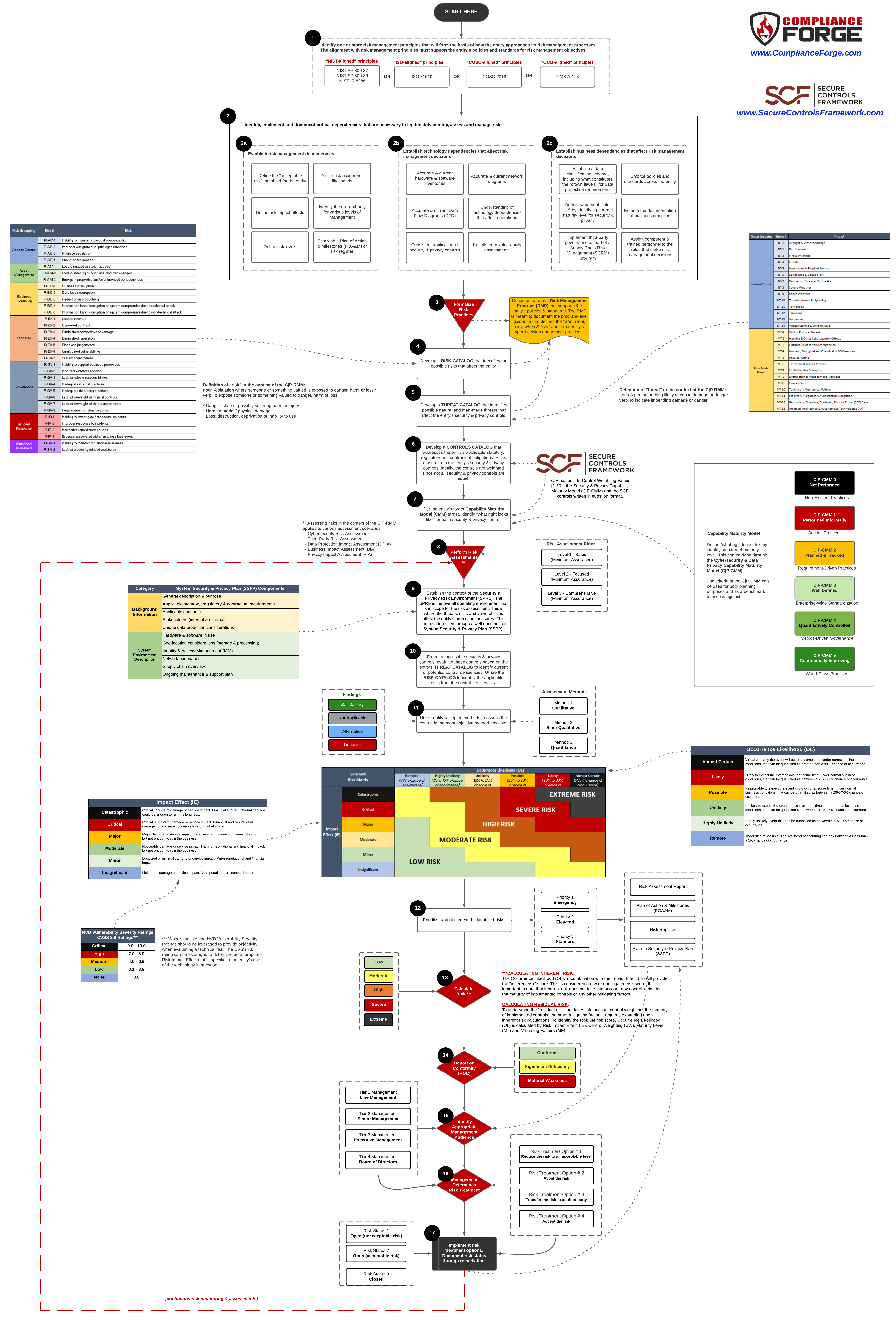
Cybersecurity & Data Privacy Risk Management Model (C|P-RMM)
Why You Should Care About The C|P-RMM
Ask yourself these two questions about your organization and your personal exposure in risk & threat management operations:
- Can you prove that the right people within your organization are both aware of risks and have taken direct responsibility for mitigating those risks?
