NIST CSF 2.0 Assessment Guide
This NIST Cybersecurity Framework 2.0 (NIST CSF 2.0) assessment guide is designed for organizations that align with the cybersecurity governance framework established by NIST CSF 2.0. This is ideal for organizations that want to demonstrate conformity with NIST CSF 2.0 through a third-party assessment that results in a certification.
This and other SCF-based assessment guides can be downloaded here: https://securecontrolsframework.com/content/cap/ag-nist-csf-v-1-1.pdf
NIST CSF Assessment Methodology
Use of the NIST CSF is widespread and it is common to have a "NIST CSF assessment" performed to provide third-party objectivity. However, theSecure Controls Framework (SCF)has taken this concept of a NIST CSF assessment into an entirely different league of its own with this assessment guide that includes components like:
- Assessment Objectives (AOs).
- Evidence Request List (ERL).
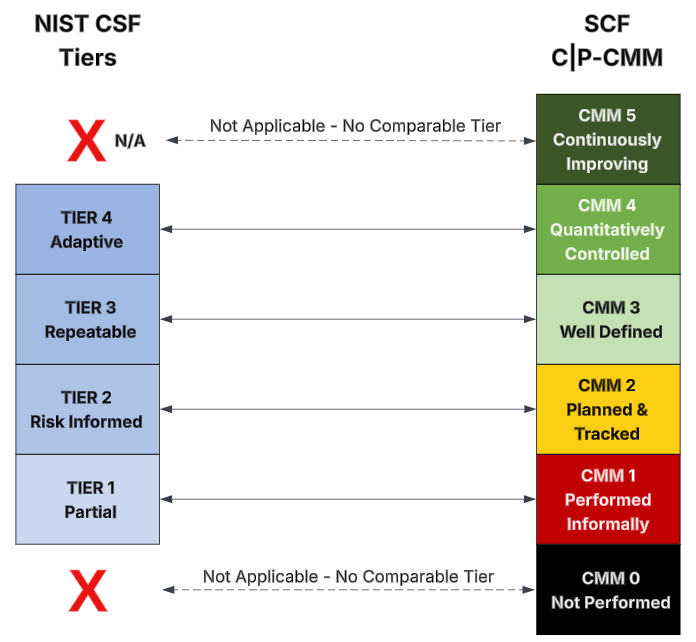
- Maturity model to provide guidance on "what looks right" for each control.
- Scoping guidance.
- Scoring criteria (Conforms, Significant Deficiency or Material Weakness).
Not only can this provide a methodology to perform an assessment, but it is possible to obtain a certification as "SCF Certified - NIST CSF 2.0" by going through a conformity assessment, governed byThe Cyber AB, the same organization that runs the Cybersecurity Maturity Model Certification (CMMC) for the US Department of Defense!