Integrated Controls Management (ICM) Model
The Integrated Controls Management (ICM) model is defined as, “a holistic, technology-agnostic approach to cybersecurity and data protection controls to identify, implement and manage secure and compliant practices, covering an organization’s people, processes, technology and data, regardless of how or where data is stored, processed and/or transmitted.”
ICM is designed to proactively address the strategic, operational and tactical nature of operating an organization’s cybersecurity & data privacy program at the control level. ICM is designed to address both internal controls, as well as the broader concept of Cybersecurity Supply Chain Risk Management (C-SCRM).
The ICM Is A "How To GRC" Playbook
|
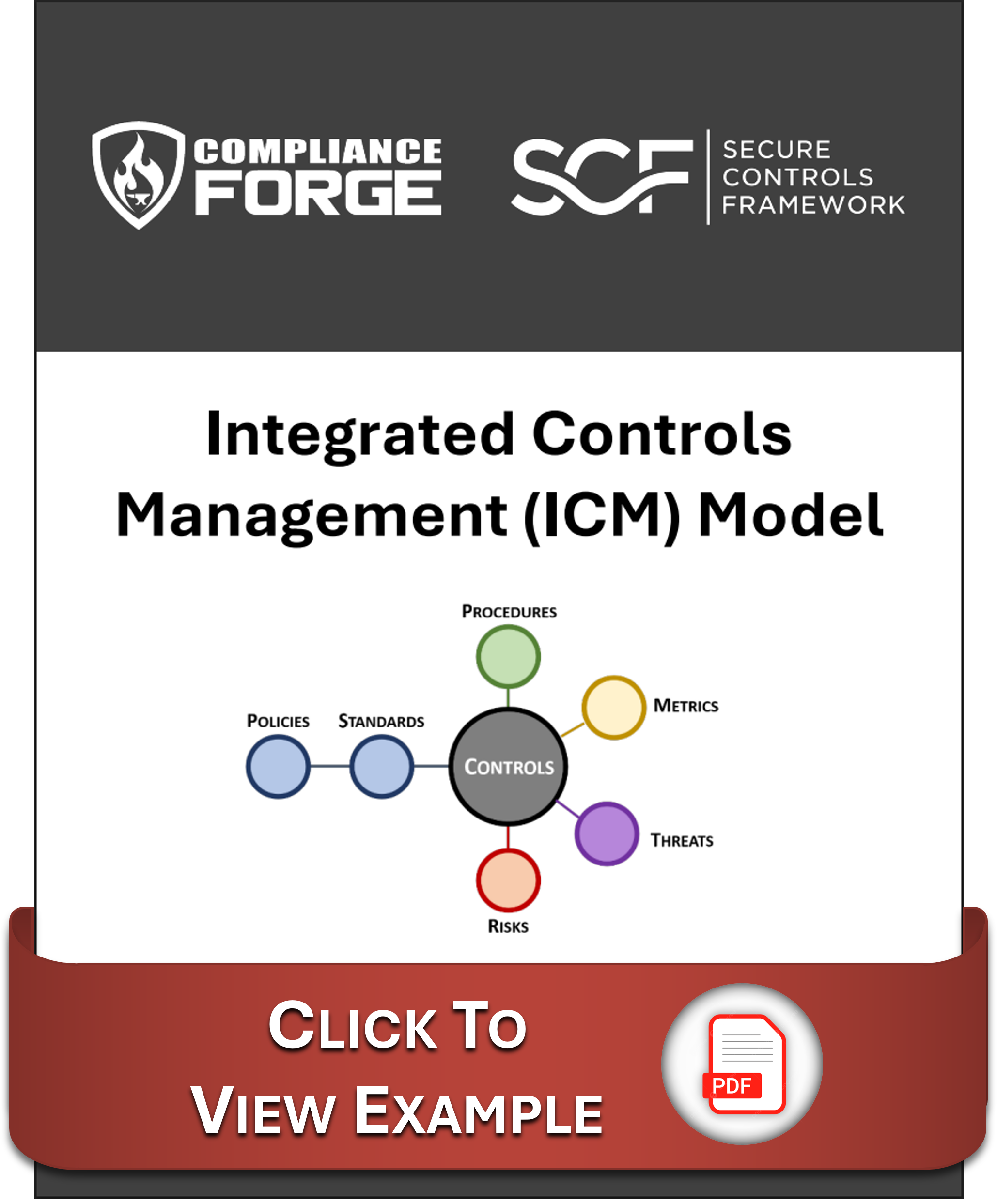
The premise of ICM is that controls are central to cybersecurity & data privacy operations, as well as the overall business rhythm of an organization. This premise is supported by the Cybersecurity & Data Privacy Risk Management Model (C|P-RMM), that describes the central nature of controls, where not just policies and standards map to controls, but procedures, metrics, threats and risks, as well. ICM takes a different approach from the traditional definition of Governance, Risk Management and Compliance (GRC) and/or Integrated Risk Management (IRM), since ICM is controls-centric, where controls are viewed as the nexus, or central pivoting point, for an organization’s cybersecurity and data privacy operations. OCEG defines GRC as, “GRC is the integrated collection of capabilities that enable an organization to reliably achieve objectives, address uncertainty and act with integrity,” while Gartner jointly defines GRC/IRM as, "a set of practices and processes supported by a risk-aware culture and enabling technologies, that improves decision making and performance through an integrated view of how well an organization manages its unique set of risks." |
 |
ICM Defines What It Means To Be Both "Secure" and "Compliant"
