SCF Licensed Content Provider (LCP)
A SCF Licensed Content Provider (LCP) is authorized by the SCF Council, LLC to sell derivative works of the SCF (e.g., SCF-based policies, standards, procedures, etc.). Only a SCF LCP is authorized to provide SCF-based derivative content.
ComplianceForge
ComplianceForge is a SCF LCP and sells cybersecurity and data protection policies, standards, procedures and other documentation solutions based on the SCF.

ComplianceForge's SCF-based policies, standards and procedures can save an organization a significant amount of money from the labor-related costs to research, write and refine cybersecurity documentation. ComplianceForge's SCF-based documentation can also be obtained the same day you purchase it, so the time savings is immense:
- Decreased implementation costs (e.g., having to research and write policies, standards and procedures); and
- Increased speed of implementation and adoption, since you have have the documentation the same day you order it.
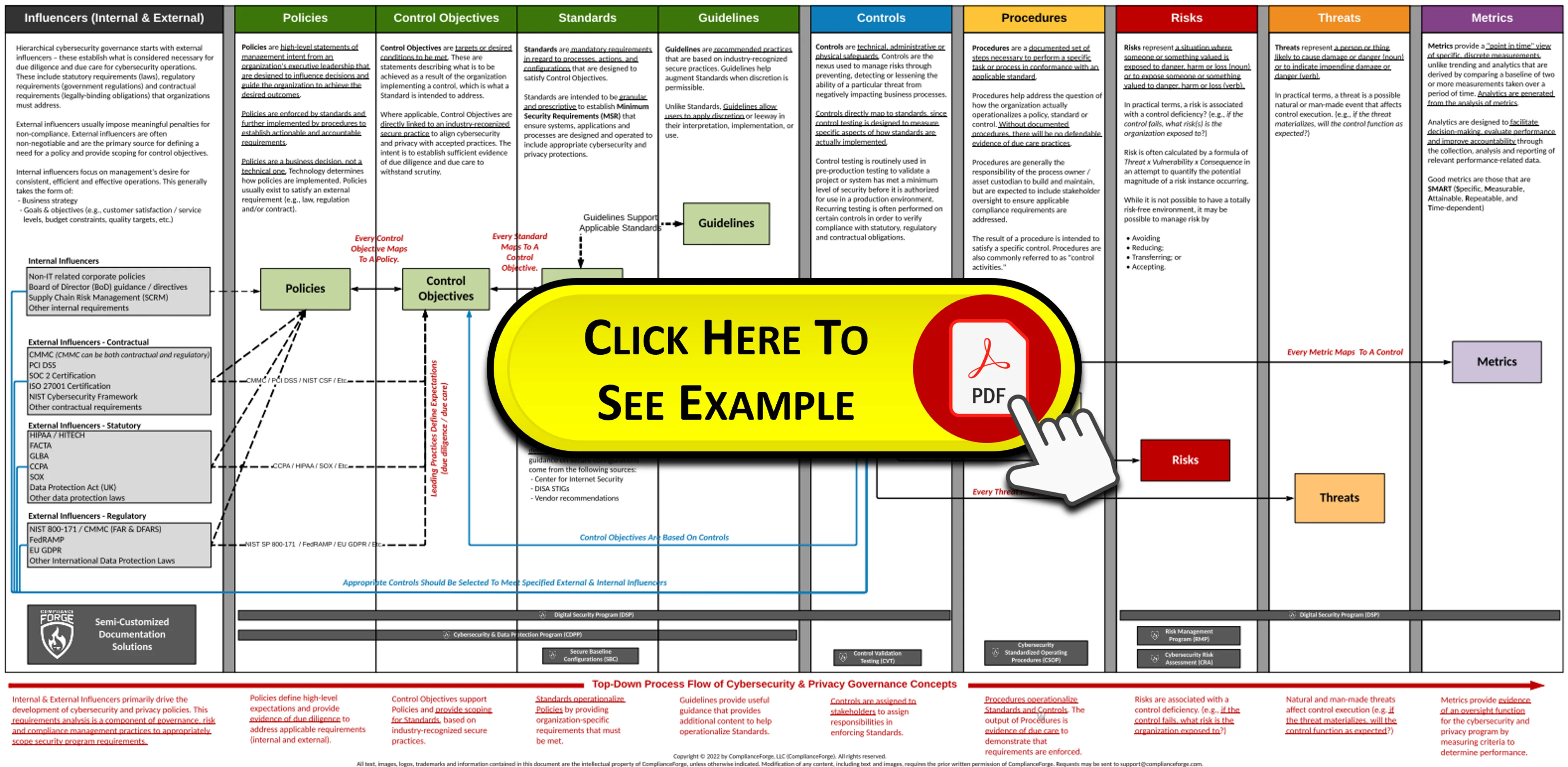
The ComplianceForge Reference Model is commonly referred to as the Hierarchical Cybersecurity Governance Framework™ (HCGF). This reference model is designed to encourage clear communication by clearly defining cybersecurity and privacy documentation components and how those are linked. This comprehensive view identifies the primary documentation components that are necessary to demonstrate evidence of due diligence and due care. The HCGF addresses the inter-connectivity of policies, control objectives, standards, guidelines, controls, risks, procedures & metrics.
The Secure Controls Framework (SCF) fits into this model by providing the necessary cybersecurity and privacy controls an organization needs to implement to stay both secure and compliant. ComplianceForge has simplified the concept of the hierarchical nature of cybersecurity and privacy documentation in the following diagram to demonstrate the unique nature of these components, as well as the dependencies that exist:
Editable SCF-Based Policies & Standards
The Digital Security Program (DSP) as an enterprise-class solution for SCF-based policies, standards, guidelines, metrics and more! The DSP is a one-time purchases with no software to install - you are buying content in the form of Microsoft Office-based documentation templates that you can edit for your specific needs. If you can use Microsoft Office or OpenOffice, you can use the DSP! While the DSP does come in Microsoft Word, it comes also comes in Excel format, so it is importable into a GRC solution that supports CSV imports (e.g., SCF Connect).