- If there was a breach or incident that is due to identified risks that went unmitigated, where does the “finger pointing” for blame immediately go to? (Is it you? Would you have guilt by association?
Risks & Threats Do Not Exist In A Vacuum
It is vitally important to understand that risks and threats do not exist in a vacuum. If your cybersecurity and privacy program is appropriately built, you will have a robust controls framework where risks and threats will map directly to controls. Why is this?
- Controls are central to managing risks, threats, procedures and metrics; and
- Risks, threats, metrics and procedures need to map into the controls, which then map to standards and policies.
Instead of executive leadership hanging blame on the CIO or CISO, quality risk management documentation can prove that reasonable steps were taken to identify, assess, report and mitigate risk. This type of documentation can provide evidence of due diligence and due care on the part of the CIO/CISO/CRO, which firmly puts the responsibility back on the management of the team/department/line of business that “owns” the risk.
Based on the applicable statutory, regulatory and contractual obligations that impact the scope of a risk assessment, an organization is expected to have an applicable set of cybersecurity and privacy controls to cover those needs. That set of controls identifies the in-scope requirements that must be evaluated to determine what risk exists. This is generally considered to be a “gap assessment” where the assessor:
- Evaluates those controls based on the entity's THREAT CATALOG to identify current or potential control deficiencies; and
- Utilize the RISK CATALOG to identify the applicable risks, based on the identified control deficiencies.
Risks vs Threats vs Vulnerabilities
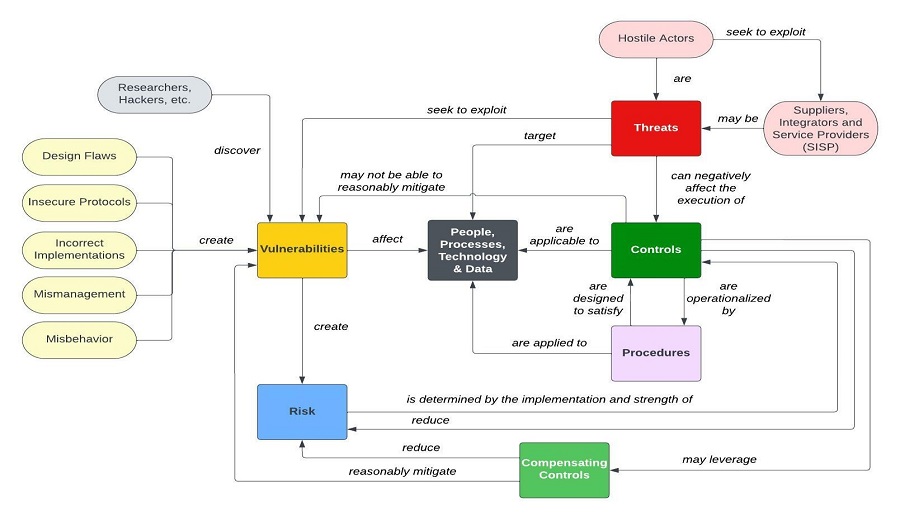
Risks, threats and vulnerabilities are commonly misunderstood. Fundamentally, vulnerability and risk management practices exist to achieve a minimum level of protection for an organization, which equates to a reduction in the total risk due to the protections offered by implemented controls. This can be conceptualized as a "risk management ecosystem" as it pertains to an organization's overall cybersecurity & data protection efforts. These ecosystem components have unique meanings that need to be understood to reasonably protect people, processes, technology and data, as shown below:
SCF Threat Catalog
The threat catalog use case is: What natural and man-made threats affect control execution? (e.g., if the threat materializes, will the control function as expected?)
This use case relies on the following definition of a threat:
- Noun - A person or thing likely to cause damage or danger.
