SCF Frequently Asked Questions (FAQ)
What Is The SCF?
The SCF stands for the Secure Controls Framework. It is more than just an assortment of cybersecurity and data privacy controls, since it is focused on designing, implementing and maintaining SECURE solutions to address all applicable statutory, regulatory and contractual requirements that an organization faces. Our belief is that if you scope your requirements with security in mind, compliance will generally be a natural byproduct of those actions. We want organizations to be both secure and compliant!
How Do I Use The SCF?
You can start in one of two ways:
- Download the Excel version of the SCF here and create your own set of controls from the complete listing of SCF controls; or
- Use a GRC tool, such as SCF Connect or others listed on the SCF Marketplace.
Realistically, pour yourself a cup of coffee (or your favorite beverage) and read through the SCF to get an understanding for its overall layout and what it contains. Being an Excel spreadsheet, you can do wonders with sorting out what is applicable to you. We even wrote a "start here guide" to help you understand the possibilities with the SCF.
What happens if you get stuck and don't know how to tailor the SCF or what steps you need to take to operationalize it? We have thought of that and we have a resource where you can find a SCF Practitioner - specialists within the cybersecurity and privacy fields who you can contract with. We give away the SCF for free, but if you want to get a consultant to walk you through setting up or operationalizing your control set, you will have to pay for a consultant to assist and that is outside of the scope of what this website offers.
How Often Is The SCF Updated?
The general cadence for updates is one (1) update per quarter. There may be situations where out-of-cycle updates are released, but the goal is to publish updates on a quarterly basis.
Why Is the SCF Free To Use?
Quite simply, the SCF is free to help fix the broken nature of cybersecurity and privacy practices in many organizations. We cannot rely on politicians to fix anything, so it is up to us to provide solutions.
The quality of the SCF could easily justify a costly subscription service, but we know that would exclude most organizations and defeat our broader goal of improving cybersecurity and privacy practices on a macro scale. While our contributors are volunteers, we rely on our generous sponsors to maintain the SCF.
Are There Restrictions On The Use of the SCF?
The Secure Controls Framework is copyrighted material, but we leverage the Creative Commons licensing model to keep it free for businesses to use. Please see the Terms & Conditions page for more details on this where you will see the open license that is granted for organizations to freely the use of the SCF.
Why Does The SCF Say It Is The Common Controls Framework?
The use of Common Controls Framework™ is trademarked and the SCF has exclusive rights to say the SCF is the Common Controls Framework™. Additionally, the domains common-controls-framework.com and commoncontrolsframework.com point to the SCF.
What Does "Mechanisms Exist" Mean?
We wrote the controls to be flexible to meet the needs of organizations, regardless of the size or industry. As you might imagine, that can make wording a challenge. Given that, you will see text within the controls, such as "Mechanisms exist to..." and if you do not like the term mechanism, you can replace that with "solution," "processes," or some other term of your preference.
However, the term "mechanism" can mean a manual process, technology solution, outsourced contract or a combination of those that come together to address the needs of the control. Some smaller companies may lack technology solutions for many controls, so manual processes will likely prevail. However, getting into Fortune 500 environments, technology solutions will most often exist to address the controls.
