Unified Scoping Guide (USG)
|
The Unified Scoping Guide (USG) is a free resource that is intended to help organizations define the scope of the sensitive data where it is stored, transmitted and/or processed. This guide will refer to both sensitive and regulated data as “sensitive data” to simplify the concept this document is focused on. This scoping guide categorizes system components according to several factors:
|
 |
Data-Centric Security Approach For Scoping Sensitive & Regulated Data
The Unified Scoping Guide (USG) is intended to help organizations define the scope of the sensitive data where it is stored, transmitted and/or processed. This guide will refer to both sensitive and regulated data as “sensitive data” to simplify the concept this document is focused on. This approach is applicable to the following sensitive data types:
- Controlled Unclassified Information (CUI)
- Personally Identifiable Information (PII)
- Cardholder Data (CHD)
- Attorney-Client Privilege Information (ACPI)
- Export-Controlled Data (ITAR / EAR)
- Federal Contract Information (FCI)
- Protected Health Information (PHI)
- Intellectual Property (IP)
- Student Educational Records (FERPA)
- Critical Infrastructure Information (CII)
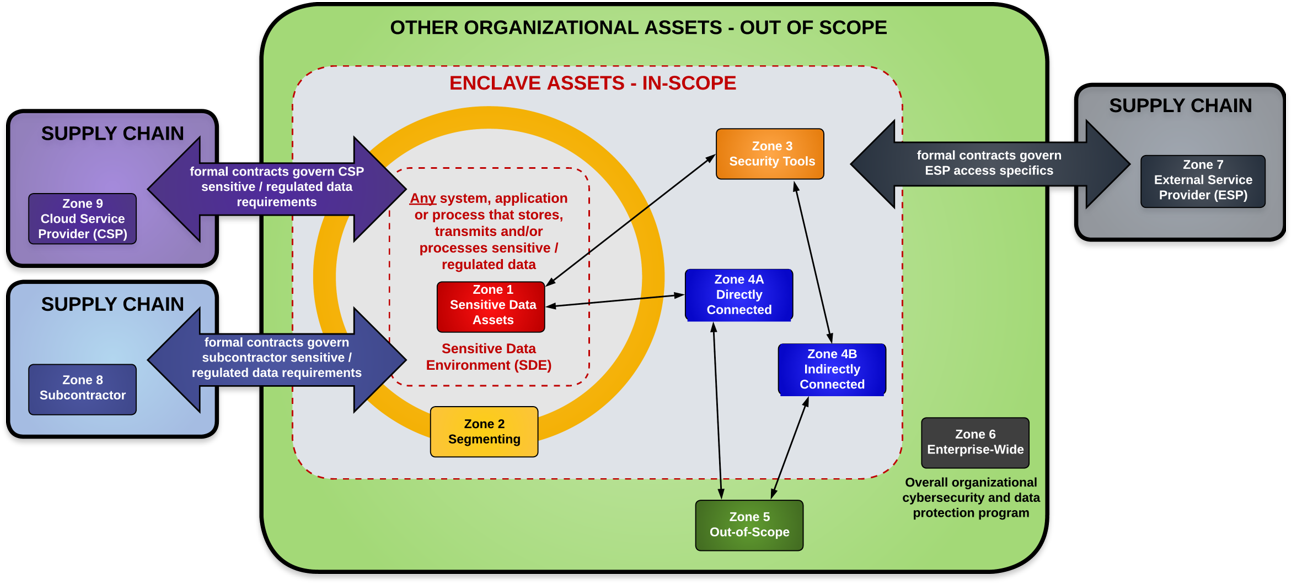
Zone-Based Approach To Implementing Data-Centric Security
When viewing scoping, there are nine (9) zones for sensitive data compliance purpose.
What This Guide Does Address
Identifying and addressing the people, processes and technologies around sensitive data is a necessary part of any cybersecurity and data protection (privacy) program. This guide focuses on categorizing the system components that comprise a company's computing environment and helps with the following:
- Assists in determining which system components fall in and out of scope.
- Facilitates constructive communication between your company and an assessor/regulator by providing a reasonable methodology to describe your technology infrastructure and sensitive data environment.
- Provides a means to categorize the various different types of assets, each with a different risk profile associated with it.
- Provides a starting point to potentially reduce the scope of sensitive data by re-architecting technologies to isolate and control access to the sensitive data environment.
This model categorizes system components according to several factors:
- Whether sensitive data is being stored, processed or transmitted;
- The functionality that the system component provides (e.g. access control, logging, antimalware, etc.); and
- The connectivity between the system and the Sensitive Data Environment (SDE).
What This Guide Does Not Address
This guide does not define which statutory, regulatory and/or contractual controls are required for each category (see Integrated Controls Management (ICM) model for defining control applicability). Since every organization is different, it is up to each organization and its assessor to determine the nature, extent and effectiveness of each control to adequately mitigate the risks to sensitive data.