- Verb - To indicate impending damage or danger.
| Threat Grouping | Threat # | Threat* | Threat Description |
| Natural Threat | NT-1 | Drought & Water Shortage | Regardless of geographic location, periods of reduced rainfall are expected. For non-agricultural industries, drought may not be impactful to operations until it reaches the extent of water rationing. |
| NT-2 | Earthquakes | Earthquakes are sudden rolling or shaking events caused by movement under the earth’s surface. Although earthquakes usually last less than one minute, the scope of devastation can be widespread and have long-lasting impact. | |
| NT-3 | Fire & Wildfires | Regardless of geographic location or even building material, fire is a concern for every business. When thinking of a fire in a building, envision a total loss to all technology hardware, including backup tapes, and all paper files being consumed in the fire. | |
| NT-4 | Floods | Flooding is the most common of natural hazards and requires an understanding of the local environment, including floodplains and the frequency of flooding events. Location of critical technologies should be considered (e.g., server room is in the basement or first floor of the facility). | |
| NT-5 | Hurricanes & Tropical Storms | Hurricanes and tropical storms are among the most powerful natural disasters because of their size and destructive potential. In addition to high winds, regional flooding and infrastructure damage should be considered when assessing hurricanes and tropical storms. | |
| NT-6 | Landslides & Debris Flow | Landslides occur throughout the world and can be caused by a variety of factors including earthquakes, storms, volcanic eruptions, fire, and by human modification of land. Landslides can occur quickly, often with little notice. Location of critical technologies should be considered (e.g., server room is in the basement or first floor of the facility). | |
| NT-7 | Pandemic (Disease) Outbreaks | Due to the wide variety of possible scenarios, consideration should be given both to the magnitude of what can reasonably happen during a pandemic outbreak (e.g., COVID-19, Influenza, SARS, Ebola, etc.) and what actions the business can be taken to help lessen the impact of a pandemic on operations. | |
| NT-8 | Severe Weather | Severe weather is a broad category of meteorological events that include events that range from damaging winds to hail. | |
| NT-9 | Space Weather | Space weather includes natural events in space that can affect the near-earth environment and satellites. Most commonly, this is associated with solar flares from the Sun, so an understanding of how solar flares may impact the business is of critical importance in assessing this threat. | |
| NT-10 | Thunderstorms & Lightning | Thunderstorms are most prevalent in the spring and summer months and generally occur during the afternoon and evening hours, but they can occur year-round and at all hours. Many hazardous weather events are associated with thunderstorms. Under the right conditions, rainfall from thunderstorms causes flash flooding and lightning is responsible for equipment damage, fires and fatalities. | |
| NT-11 | Tornadoes | Tornadoes occur in many parts of the world, including the US, Australia, Europe, Africa, Asia, and South America. Tornadoes can happen at any time of year and occur at any time of day or night, but most tornadoes occur between 4–9 p.m. Tornadoes (with winds up to about 300 mph) can destroy all but the best-built man-made structures. | |
| NT-12 | Tsunamis | All tsunamis are potentially dangerous, even though they may not damage every coastline they strike. A tsunami can strike anywhere along most of the US coastline. The most destructive tsunamis have occurred along the coasts of California, Oregon, Washington, Alaska and Hawaii. | |
| NT-13 | Volcanoes | While volcanoes are geographically fixed objects, volcanic fallout can have significant downwind impacts for thousands of miles. Far outside of the blast zone, volcanoes can significantly damage or degrade transportation systems and also cause electrical grids to fail. | |
| NT-14 | Winter Storms & Extreme Cold | Winter storms is a broad category of meteorological events that include events that range from ice storms, to heavy snowfall, to unseasonably (e.g., record breaking) cold temperatures. Winter storms can significantly impact business operations and transportation systems over a wide geographic region. | |
| Man-Made Threat | MT-1 | Civil or Political Unrest | Civil or political unrest can be singular or wide-spread events that can be unexpected and unpredictable. These events can occur anywhere, at any time. |
