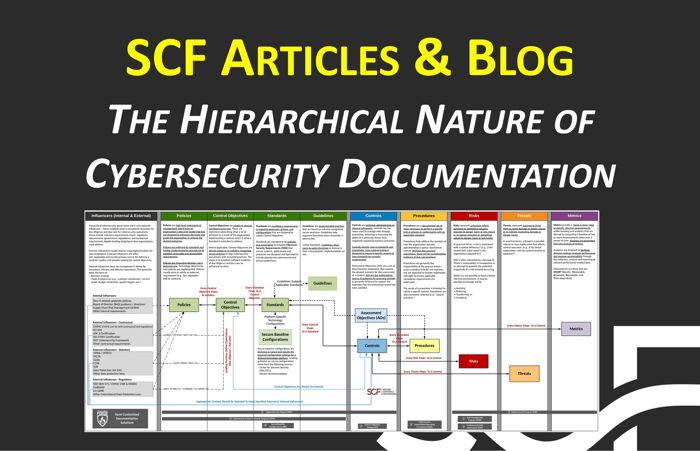
The Hierarchical Nature of Cybersecurity Documentation
ComplianceForge | Controls | cybersecurity compliance | cybersecurity controls | data privacy controls | Policies | Procedures | Standards
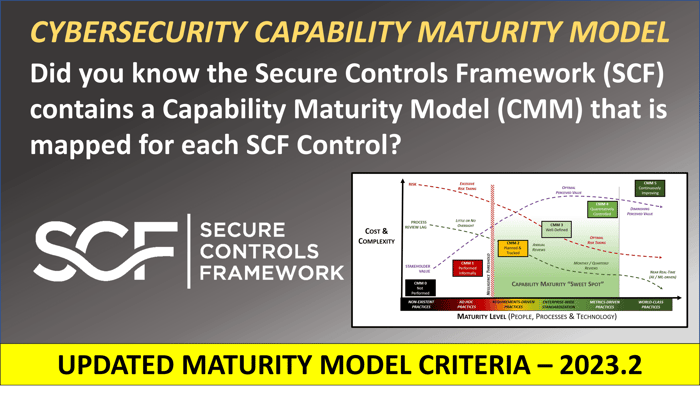
Updated Security & Privacy Capability Maturity Model (SP-CMM)
Capability Maturity Model | CMM | Cybersecurity Maturity | Maturity Model | SCF | SP-CMM

SCF 2023.2
CMMC | Maturity Model | NIST 800-171 | NNPI | SCF | Secure Controls Framework | SOC 2 | SP-CMM | TSC | UK CAF
Security & Privacy Capability Maturity Model (SP-CMM) Use Case #1 – Objective Criteria To Build A Cybersecurity & Privacy Program
Cybersecurity Maturity | Maturity Model | SCF | Security & Privacy Capability Maturity Model | SP-CMM
Security & Privacy Capability Maturity Model (SP-CMM) Use Case #4 – Due Diligence In Mergers & Acquisitions (M&A)
cybersecurity assessments | cybersecurity audit | cybersecurity due diligence | due diligence | M&A | Mergers & Acquisitions | SCF

Security & Privacy Capability Maturity Model (SP-CMM) Use Case #3 – Provide Objective Criteria To Evaluate Third-Party Service Provider Security
C-SCRM | SCF | SCRM | Supply Chain Risk Management | Third Party Cybersecurity Controls | Third-Party Risk Management
Security & Privacy Capability Maturity Model (SP-CMM) Use Case #2 – Assist Project Teams To Appropriately Plan & Budget Secure Practices
Cybersecurity Maturity | Maturity Model | Project Cybersecurity Criteria | SCF | SDLC | SP-CMM

SCFConnect - SaaS approach to using the SCF
GRC | SCF | scf cap | SCFConnect
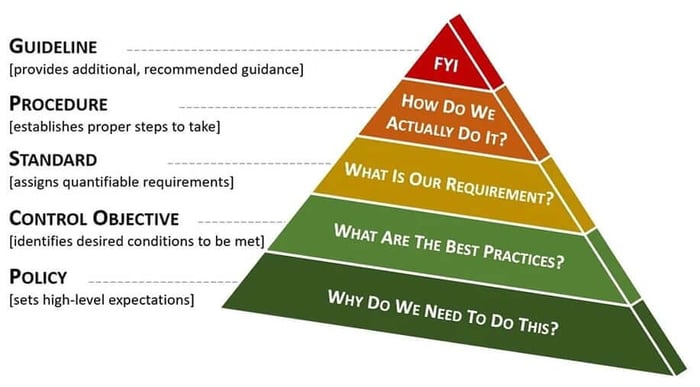
Words Matter - Understanding Policies, Control Objectives, Standards, Guidelines & Procedures
Compliance | Control Objectives | Controls | Governance | GRC | Guidelines | Policies | Procedures | Risk | SCF | Secure Controls Framework | Standards