The DSP and its corresponding Cybersecurity Operating Procedures (CSOP), come together to provide "premium GRC content" that enables an organization to establish or refresh its GRC practices. The DSP consists of the thirty-three (33) SCF domains that defines a modern, digital security program (encompassing both cybersecurity and privacy considerations).
- For each SCF domain, there is a corresponding policy in the DSP.
- For each SCF control, there is a corresponding standard in the DSP.
Nested within the DSP's policies are the control objectives, standards, guidelines and metrics enable governance of your cybersecurity & privacy program. The DSP was developed to meet the need for growing organizations that want to avoid being locked into alignment with a single framework or have complex compliance requirements that span multiple frameworks. This SCF-based approach is a "best in class" hybrid framework structure that provides you with the ability to align with multiple frameworks in an efficient and scalable manner.
ComplianceForge provides organizations with exactly what they need to protect themselves - professionally-written and editable cybersecurity policies, control objectives, standards, controls, procedures and guidelines at a very affordable cost. The DSP can be found in medium and large organizations that range from Fortune 500 companies, to US and international government agencies, universities and other organizations that have complex compliance requirements and need an efficient, scalable solution for their Governance, Risk & Compliance (GRC) needs.
- The DSP is footnoted to provide authoritative references for the statutory, regulatory and contractual requirements that need to be addressed. Just as Human Resources publishes an “employee handbook” to let employees know what is expected for employees from a HR perspective, the DSP does this from a cybersecurity perspective.
- The Cybersecurity Operating Procedures (CSOP) is available that provides mapped procedures to the DSP's standards. This is a 1-1 mapping with a procedure for each standard.
