SCF Premium Content - Procedures Template
ComplianceForge is an authorized SCF partner and offers its Cybersecurity Standardized Operating Procedures (CSOP) as an enterprise-class solution for SCF-based procedures that augments the Digital Security Program (DSP)'s SCF-based policies, control objectives, standards, guidelines and metrics! The CSOP is a one-time purchases with no software to install - you are buying content in the form of Microsoft Office-based documentation templates that you can edit for your specific needs. If you can use Microsoft Office or OpenOffice, you can use the CSOP! While the CSOP does come in Microsoft Word, it comes also comes in Excel format, so it is easy to import into a GRC/IRM solution that supports CSV imports (e.g., SCF Connect).
The CSOP and its corresponding Digital Security Program (DSP), come together to provide "premium GRC content" that enables an organization to establish or refresh its GRC practices. For each SCF control, there is a corresponding procedures in the CSOP.
Cybersecurity & Privacy Procedures Templates
Organizations are often not at a loss for a set of policies, but executing those requirements often fall short due to several reasons. Standardized Operating Procedures (SOPs) are where the rubber meets the road for Individual Contributors (ICs), since these key players need to know:
- How they fit into day-to-day operations;
- What their priorities are; and
- What is expected from them in their duties.
When looking at it from an auditability perspective, the evidence of due diligence and due care should match what the organization's cybersecurity business plan is attempting to achieve. One of the most important things to keep in mind with procedures is that the "ownership" is different than that of policies and standards:
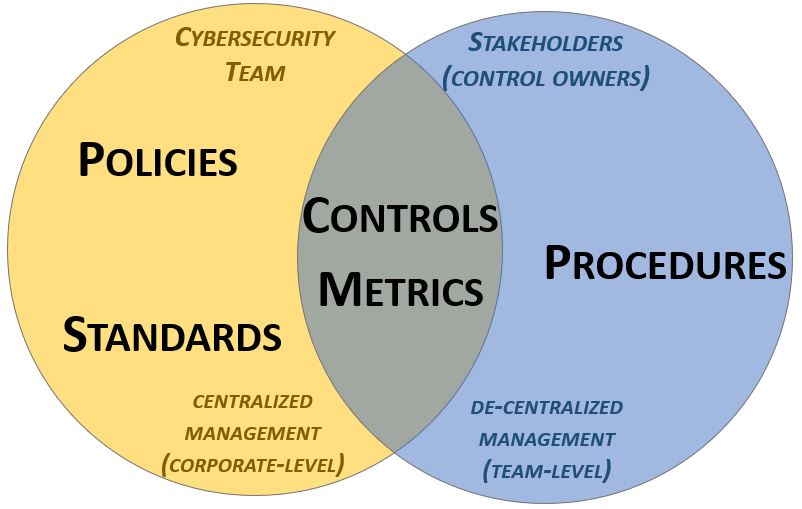
- Policies, standards and controls are designed to be centrally-managed at the corporate level (e.g., governance, risk & compliance team, CISO, etc.).
- Controls are assigned to stakeholders, based on applicable statutory, regulatory and contractual obligations.
- Procedures are by their very nature de-centralized, where control implementation at the team-level is defined to explain how the control is addressed (e.g., network team, desktop support, HR, procurement, etc.).
Given this approach to how documentation is structured, based on "ownership" of the documentation components:
- Policies, standards and controls are expected to be published for anyone within the organization to have access to, since it applies organization-wide. This may be centrally-managed by a GRC/IRM platform or published as a PDF on a file share, since they are relatively static with infrequent changes.
- Procedures are "living documents" that require frequent updates based on changes to technologies and staffing. Procedures are often documented in "team share" repositories, such as a wiki, SharePoint page, workflow management tool, etc.
