SCF Certification - Conformity Assessment Program (CAP)
The Secure Controls Framework Conformity Assessment Program (SCF CAP) is an organization-level conformity assessment. The SCF CAP is designed to utilize tailored cybersecurity and privacy controls that specifically address the applicable statutory, regulatory and contractual obligations an Organization Seeking Assessment (OSA) is required to comply with. By using the metaframework nature of the SCF, an OSA is able to perform conformity assessment that spans multiple cybersecurity and privacy-specific laws, regulations and frameworks.
Earning a SCF Certified™ conformity designation is meant to signify an accomplishment, rather than be viewed as a “participation ribbon” that has little practical value for the OSA or stakeholders in the OSA’s supply chain to understand the OSA’s security posture.
The SCF CAP is focused on using the SCF as the control set to provide a company-level certification. While the SCF-CAP shares some similarities with other existing, single-focused certifications (e.g., ISO 27001, CMMC, FedRAMP, etc.), the SCF CAP is unique in its metaframework approach to covering cybersecurity and data protection requirements that span multiple laws, regulations and frameworks
SCF Certified - Third-Party Validation of SCF Control Conformity
Regardless of the industry, there is a definitive need for a third-party verified certification that assesses tailored cybersecurity and privacy controls that could impact the OSA and its supply chain stakeholders. The SCF CAP was designed to deliver an organization-level certification that is industry-recognized, earned through a qualified third-party assessor’s review of supporting evidence of a control’s effectiveness.
As cybersecurity and data protection operations are multi-faceted, the SCF CAP is designed to ensure that assessed controls reflect the real-world requirements faced by the OSA from a statutory, regulatory and contractual perspective. An assessment that only covers a part of an OSA’s cybersecurity and privacy program results in an inaccurate and incomplete report on the OSC’s overall security posture, providing a false sense of security to the OSA.
The SCF CAP is designed for cybersecurity & privacy practitioners by cybersecurity & data privacy practitioners. This concept is based on the need within the industry for a tailored conformity assessment solution that is capable of addressing several key considerations:
- View compliance as a natural by-product of secure practices;
- Scale to address multifaceted operational requirements (e.g., laws, regulations and frameworks);
- Acknowledge the stated risk tolerance of the OSC since not all organizations have the same risk tolerance;
- Minimize the risk of “gaming” the certification process that provides no useful insights into the security posture of the OSA;
- Utilize technology to make the assessment process more efficient to drive down labor-related assessment costs; and
- Leverage existing industry recognized practices, where possible.
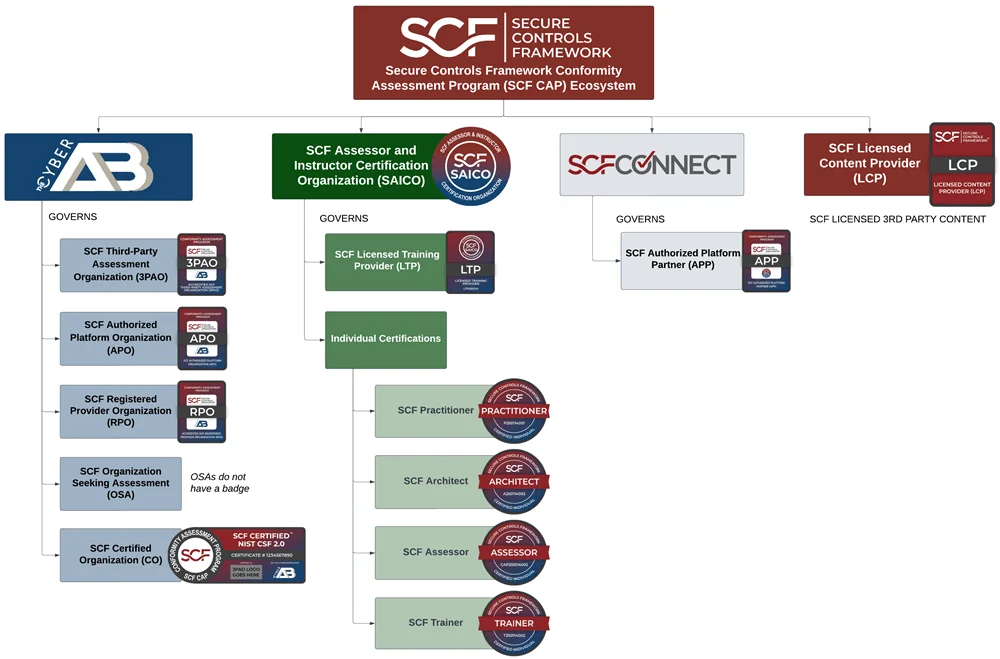
SCF CAP Ecosystem
There are several key players in the "SCF CAP Ecosystem" that are worth highlighting. If you click on the image, you can download a PDF with more information on the various components that make up the SCF CAP Ecosystem.