The structure of the Digital Security Program is scalable to make it is easy to add or remove policy sections, as your business needs change. The same concept applies to standards – you can simply add/remove content to meet your specific needs. The DSP addresses the “why?” and “what?” questions, since policies and standards form the foundation for your cybersecurity program. The following two documents shown below are well worth the time to make a pot of coffee and read through, since you will be able to understand both the structure of the documentation and how you can customize it for your specific needs.
The DSP is our recommended solution if you are currently using or plan to use a Governance, Risk & Compliance (GRC) or Integrated Risk Management (IRM) solution. The DSP is ready to import into your GRC/IRM instance, since it comes in both Microsoft Word and Excel formats. This makes the import from Excel straightforward and that allows you to then do you any customization and collaboration directly from your GRC portal.
The DSP's policies & standards have direct, 1-1 mapping to the SCF's controls. The DSP leverages several key SCF components to provide “more than just policies & standards” by incorporating maturity criteria, a threat catalog, a risk catalog and more! The DSP provides invaluable content to operationalize several of the SCF's notable capabilities:
- Security & Privacy (S|P) Principles
- Privacy Management Principles (PMP)
- Security & Privacy Capability Maturity Model (SP-CMM)
- Security & Privacy Risk Management Model (SP-RMM)
- Premium Governance, Risk Management & Compliance (GRC) Content
When you look at the costs associated with either (1) hiring an external consultant to write cybersecurity documentation for you or (2) tasking your internal staff to write it, the cost comparisons paint a clear picture that buying from ComplianceForge is the logical option. Compared to hiring a consultant, you can save months of wait time and tens of thousands of dollars. Whereas, compared to writing your own documentation, you can potentially save hundreds of work hours and the associated cost of lost productivity. Purchasing the DSP from ComplianceForge offers these fundamental advantages when compared to the other options for obtaining quality cybersecurity documentation.
The process of writing cybersecurity documentation can take an internal team many months and it involves pulling your most senior and experienced cybersecurity experts away from operational duties to assist in the process, which is generally not the most efficient use of their time. In addition to the immense cost of hiring a cybersecurity consultant at $300/hr+ to write this documentation for you, the time to schedule a consultant, provide guidance and get the deliverable product can take months. Even when you bring in a consultant, this also requires involvement from your internal team for quality control and answering questions, so the impact is not limited to just the consultant's time being consumed.
Editable SCF-Based Procedures
The Cybersecurity Standardized Operating Procedures (CSOP) as an enterprise-class solution for SCF-based procedures that augments the Digital Security Program (DSP)'s SCF-based policies, control objectives, standards, guidelines and metrics! The CSOP is a one-time purchases with no software to install - you are buying content in the form of Microsoft Office-based documentation templates that you can edit for your specific needs. If you can use Microsoft Office or OpenOffice, you can use the CSOP! While the CSOP does come in Microsoft Word, it comes also comes in Excel format, so it is easy to import into a GRC/IRM solution that supports CSV imports (e.g., SCF Connect).
The CSOP and its corresponding Digital Security Program (DSP), come together to provide "premium GRC content" that enables an organization to establish or refresh its GRC practices. For each SCF control, there is a corresponding procedures in the CSOP.
Organizations are often not at a loss for a set of policies, but executing those requirements often fall short due to several reasons. Standardized Operating Procedures (SOPs) are where the rubber meets the road for Individual Contributors (ICs), since these key players need to know:
- How they fit into day-to-day operations;
- What their priorities are; and
- What is expected from them in their duties.
When looking at it from an auditability perspective, the evidence of due diligence and due care should match what the organization's cybersecurity business plan is attempting to achieve. One of the most important things to keep in mind with procedures is that the "ownership" is different than that of policies and standards:
- Policies, standards and controls are designed to be centrally-managed at the corporate level (e.g., governance, risk & compliance team, CISO, etc.).
- Controls are assigned to stakeholders, based on applicable statutory, regulatory and contractual obligations.