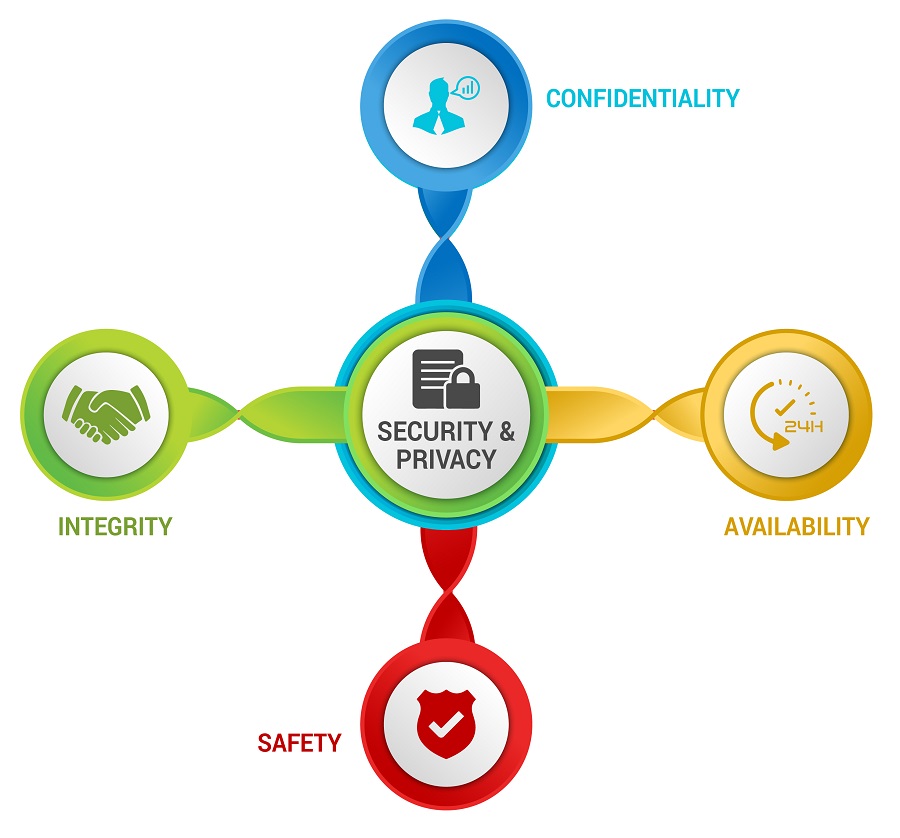
What The CIAS Model and Why Should It Replace The "CIA Triad"?
With the rise of Artificial Intelligence (AI) and autonomous technologies, the traditional Confidentiality, Integrity & Availability "CIA Triad" is insufficient to address the needs of a modern, digital cybersecurity and privacy program due to its avoidance of a safety component. The CIA Triad does not adequately represent a digital world with embedded technologies (e.g., Internet of Things (IoT) and Operational Technology (OT)) and AI-powered capabilities. The security of systems, applications and services must include controls to offset possible threats, as well as controls to ensure Confidentiality, Integrity, Availability and Safety (CIAS):
- CONFIDENTIALITY – This addresses preserving authorized restrictions on access and disclosure to authorized users and services, including means for protecting personal privacy and proprietary information.
- INTEGRITY – This addresses protecting against improper modification or destruction, including ensuring non-repudiation and authenticity.
- AVAILABILITY – This addresses timely, reliable access to data, systems and services for authorized users, services and processes.
- SAFETY – This addresses reducing risk associated with technologies that could fail or be manipulated by nefarious actors to cause death, injury, illness, damage to or loss of equipment.
If your organization utilizes IoT/OT devices and/or is utilizing (or planning to) AI and autonomous technologies, risk management discussions should include considerations for how the technology could be used for nefarious purposes or how safety could be jeopardized from emergent behaviors:
- Device Tampering: Can this technology lead to harm? (e.g., turn off a pacemaker; too much/too little drug dispensing; open/close physical access; etc.)
- Cyber Stalking: Can this technology lead to real-world stalking risks? (e.g., geolocation; travel patterns; recent contacts; etc.)
- Physical Damage: Can this technology lead to real-world physical damage (e.g., Aurora Generator Test) that could lead to physical harm?
- Cyber Warfare: Can this technology be weaponized by a nation state to support military or intelligence-gathering gains?
- Terrorism: Can this technology be weaponized by terrorists?
What Is Cybersecurity For Privacy by Design (C4P)?
Cybersecurity For Privacy by Design (C4P) is simply the concept of designing, implementing and maintaining the appropriate cybersecurity controls that address the confidentiality and integrity side of data privacy concerns with Personal Information (PI).
Surprising to many people, data privacy protections overlay most existing security protection mechanisms. In a C4P model, the focus is on People, Processes and Technology (PPT) to:
- Enable privacy.
- Preset security configuration settings so that they are secure by default.
- "Bake in” security mechanisms, as compared to “bolt on” protections as an afterthought.
- Value keeping things simple to save resources and avoid negatively affecting users.
- Integrate throughout the lifecycle of projects / applications / systems.
- Support a common method to “trust but verify” projects / applications / systems.
- Set security up to be seen as an enabler through educating users, managing expectations, and supporting change.