SCF Premium Content - Policies & Standards Template
ComplianceForge is an authorized SCF partner and offers its Digital Security Program (DSP) as an enterprise-class solution for SCF-based policies, standards, guidelines, metrics and more! The DSP is a one-time purchases with no software to install - you are buying content in the form of Microsoft Office-based documentation templates that you can edit for your specific needs. If you can use Microsoft Office or OpenOffice, you can use the DSP! While the DSP does come in Microsoft Word, it comes also comes in Excel format, so it is importable into a GRC solution that supports CSV imports (e.g., SCF Connect).
The DSP and its corresponding Cybersecurity Operating Procedures (CSOP), come together to provide "premium GRC content" that enables an organization to establish or refresh its GRC practices. The DSP consists of the thirty-three (33) SCF domains that defines a modern, digital security program (encompassing both cybersecurity and privacy considerations).
- For each SCF domain, there is a corresponding policy in the DSP.
- For each SCF control, there is a corresponding standard in the DSP.
Nested within the DSP's policies are the control objectives, standards, guidelines and metrics enable governance of your cybersecurity & privacy program. The DSP was developed to meet the need for growing organizations that want to avoid being locked into alignment with a single framework or have complex compliance requirements that span multiple frameworks. This SCF-based approach is a "best in class" hybrid framework structure that provides you with the ability to align with multiple frameworks in an efficient and scalable manner.
Cybersecurity & Privacy Policies, Standards, Controls & Metrics For A Digital Company - Hierarchical & Scalable!
ComplianceForge provides organizations with exactly what they need to protect themselves - professionally-written and editable cybersecurity policies, control objectives, standards, controls, procedures and guidelines at a very affordable cost. The DSP can be found in medium and large organizations that range from Fortune 500 companies, to US and international government agencies, universities and other organizations that have complex compliance requirements and need an efficient, scalable solution for their Governance, Risk & Compliance (GRC) needs.
- The DSP is footnoted to provide authoritative references for the statutory, regulatory and contractual requirements that need to be addressed. Just as Human Resources publishes an “employee handbook” to let employees know what is expected for employees from a HR perspective, the DSP does this from a cybersecurity perspective.
- The Cybersecurity Operating Procedures (CSOP) is available that provides mapped procedures to the DSP's standards. This is a 1-1 mapping with a procedure for each standard.
The structure of the Digital Security Program is scalable to make it is easy to add or remove policy sections, as your business needs change. The same concept applies to standards – you can simply add/remove content to meet your specific needs. The DSP addresses the “why?” and “what?” questions, since policies and standards form the foundation for your cybersecurity program. The following two documents shown below are well worth the time to make a pot of coffee and read through, since you will be able to understand both the structure of the documentation and how you can customize it for your specific needs.
The DSP is our recommended solution if you are currently using or plan to use a Governance, Risk & Compliance (GRC) or Integrated Risk Management (IRM) solution. The DSP is ready to import into your GRC/IRM instance, since it comes in both Microsoft Word and Excel formats. This makes the import from Excel straightforward and that allows you to then do you any customization and collaboration directly from your GRC portal.
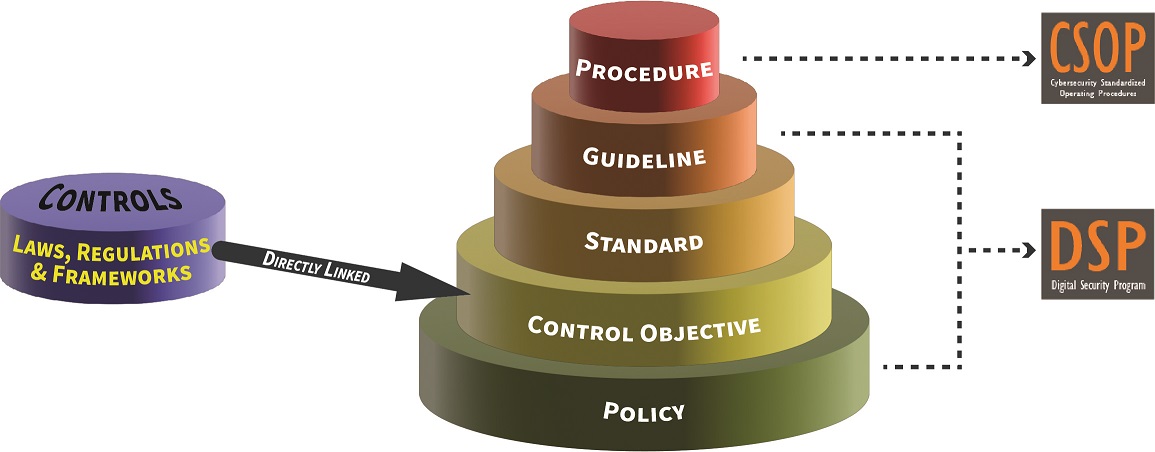
The ComplianceForge Reference Model (Hierarchical Cybersecurity Governance Framework) provides level setting on how the various types of documentation support each other (including the role of the SCF's controls). This provides insights into the definitions used, since there is a tendency within the industry to abuse definitions around policy, standard, procedure, etc. This is the hierarchical structure we follow to build our content so it is scalable and based on industry practices.