- Procedures are by their very nature de-centralized, where control implementation at the team-level is defined to explain how the control is addressed (e.g., network team, desktop support, HR, procurement, etc.).
Given this approach to how documentation is structured, based on "ownership" of the documentation components:
- Policies, standards and controls are expected to be published for anyone within the organization to have access to, since it applies organization-wide. This may be centrally-managed by a GRC/IRM platform or published as a PDF on a file share, since they are relatively static with infrequent changes.
- Procedures are "living documents" that require frequent updates based on changes to technologies and staffing. Procedures are often documented in "team share" repositories, such as a wiki, SharePoint page, workflow management tool, etc.
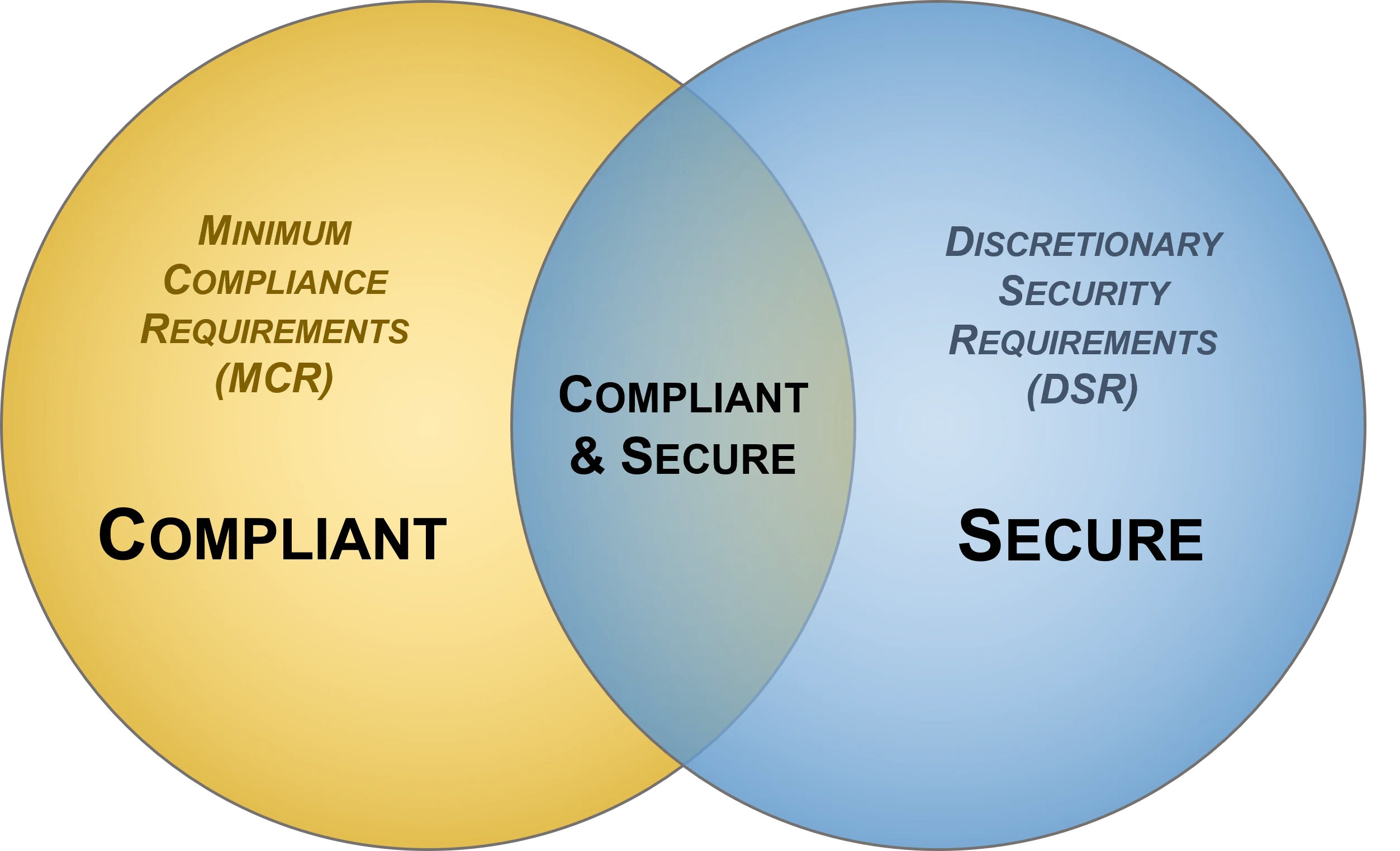
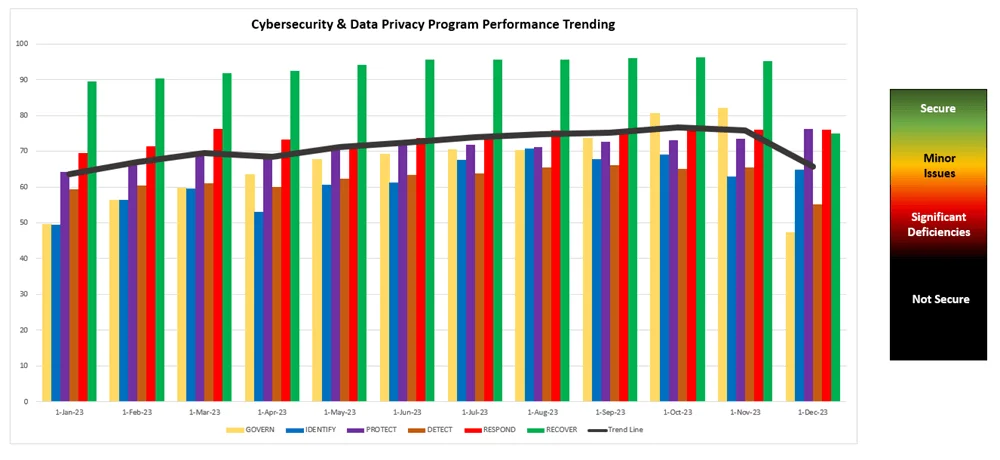
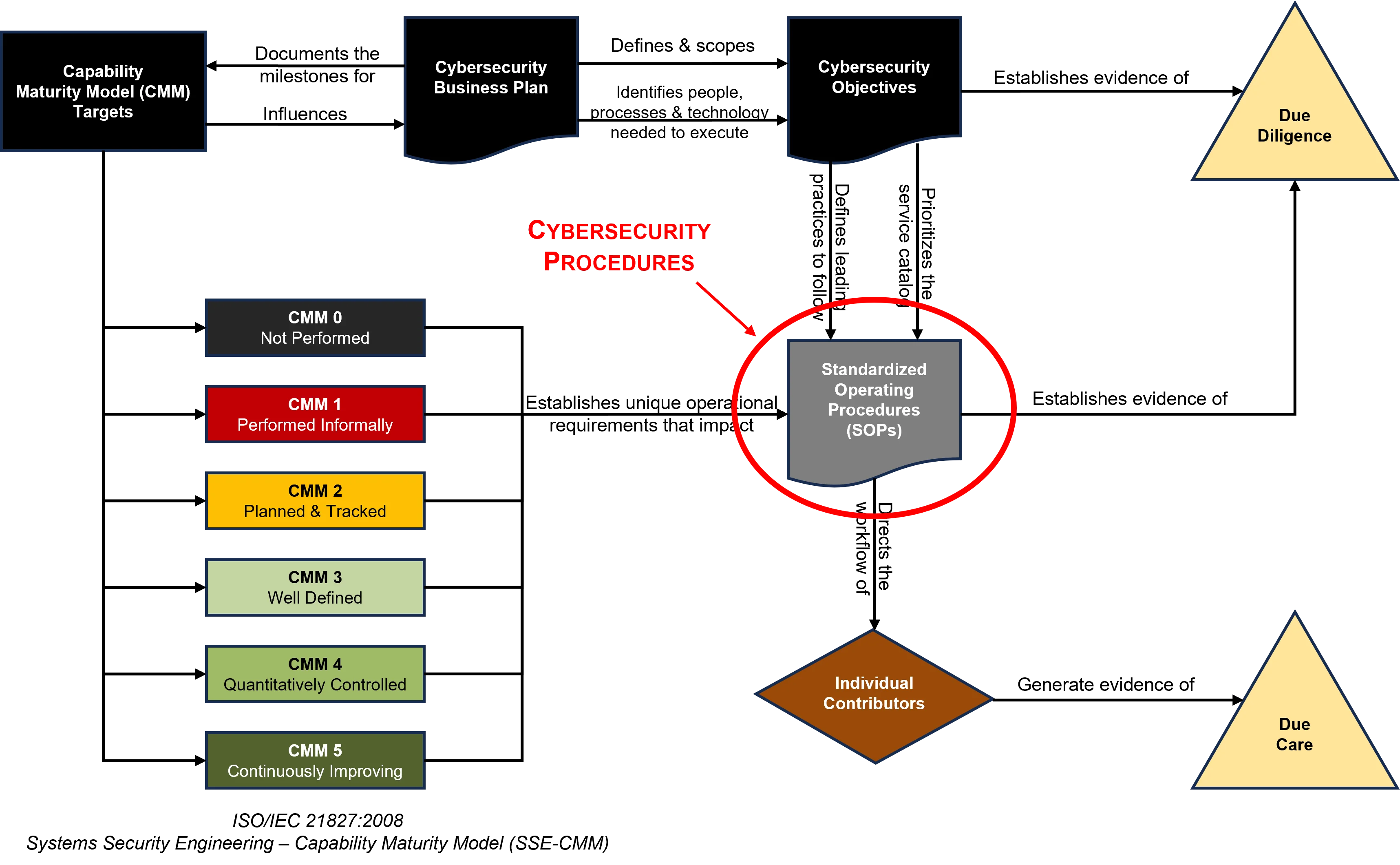