Unlike GRC/IRM, ICM specifically focuses on the need to understand and clarify the difference between "compliant" versus "secure" since that is necessary to have coherent risk management discussions. To assist in this process, ICM helps an organization categorize its applicable controls according to “must have” vs “nice to have” requirements:
- Minimum Compliance Requirements (MCR) are the absolute minimum requirements that must be addressed to comply with applicable laws, regulations and contracts.
- Discretionary Security Requirements (DSR) are tied to the organization’s risk appetite since DSR are “above and beyond” MCR, where the organization self-identifies additional cybersecurity and data protection controls to address voluntary industry practices or internal requirements, such as findings from internal audits or risk assessments.
Secure and compliant operations exist when both MCR and DSR are implemented and properly governed:
- MCR are primarily externally-influenced, based on industry, government, state and local regulations. MCR should never imply adequacy for secure practices and data protection, since they are merely compliance-related.
- DSR are primarily internally-influenced, based on the organization’s respective industry and risk tolerance. While MCR establish the foundational floor that must be adhered to, DSR are where organizations often achieve improved efficiency, automation and enhanced security.
Plan, Do, Check & Act Approach To GRC
The ICM takes a comprehensive view towards governing a cybersecurity & data privacy program. Without an overarching concept of operations for the broader GRC/IRM function, organizations will often find that their governance, risk, compliance and privacy teams are siloed in how they think and operate. These siloed functions and unclear roles often stem from a lack of a strategic understanding of how these specific functions come together to build a symbiotic working relationship between the individual teams that enables quality control over people, processes and technology.