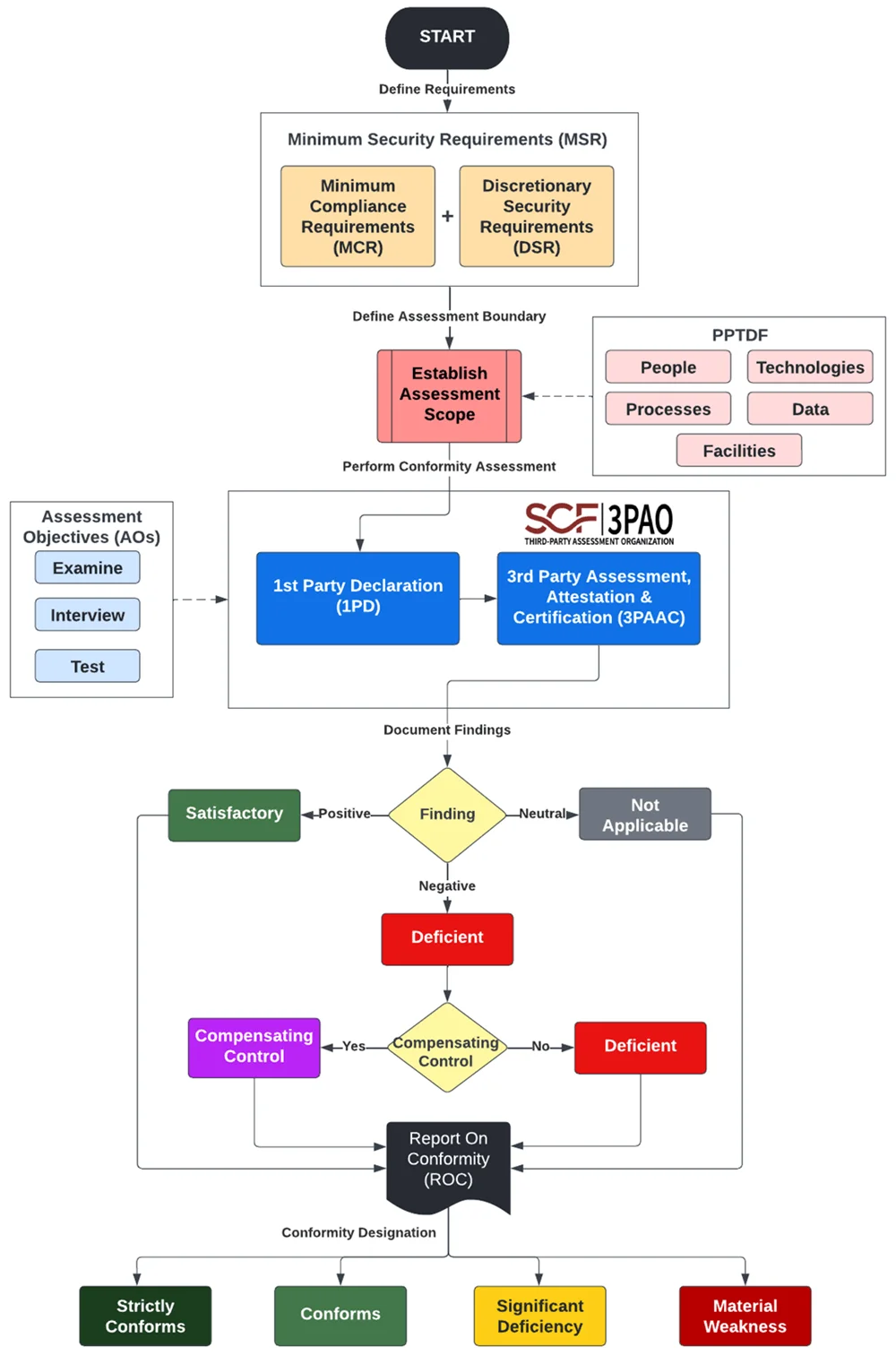
High Level Assessment Process Flow
The flow chart below provides a very high level processes flow for how a SCF CAP assessment is structured.