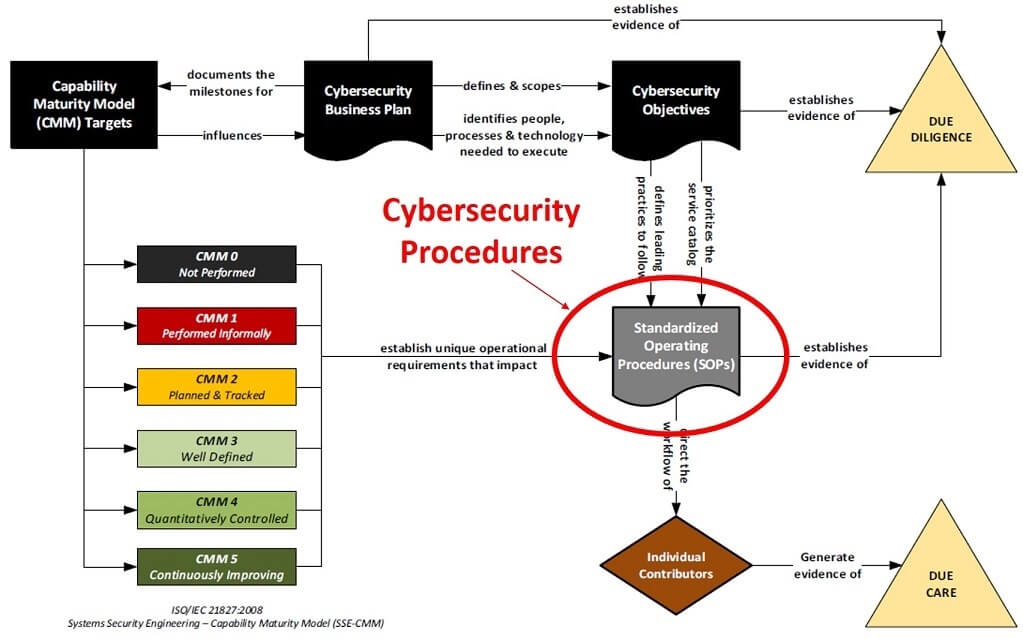
The central focus of any procedures should be a Capability Maturity Model (CMM) target that provides quantifiable expectations for People, Processes and Technologies (PPT), since this helps prevent a “moving target” by establishing an attainable expectation for “what right looks like” in terms of PPT. Generally, cybersecurity business plans take a phased, multi-year approach to meet these CMM-based cybersecurity objectives. Those objectives, in conjunction with the business plan, demonstrate evidence of due diligence on behalf of the CISO and his/her leadership team. The objectives prioritize the organization’s service catalog through influencing procedures at the IC-level for how PPT are implemented at the tactical level. SOPs not only direct the workflow of staff personnel, but the output from those procedures provides evidence of due care.
The diagram below helps show the critical nature of documented cybersecurity procedures in keeping an organization both secure and compliant:
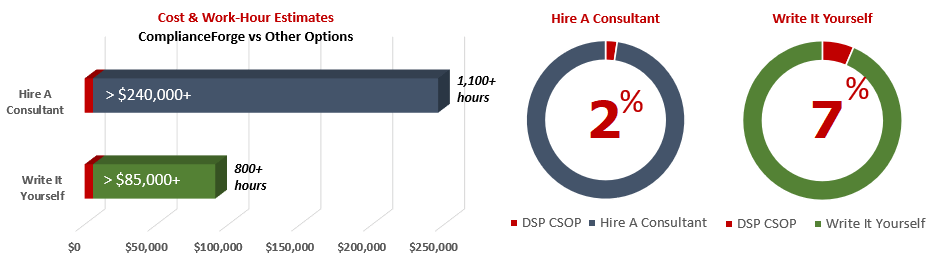
Cost Savings Estimate - Cybersecurity Standardized Operating Procedures (CSOP)
When you look at the costs associated with either (1) hiring an external consultant to write cybersecurity documentation for you or (2) tasking your internal staff to write it, the cost comparisons paint a clear picture that buying from ComplianceForge is the logical option. Compared to hiring a consultant, you can save months of wait time and tens of thousands of dollars. Whereas, compared to writing your own documentation, you can potentially save hundreds of work hours and the associated cost of lost productivity. Purchasing the DSP CSOP from ComplianceForge offers these fundamental advantages when compared to the other options for obtaining quality cybersecurity documentation:
- For your internal staff to generate comparable documentation, it would take them an estimated 1,200 internal staff work hours, which equates to a cost of approximately $85,000 in staff-related expenses. This is about 9-18 months of development time where your staff would be diverted from other work.
- If you hire a consultant to generate this documentation, it would take them an estimated 800 consultant work hours, which equates to a cost of approximately $240,000. This is about 6-12 months of development time for a contractor to provide you with the deliverable.
- The DSP CSOP is approximately 2% of the cost for a consultant or 7% of the cost of your internal staff to generate equivalent documentation.
- We process most orders the same business day so you can potentially start working with the DSP CSOP the same day you place your order.
The process of writing cybersecurity documentation can take an internal team many months and it involves pulling your most senior and experienced cybersecurity experts away from operational duties to assist in the process, which is generally not the most efficient use of their time. In addition to the immense cost of hiring a cybersecurity consultant at $300/hr+ to write this documentation for you, the time to schedule a consultant, provide guidance and get the deliverable product can take months. Even when you bring in a consultant, this also requires involvement from your internal team for quality control and answering questions, so the impact is not limited to just the consultant's time being consumed.