| MT-2 | Hacking & Other Cybersecurity Crimes | Unlike physical threats that prompt immediate action (e.g., "stop, drop, and roll" in the event of a fire), cyber incidents are often difficult to identify as the incident is occurring. Detection generally occurs after the incident has occurred, with the exception of "denial of service" attacks. The spectrum of cybersecurity risks is limitless and threats can have wide-ranging effects on the individual, organizational, geographic, and national levels. | |
| MT-3 | Hazardous Materials Emergencies | Hazardous materials emergencies are focused on accidental disasters that occur in industrialized nations. These incidents can range from industrial chemical spills to groundwater contamination. | |
| MT-4 | Nuclear, Biological and Chemical (NBC) Weapons | The use of NBC weapons are in the possible arsenals of international terrorists and it must be a consideration. Terrorist use of a “dirty bomb” — is considered far more likely than use of a traditional nuclear explosive device. This may be a combination a conventional explosive device with radioactive / chemical / biological material and be designed to scatter lethal and sub-lethal amounts of material over a wide area. | |
| MT-5 | Physical Crime | Physical crime includes "traditional" crimes of opportunity. These incidents can range from theft, to vandalism, riots, looting, arson and other forms of criminal activities. | |
| MT-6 | Terrorism & Armed Attacks | Armed attacks, regardless of the motivation of the attacker, can impact a businesses. Scenarios can range from single actors (e.g., "disgruntled" employee) all the way to a coordinated terrorist attack by multiple assailants. These incidents can range from the use of blade weapons (e.g., knives), blunt objects (e.g., clubs), to firearms and explosives. | |
| MT-7 | Utility Service Disruption | Utility service disruptions are focused on the sustained loss of electricity, Internet, natural gas, water, and/or sanitation services. These incidents can have a variety of causes but directly impact the fulfillment of utility services that your business needs to operate. | |
| MT-8 | Dysfunctional Management Practices | Dysfunctional management practices are a manmade threat that expose an organization to significant risk. The threat stems from the inability of weak, ineffective and/or incompetent management to (1) make a risk-based decision and (2) support that decision. The resulting risk manifests due (1) an absence of a required control or (2) a control deficiency. | |
| MT-9 | Human Error | Human error is a broad category that includes non-malicious actions that are unexpected and unpredictable by humans. These incidents can range from misconfigurations, to misunderstandings or other unintentional accidents. | |
| MT-10 | Technical / Mechanical Failure | Technical /mechanical failure is a broad category that includes non-malicious failure due to a defect in the technology, materials or workmanship. Technical / mechanical failures are unexpected and unpredictable, even when routine and preventative maintenance is performed. These incidents can range from malfunctions, to reliability concerns to catastrophic damage (including loss of life). | |
| MT-11 | Statutory / Regulatory / Contractual Obligation | Laws, regulations and/or contractual obligations that directly or indirectly weaken an organization's security & privacy controls. This includes hostile nation states that leverage statutory and/or regulatory means for economic or political espionage and/or cyberwarfare activities. | |
| MT-12 | Redundant, Obsolete/Outdated, Toxic or Trivial (ROT) Data | Redundant, Obsolete/Outdated, Toxic or Trivial (ROT) data is information an organization utilizes for business processes even though the data is untrustworthy, due to the data's currency, accuracy, integrity and/or applicability. | |
| MT-13 | Artificial Intelligence & Autonomous Technologies (AAT) | Artificial Intelligence & Autonomous Technologies (AAT) is a broad category that range from non-malicious failure due to a defect in the algorithm to emergent properties or unintended consequences. AAT failures can be due to hardware failures, inherent biases or other flaws in the underlying algorithm. These incidents can range from malfunctions, to reliability concerns to catastrophic damage (including loss of life). |
SCF Risk Catalog
The risk catalog use case is: What are the risks associated with a control deficiency? (e.g., if the control fails, what risk(s) is the organization exposed to?)
This use case relies on the following definition of a risk:
- Noun - A situation where someone or something valued is exposed to danger, harm or loss.**
- Verb - To expose someone or something valued to danger, harm or loss.