The DSP's policies & standards have direct, 1-1 mapping to the SCF's controls. The DSP leverages several key SCF components to provide “more than just policies & standards” by incorporating maturity criteria, a threat catalog, a risk catalog and more! The DSP provides invaluable content to operationalize several of the SCF's notable capabilities:
- Security & Privacy (S|P) Principles
- Privacy Management Principles (PMP)
- Security & Privacy Capability Maturity Model (SP-CMM)
- Security & Privacy Risk Management Model (SP-RMM)
- Premium Governance, Risk Management & Compliance (GRC) Content
Understanding "How To GRC" With The Digital Security Program (DSP) & Secure Controls Framework (SCF)
ComplianceForge, in conjunction with the SCF, literally wrote the book on "how to GRC" by establishing the Integrated Controls Management (ICM) that is a principle-based approach to Governance, Risk & Compliance (GRC) operations. The ICM Overview document (shown below) is a great starting place to understand how the DSP can help your organization to designing, implementing and managing a security and privacy program that incorporates requirements to be both secure and compliant. This approach leverages the "Deming Cycle" of Plan, Do, Check and Act (PDCA) for continuous improvement.
Understanding the requirements for both cybersecurity and privacy principles involves a simple process of distilling expectations. This process is all part of documenting reasonable expectations that are “right-sized” for an organization, since every organization has unique requirements. The approach looks at the following spheres of influence to identify applicable controls:
- Statutory - these are US state, federal and international laws.
- Regulatory - these are requirements from regulatory bodies or governmental agencies.
- Contractual - these are requirements that are stipulated in contracts, vendor agreements, etc.
- Industry-Recognized Practices - these are requirements that are based on an organization’s specific industry, where "industry norms" are established for what constitutes reasonable practices.
There are eight (8) principles associated with ICM that are fully-supported by the DSP to develop, implement and maintain a secure and compliant security and privacy program:
- Establish Context
- Define Applicable Controls
- Assign Maturity-Based Criteria
- Publish Policies, Standards & Procedures
- Assign Stakeholder Accountability
- Maintain Situational Awareness
- Manage Risk
- Evolve Processes
Cost Savings Estimate For The Digital Security Program (DSP) - A Fraction Of The Time & Expense
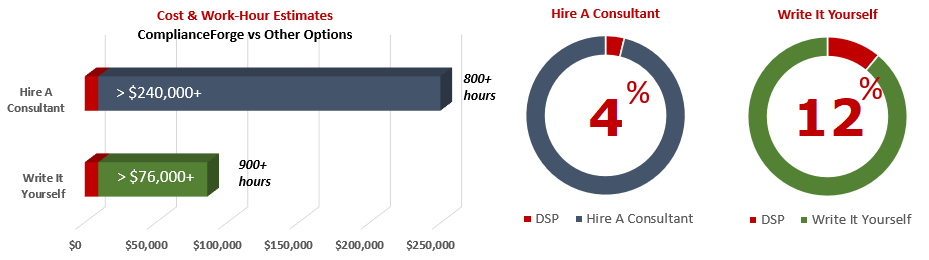
When you look at the costs associated with either (1) hiring an external consultant to write cybersecurity documentation for you or (2) tasking your internal staff to write it, the cost comparisons paint a clear picture that buying from ComplianceForge is the logical option. Compared to hiring a consultant, you can save months of wait time and tens of thousands of dollars. Whereas, compared to writing your own documentation, you can potentially save hundreds of work hours and the associated cost of lost productivity. Purchasing the DSP from ComplianceForge offers these fundamental advantages when compared to the other options for obtaining quality cybersecurity documentation:
- For your internal staff to generate comparable documentation, it would take them an estimated 900 internal staff work hours, which equates to a cost of approximately $76,000 in staff-related expenses. This is about 12-24 months of development time where your staff would be diverted from other work.
- If you hire a consultant to generate this documentation, it would take them an estimated 800 consultant work hours, which equates to a cost of approximately $240,000. This is about 6-12 months of development time for a contractor to provide you with the deliverable.
- The DSP is approximately 4% of the cost for a consultant or 12% of the cost of your internal staff to generate equivalent documentation.
- We process most orders the same business day so you can potentially start working with the DSP the same day you place your order.
The process of writing cybersecurity documentation can take an internal team many months and it involves pulling your most senior and experienced cybersecurity experts away from operational duties to assist in the process, which is generally not the most efficient use of their time. In addition to the immense cost of hiring a cybersecurity consultant at $300/hr+ to write this documentation for you, the time to schedule a consultant, provide guidance and get the deliverable product can take months. Even when you bring in a consultant, this also requires involvement from your internal team for quality control and answering questions, so the impact is not limited to just the consultant's time being consumed.