Security & Privacy Capability Maturity Model (SP-CMM) Use Case #2 – Assist Project Teams To Appropriately Plan & Budget Secure Practices
Posted by SCF Council on Apr 19th 2023
The Secure Controls Framework (SCF) release 2023.2 contains completely new content for its Security & Privacy Capability Maturity Model (SP-CMM). This effort was conducted to help streamline and standardize maturity criteria. One of the use cases for the SP-CMM is to provide objective criteria for project teams so that secure practices are appropriately planned and budgeted for.
SP-CMM Use Case #2 – Assist Project Teams To Appropriately Plan & Budget Secure Practices
When you consider regulations such as the EU General Data Protection Regulation (GDPR), there is an expectation for systems, applications and processes to identify and incorporate cybersecurity and privacy by default and by design. In order to determine what is appropriate and to evaluate it prior to “go live” it necessitates expectations for control maturity to be defined.
Identifying The Problem
In planning a project or initiative, it is important to establish “what right looks like” from security and privacy controls that must be implemented to address all compliance needs. This includes internal requirements, as well as external requirements from applicable laws, regulations and contracts. Prior planning of requirements can reduce delays and other costs associated with re-engineering.
Considerations
Referencing back to the SP-CMM Overview section of this document, L0-1 levels of maturity are identified as being deficient from a “reasonable person perspective” in most cases. Therefore, project teams need to look at the “capability maturity sweet spot” between L2-L4 to identify the reasonable people, processes and technologies that need to be incorporated into the solution.
As previously-covered, avoiding negligent behavior is a critical consideration. The most common constraints that impact a project’s maturity are: (1) budget and (2) time. A System Development Life Cycle (SDLC) has constraints and the expectations are that security and privacy controls are applied throughout the SDLC.
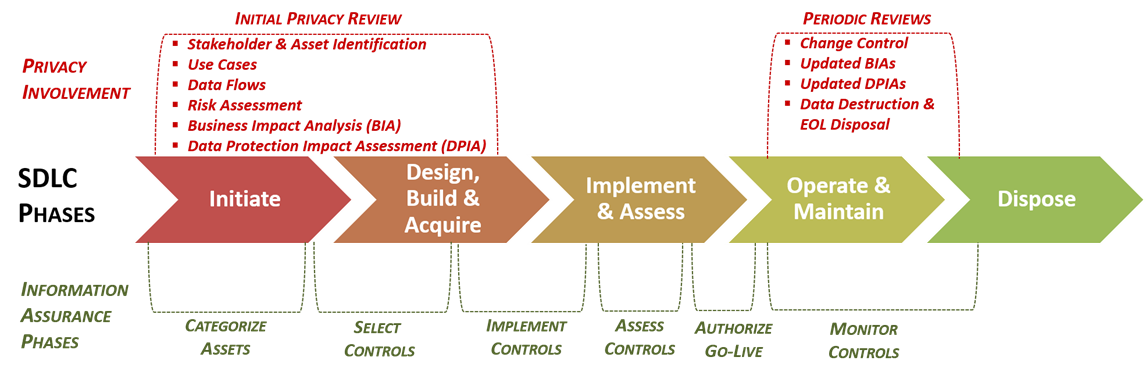
Projects do not have unlimited budgets, nor do they tend to have overly flexible timelines that allow for new security & privacy tools to be installed and trained upon. From a project perspective, this is often going to limit target CMM levels to L2-3 for planning purposes.
Identifying A Solution
While there are over 1,000 controls in the SCF’s controls catalog, it is necessary for a project team to pare down that catalog to only what is applicable to the project (e.g., ISO 27002, PCI DSS, CCPA, etc.). This step simply involves filtering out the controls in the SCF that are not applicable. This step can also be done within Excel or within a GRC solution (e.g., SCF Connect). In the end, the result is a tailored set of controls that meet the project’s specific needs.
Now that you have pared down the SCF’s controls catalog to only what is applicable, it is a manual review process to identify the appropriate level of maturity for each of the controls. Ideally, the project will inherit the same target maturity level for controls as used throughout the organization. For any deviations, based on budget, time or other constraints, a risk assessment should be conducted to ensure a lower level of maturity for project-specific controls is appropriate.

