The Hierarchical Nature of Cybersecurity Documentation
Posted by SCF Council on Jan 16th 2024
In the dynamic landscape of cybersecurity, where the stakes are high and threats are ever-evolving, the importance of meticulous documentation cannot be overstated. What often goes unnoticed is the hierarchical structure that underpins cybersecurity and data protection documentation. This article explores the layered nature of these documents, illuminating how a well-organized hierarchy is fundamental to the effectiveness of cybersecurity practices.
Benefits of a Hierarchical Approach To Cybersecurity & Data Privacy Documentation:
- Clarity and Consistency: A well-organized, hierarchical structure brings clarity to the complex landscape of cybersecurity and data privacy documentation. It ensures that every document has a defined role and place in the overarching structure, reducing confusion and enhancing consistency in implementation.
- Scalability and Adaptability: The hierarchical nature allows for scalability, enabling organizations to expand their documentation as their cybersecurity and data protection needs evolve. It also facilitates adaptability, allowing for updates and adjustments without disrupting the entire framework.
- Efficient Auditing and Assessments: Auditors and assessors benefit from a hierarchical structure as it streamlines the review process. The layered approach allows for a systematic evaluation of policies, standards, procedures, and other documentation, making audits more efficient and effective.
- Effective Communication: Each layer in the hierarchy serves as a communication tool. Policies communicate high-level objectives to stakeholders, while procedures and guidelines provide practical instructions. This ensures that cybersecurity information is communicated effectively across different levels of the organization.
Bringing It All Together
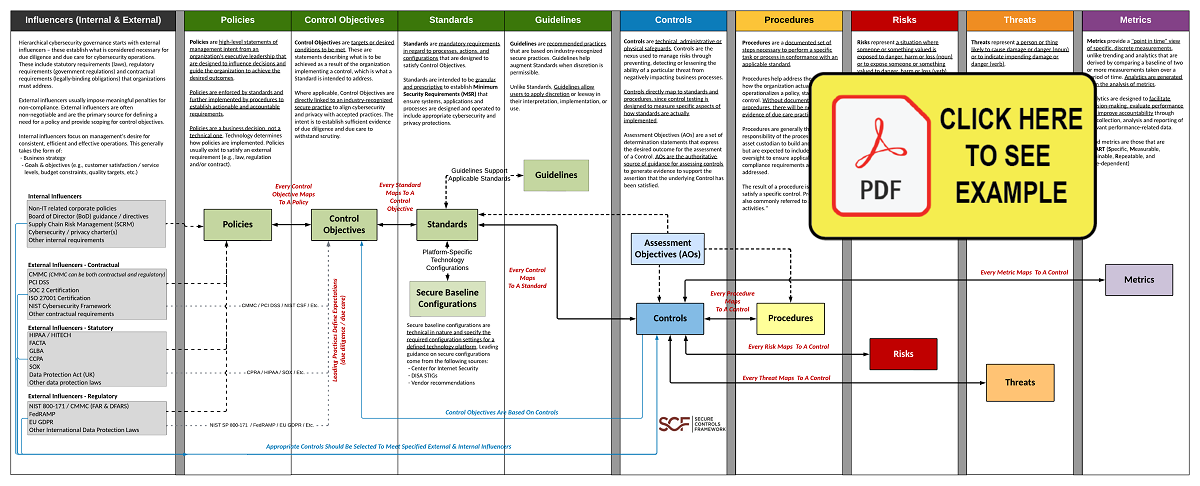
ComplianceForge developed a Hierarchical Cybersecurity Governance Framework (HCGF) that is a masterclass in the concept of the hierarchical nature of cybersecurity and data protection documentation. It is a must read for cybersecurity and data privacy practitioners:
Policy Structure: The Foundation
At the base of the cybersecurity documentation pyramid lies the policy structure. This foundational layer encompasses high-level documents that articulate an organization's overarching approach to cybersecurity and data protection. Policies outline the principles, goals, and high-level statements of management intent that govern the organization's cybersecurity posture. Policies serve as the north star, guiding the creation of more granular documentation.
Standards: Translating Policies into Actionable Requirements
Above policies sit standards, which provide more specific and actionable requirements derived from the overarching policies. Standards define the detailed requirements and best practices necessary to implement the policies effectively. They act as a bridge between the strategic vision outlined in policies and the tactical execution required at the operational level.
Guidelines: Tailoring for Specific Scenarios
Situated at a more flexible level, guidelines provide additional context and recommendations for specific scenarios. While policies, standards, and procedures offer a structured framework, guidelines offer adaptability. They empower cybersecurity practitioners to apply their expertise and judgment when faced with unique or evolving situations.
Procedures: Operationalizing Standards
The next layer in the hierarchy comprises procedures, which serve as the operational backbone of cybersecurity on a day-to-day or Business As Usual (BAU) basis. Procedures break down the standards into step-by-step instructions, detailing how specific tasks or processes should be carried out. These documents are instrumental in ensuring consistency and repeatability in security practices.
Technology-Specific Baselines: Configuring Security Controls
At the top of the hierarchy are technology-specific baselines, which define the specific configurations and settings required for various security controls that are vendor/platform-specific. Technology-specific baselines ensure that systems, applications, and devices are configured in alignment with industry-recognized secure practices (e.g., DISA STIGs, CIS Benchmarks, OEM vendor recommendations, etc.). They play a crucial role in minimizing vulnerabilities and maintaining a consistent security posture.
In this complex and ever-evolving realm of cybersecurity and data protection, the hierarchical nature of documentation is a linchpin for success. From establishing high-level policies to configuring specific security controls, each layer plays a vital role in fortifying an organization's defenses. As threats and risks continue to evolve, a well-organized hierarchy ensures that documentation remains not just a compliance checkbox, but a dynamic and adaptive tool in the ongoing battle for information security.