** Danger: state of possibly suffering harm or injury
** Harm: material / physical damage
** Loss: destruction, deprivation or inability to use
Note - Some of these risks may indicate a deficiency that could be considered a failure to meet "reasonable security practices"
| Risk Grouping | Risk # | Risk |
Description of Possible Risk Due To Control Deficiency IF THE CONTROL FAILS, RISK THAT THE ORGANIZATION IS EXPOSED TO IS: |
| Access Control | R-AC-1 | Inability to maintain individual accountability | The inability to maintain accountability (e.g., asset ownership, non-repudiation of actions or inactions, etc.). |
| R-AC-2 | Improper assignment of privileged functions | The inability to implement least privileges (e.g., Role-Based Access Control (RBAC), Privileged Account Management (PAM), etc.). | |
| R-AC-3 | Privilege escalation | The inability to restrict access to privileged functions. | |
| R-AC-4 | Unauthorized access | The inability to restrict access to only authorized individuals, groups or services. | |
| Asset Management | R-AM-1 | Lost, damaged or stolen asset(s) | Lost, damaged or stolen assets. |
| R-AM-2 | Loss of integrity through unauthorized changes | Unauthorized changes that corrupt the integrity of the system / application / service. | |
| R-AM-3 | Emergent properties and/or unintended consequences | Emergent properties and/or unintended consequences from Artificial Intelligence & Autonomous Technologies (AAT). | |
| Business Continuity | R-BC-1 | Business interruption | Increased latency, or a service outage, that negatively impact business operations. |
| R-BC-2 | Data loss / corruption | The inability to maintain the confidentiality of the data (compromise) or prevent data corruption (loss). | |
| R-BC-3 | Reduction in productivity | Diminished user productivity. | |
| R-BC-4 | Information loss / corruption or system compromise due to technical attack | A technical attack that compromises data, systems, applications or services (e.g., malware, phishing, hacking, etc.). | |
| R-BC-5 | Information loss / corruption or system compromise due to non-technical attack | A non-technical attack that compromises data, systems, applications or services (e.g., social engineering, sabotage, etc.). | |
| Exposure | R-EX-1 | Loss of revenue | A negatively impact on the ability to generate revenue (e.g., a loss of clients or an inability to generate future revenue). |
| R-EX-2 | Cancelled contract | A cancelled contract with a client or other entity for cause (e.g., failure to fulfill obligations for secure practices). | |
| R-EX-3 | Diminished competitive advantage | Diminished competitive advantage (e.g., lose market share, internal dysfunction, etc.). | |
| R-EX-4 | Diminished reputation | Diminished brand value (e.g., tarnished reputation). | |
| R-EX-5 | Fines and judgements | Financial damages due to fines and/or judgements from statutory / regulatory / contractual non-compliance. | |
| R-EX-6 | Unmitigated vulnerabilities | Unmitigated technical vulnerabilities that lack compensating controls or other mitigation actions. | |
| R-EX-7 | System compromise | A compromise of a system, application or service that affects confidentiality, integrity, availability and/or safety. | |
| Governance | R-GV-1 | Inability to support business processes | Insufficient cybersecurity and/or privacy practices that cannot securely support the organization's technologies & processes. |
| R-GV-2 | Incorrect controls scoping | Missing or incorrect cybersecurity and/or privacy controls due to incorrect or inadequate control scoping practices. | |
| R-GV-3 | Lack of roles & responsibilities | Insufficient cybersecurity and/or privacy roles & responsibilities that cannot securely support the organization's technologies & processes. | |
| R-GV-4 | Inadequate internal practices | Insufficient cybersecurity and/or privacy practices that can securely support the organization's technologies & processes. | |
| R-GV-5 | Inadequate third-party practices | Insufficient Cybersecurity Supply Chain Risk Management (C-SCRM) practices that cannot securely support the organization's technologies & processes. | |
| R-GV-6 | Lack of oversight of internal controls | The inability to demonstrate appropriate evidence of due diligence and due care in overseeing the organization's internal cybersecurity and/or privacy controls. | |
| R-GV-7 | Lack of oversight of third-party controls | The inability to demonstrate appropriate evidence of due diligence and due care in overseeing third-party cybersecurity and/or privacy controls. | |
| R-GV-8 | Illegal content or abusive action | Disruptive content or actions that negatively affect business operations (e.g., abusive content, harmful speech, threats of violence, illegal content, etc.). | |
