
- Maintain Situational Awareness
- Manage Risk
- Evolve Processes
More Than Just A Control Set
Where the SCF sets itself apart from other metaframeworks is the following:
- Capability maturity criteria for each control
- Proposed control weighting (not all controls are as important in risk management decisions)
- Built-in risk catalog
- Built-in threat catalog
For the capability maturity criteria, we published the Cybersecurity & Data Privacy Capability Maturity Model (C|P-CMM).
To make use of the risk & threat catalogs, we published the Cybersecurity & Data Privacy Risk Management Model (C|P-RMM).
This is where the Integrated Controls Management (ICM) model ties all those capabilities together to help you design the controls that are right for your organization, as well as be able to leverage that same control set to help understand risks and threats. This is a "paint by numbers" approach to operationalizing your cybersecurity and data protection program!
Understanding Cybersecurity & Privacy By Design
Security by Design (SbD)
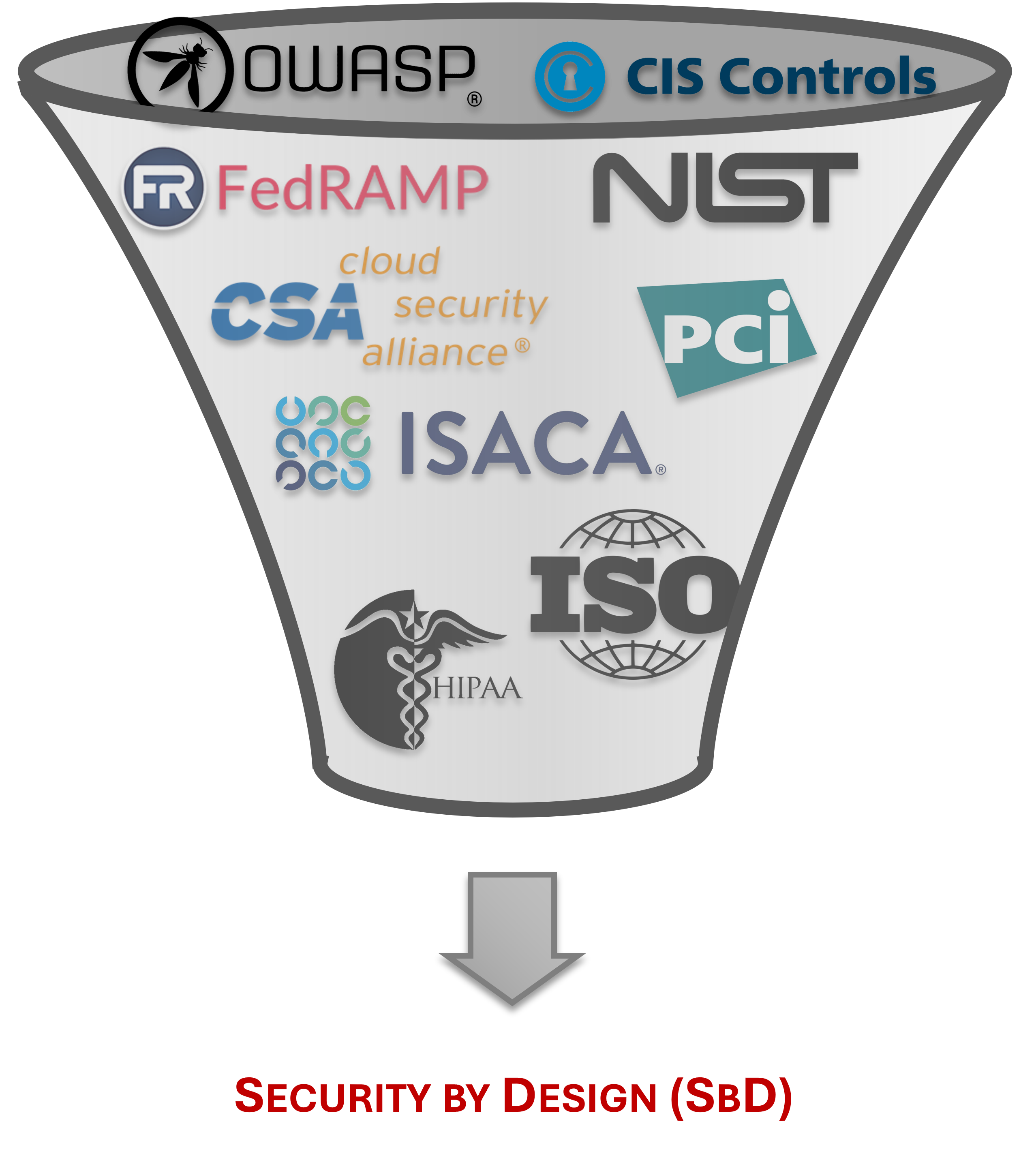 |