The ICM utilizes a Plan, Do, Check & Act (PDCA) approach that is a logical way to design a governance structure:
|
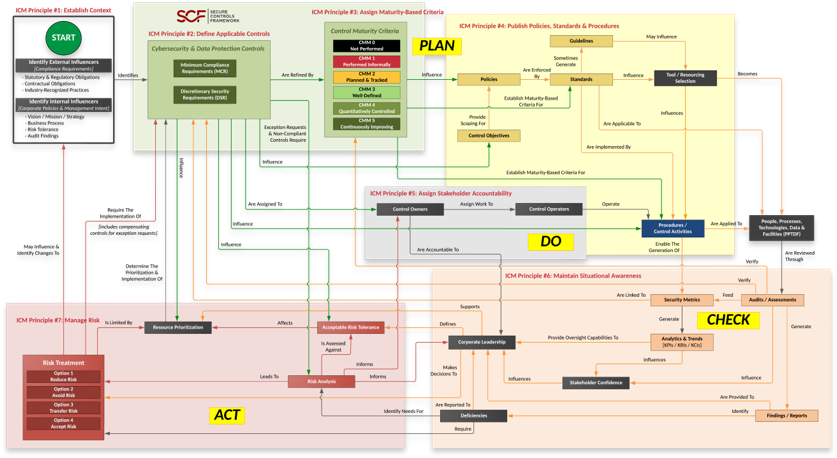 |
Integrated Controls Management (ICM) Principles
There are eight (8) principles associated with the ICM:
ICM Principle 1: Establish Context
To build and maintain efficient and effective operations, a cybersecurity & privacy program must have a hierarchical vision, mission and strategy that directly supports the organization’s broader strategic objectives and business processes. This process of establishing context involves identifying all applicable external compliance requirements (e.g., laws, regulations and contractual obligations), as well as internal directives (e.g., Board of Directors, corporate policies, etc.). This is a due diligence element of the cybersecurity & data privacy program.
ICM Principle 2: Define Applicable Controls
A tailored control set cybersecurity and data protection controls must exist. This control set needs to be made of Minimum Compliance Requirements (MCR) and Discretionary Security Requirements (DSR). This blend of “must have” and “nice to have” requirements establish an organization’s tailored control set to ensure both secure practices and compliance.
ICM Principle 3: Assign Maturity-Based Criteria
The cybersecurity & privacy program must assign maturity targets to define organization-specific “what right looks like” for controls. This establishes attainable criteria for people, processes and technology requirements. Tailored maturity level criteria can be used to plan for, budget for and assess against. Maturity targets should support the organization’s need for operational resiliency.
ICM Principle 4: Publish Policies, Standards & Procedures
Documentation must exist, otherwise an organization’s cybersecurity and data protection practices are unenforceable. Formalizing organization-specific requirements via policies and standards are necessary to operationalize controls. Stakeholders utilize those prescriptive requirements to develop Standardized Operating Procedures (SOP) that enable Individual Contributors (IC) to execute those controls. Policies, standards and procedures provides evidence of due diligence that the organization identified and implemented reasonable steps to address its applicable requirements.
ICM Principle 5: Assign Stakeholder Accountability
Controls must be assigned to stakeholders to ensure accountability (e.g., business units, teams and/or individuals). These “control owners” may assign the task of executing controls to “control operators” at the IC-level. The documented execution of procedures provides evidence of due care that reasonable practices are being performed.
ICM Principle 6: Maintain Situational Awareness
Situational awareness must involve more than merely “monitoring controls” (e.g., metrics). While metrics are a point-in-time snapshot into discrete controls’ performance, the broader view of metrics leads to a longer-term trend analysis. When properly tied in with current risk, threat and vulnerability information, this insight provides “situational awareness” that is necessary for organizational leadership to adjust plans to operate within the organization’s risk threshold.
ICM Principle 7: Manage Risk
Proactive risk management processes must exist across all phases of development/information/system life cycles to address confidentiality, integrity, availability and safety aspects. Risk management must address internal and external factors, including privacy and Supply Chain Risk Management (SCRM) considerations. To manage risk, it requires the organization to clearly define its risk threshold and risk management expectations.
ICM Principle 8: Evolve Processes
Cybersecurity and data protection measures must adapt and evolve to address business operations and the evolving threat landscape. This requires the adoption of a Plan, Do, Check & Act (PDCA) approach (Deming Cycle) to ensure the organization proactively identifies its requirements, implements appropriate protections, maintains situational awareness to detect incidents, operates a viable capability to respond to incidents and can sustain key business operations, if an incident occurs.