| Incident Response | R-IR-1 | Inability to investigate / prosecute incidents | Insufficient incident response practices that prevent the organization from investigating and/or prosecuting incidents (e.g., chain of custody corruption, available sources of evidence, etc.). |
| R-IR-2 | Improper response to incidents | The inability to appropriately respond to incidents in a timely manner. | |
| R-IR-3 | Ineffective remediation actions | The inability to ensure incident response actions were correct and/or effective. | |
| R-IR-4 | Expense associated with managing a loss event | Financial repercussions from responding to an incident or loss. | |
| Situational Awareness | R-SA-1 | Inability to maintain situational awareness | The inability to detect cybersecurity and/or privacy incidents (e.g., a lack of situational awareness). |
| R-SA-2 | Lack of a security-minded workforce | The inability to appropriately educate and train personnel to foster a security-minded workforce. |
Risk Management: The Path To Hell Is Paved With Good Intentions
In risk management, the old adage is applicable that “the path to hell is paved with good intentions.” Often, risk management personnel are tasked with creating risk assessments and questions to ask without having a centralized set of organization-wide cybersecurity and privacy controls to work from. This generally leads to risk teams making up risks and asking questions that are not supported by the organization’s policies and standards. For example, an organization is an “ISO shop” that operates an ISO 27002-based Information Security Management System (ISMS) to govern its policies and standards, but its risk team is asking questions about NIST SP 800-53 or 800-171 controls that are not applicable to the organization.
This scenario of “making up risks” points to a few security program governance issues:
- If the need for additional controls to cover risks is legitimate, then the organization is improperly scoped and does not have the appropriate cybersecurity and privacy controls to address its applicable statutory, regulatory, contractual or industry-expected practices.
- If the organization is properly scoped, then the risk team is essentially making up requirements that are not supported by the organization’s policies and standards.
The C|P-RMM takes a holistic approach to controls, risks and threats as a way to reduce or eliminate the traditional Fear, Uncertainty and Doubt (FUD) that makes many risk assessments meaningless.
Risk Management Basics
The most important concept to understand in cybersecurity and privacy-related risk management is that the cybersecurity and IT departments generally do not “own” risk. The reality of the situation is that risk management is a business management decision, where the cybersecurity and privacy functions primarily serve as a mechanism to educate those business stakeholders on identified risks and provide possible risk treatment solutions. Right or wrong, business management is ultimately able to decide how risk is to be handled.
Where the Cybersecurity & Data Privacy Risk Management Model (C|P-RMM) exists is to help cybersecurity and privacy functions create a repeatable methodology to identify, assess, report and mitigate risk. This is based on the understanding that the responsibility to approve a risk treatment solution rests with the management of the team/department/line of business that “owns” the risk. The C|P-RMM is meant to guide the decision to one of these common risk treatment options:
- Reduce the risk to an acceptable level;
- Avoid the risk;
- Transfer the risk to another party; or
- Accept the risk
It is a common problem for individuals who are directly impacted by risk to simply say, “I accept the risk” and wish the risk away so that the project/initiative can proceed without having to first address deficiencies. This is why it is critically important that as part of a risk management program to identify the various levels of management who have the legitimate authority to make risk management decisions. This can help prevent low-level managers from recklessly accepting risk that should be reserved for more senior management.
Cybersecurity & Data Privacy Risk Management Model (C|P-RMM) - "Start To Finish" Steps
The C|P-RMM breaks risk management down to 16 steps. Please download the guide for the overview and you can click on the image below for a PDF version of the C|P-RMM infographic. The C|P-RMM breaks risk management down to 16 steps. Please download the guide for the overview and you can click on the image below for a PDF version of the C|P-RMM infographic. The C|P-RMM provides a clear method to calculate both inherent and residual risk. Please download the guide for the overview and you can click on the image below for a PDF version of the C|P-RMM infographic.