These requirements come from numerous sources. In this context, some of the most important cybersecurity frameworks are:
|
Privacy by Design (PbD)
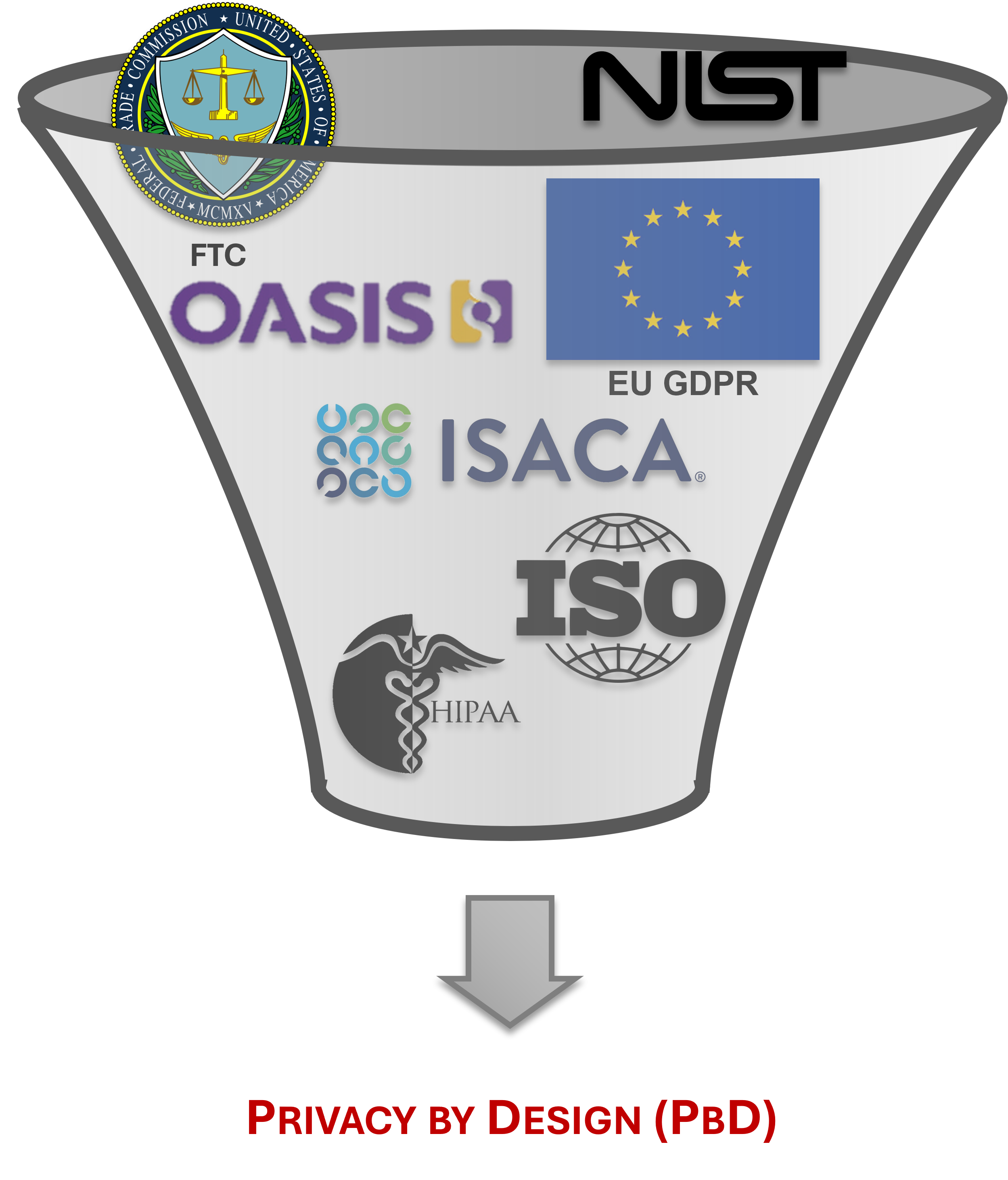 |
These requirements come from numerous sources. In this context, some of the most important privacy frameworks are:
|
How The SCF Is Mapped
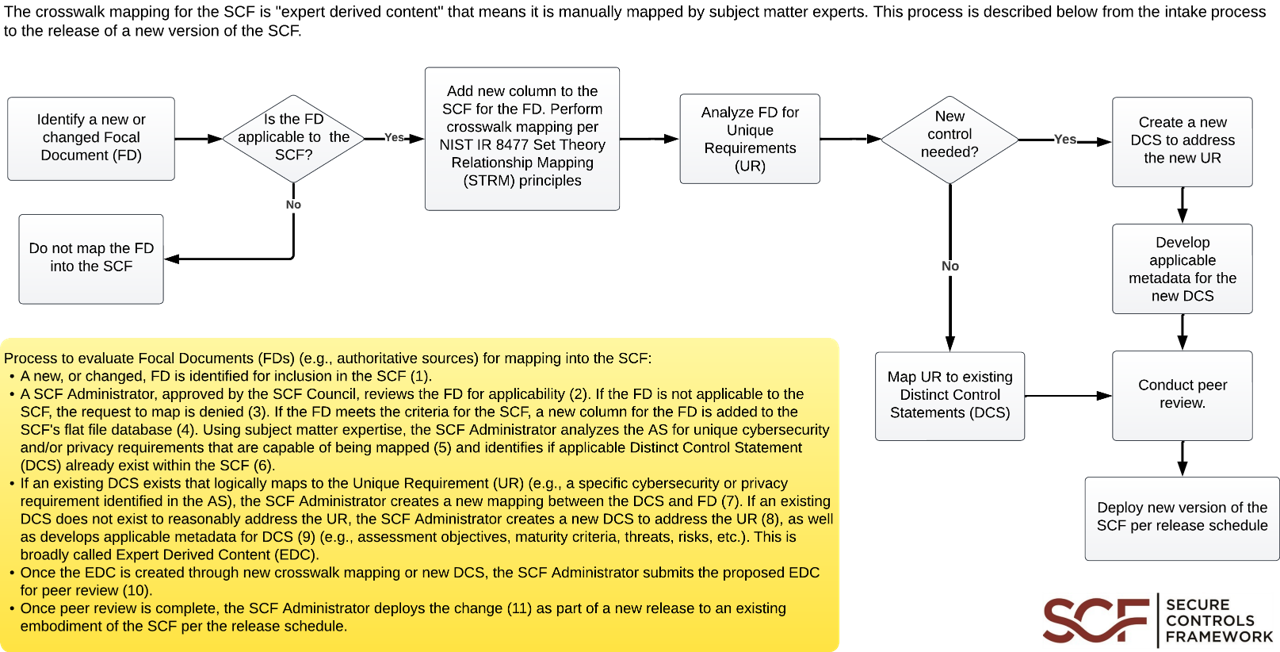
The crosswalk mapping for the SCF is "expert-derived content" which means it is manually mapped by subject matter experts. This process is described below from the intake process to the release of a new version of the SCF: