Security & Privacy Capability Maturity Model (SP-CMM) Use Case #1 – Objective Criteria To Build A Cybersecurity & Privacy Program
Posted by SCF Council on Apr 19th 2023
The Secure Controls Framework (SCF) release 2023.2 contains completely new content for its Security & Privacy Capability Maturity Model (SP-CMM). This effort was conducted to help streamline and standardize maturity criteria. One of the use cases for the SP-CMM is to provide a CISO with objective criteria to build a cybersecurity and privacy program. This is objective criteria that can be used to establish expectations for a cybersecurity & privacy program.
SP-CMM Use Case #1 – Objective Criteria To Build A Cybersecurity & Privacy Program
Identifying a target maturity state is intended to support your organization’s mission and strategy so without first understanding the broader mission of the organization and having prioritized objectives, a CISO/CIO/CPO will be guessing when it comes to establishing expectations for capability maturity. Like anything in life, if you fail to plan you plan to fail - CMM rollouts are no exception.
The time to execute a business plan to mature a cybersecurity and privacy program generally spans several years, where certain capabilities are prioritized over other capabilities. This means the CISO/CIO/CPO will establish CMM targets that evolve each year, based on prioritization. In the graphic below, the use of a spider chart can be beneficial to identify current vs future gaps with the SP-CMM. Prioritization of capability maturities may be based on risk assessments, audits, compliance obligations or management direction.
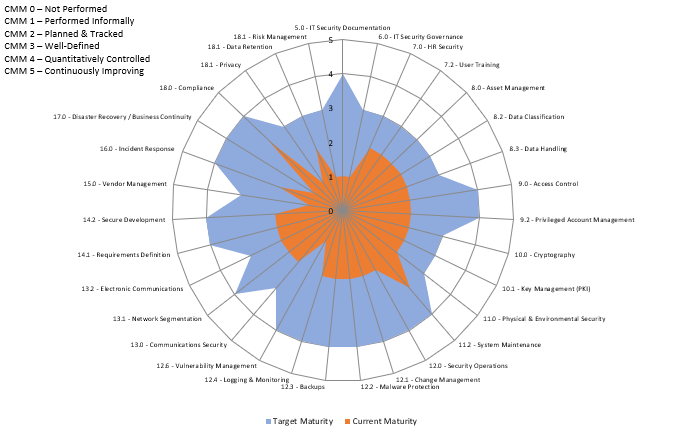
Identifying The Problem
Using a CMM helps organizations avoid “moving targets” for expectations. Maturity goals define “what right looks like” in terms of the required people, processes and technology that are expected to exist in order to execute controls at the individual contributor level. Without maturity goals, it is very difficult and subjective to define success for a security & privacy program.
All too often, unprincipled cybersecurity & privacy leaders manipulate the business through Fear, Uncertainty and Doubt (FUD) to scare other technology and business leaders into supporting cybersecurity initiatives. These bad actors maintain the illusion of a strong cybersecurity & privacy program, when in reality the department is an array of disjointed capabilities that lacks a unifying plan. These individuals stay in the job long enough to claim small victories, implement some cool technology, and then jump ship for larger roles in other organizations to extend their path of disorder. In these cases, a common theme is the lack of viable business planning beyond a shopping list of technologies and headcount targets to further their career goals.
Considerations
Cybersecurity & privacy departments are a cost center, not a revenue-generating business function. That means cybersecurity & privacy compete with all other departments for budget, and it necessitates a compelling business case to justify needed technology and staffing. Business leaders are getting smarter on the topic of cybersecurity & privacy, so these leaders need to rise above the FUD mentality and deliver value that is commensurate with the needs of the business.
When identifying a target level of maturity, it is crucial to account for your organization’s culture. The reason for this is the implementation of perceived “draconian” levels of security can cause a revolt in organizations not accustomed to heavy restrictions. One good rule of thumb when deciding between L3 and L4 targets is this simple question: “Do you want to be in an environment that is in control or do you want to be in a controlled environment?” L3 maturity is generally considered “an environment that is in control” where it is well-managed, whereas being in a L4 environment is more of a “controlled environment” that is more controlled and less free. Given those considerations, environments not used to heavy restrictions may want to target L3 as the highest-level of maturity targets. Additionally, the cost to mature from a L3-4 or L4-5 could be hundreds of thousands to millions of dollars, so there is a very real cost associated with picking a target maturity level. This is again where having management support is crucial to success, since this is ultimately a management decision.
From a CISO/CIO/CPO perspective, identifying a target level of maturity is also very beneficial in obtaining budget and protecting their professional reputation. In cases where business leadership doesn’t support reaching the proposed target level of maturity, the CISO/CIO/CPO at least has documentation to prove he/she demonstrated a defined resourcing need (e.g., CMM level to support a business need) and the request was denied. Essentially, this can help cover a CISO/CIO/CPO in case an incident occurs and blame is pointed. That is just the reality of life for anyone in a high-visibility leadership position and being able to deflect unwarranted criticism is professional reputation insurance.
Identifying A Solution
Defining a target maturity state is Step 4 in the Integrated Controls Management (ICM) model is a free resource from the SCF. That guide can be useful, since it helps establish two key pre-requisites to identifying CMM targets:
- Prioritization of efforts (including resourcing); and
- Identification of applicable statutory, regulatory and contractual obligations.
The most efficient manner we can recommend would be to first look at the thirty-two domains that make up the SCF and assign a high-level CMM level target for each domain. These domains are well-summarized in the SCF’s free Security & Privacy by Design Principles (SIP) document and can be used by a CISO/CIO/CPO to quickly align a maturity target to each domain, in accordance with previously-established prioritization and business needs.