The central focus of any procedures should be a Capability Maturity Model (CMM) target that provides quantifiable expectations for People, Processes and Technologies (PPT), since this helps prevent a “moving target” by establishing an attainable expectation for “what right looks like” in terms of PPT. Generally, cybersecurity business plans take a phased, multi-year approach to meet these CMM-based cybersecurity objectives. Those objectives, in conjunction with the business plan, demonstrate evidence of due diligence on behalf of the CISO and his/her leadership team. The objectives prioritize the organization’s service catalog through influencing procedures at the IC-level for how PPT are implemented at the tactical level. SOPs not only direct the workflow of staff personnel, but the output from those procedures provides evidence of due care.
The diagram below helps show the critical nature of documented cybersecurity procedures in keeping an organization both secure and compliant:
The process of writing cybersecurity documentation can take an internal team many months and it involves pulling your most senior and experienced cybersecurity experts away from operational duties to assist in the process, which is generally not the most efficient use of their time. In addition to the immense cost of hiring a cybersecurity consultant at $300/hr+ to write this documentation for you, the time to schedule a consultant, provide guidance and get the deliverable product can take months. Even when you bring in a consultant, this also requires involvement from your internal team for quality control and answering questions, so the impact is not limited to just the consultant's time being consumed.
SCF Premium Content - Data Privacy Program (DPP)
The Data Privacy Program (DPP) as a solution to accelerate the adoption and implementing of a privacy program at your organization! The reality for most non-Fortune 1,000 organizations is that data protection duties are often assigned to cybersecurity staff. The concept of establishing a privacy program can be a daunting endeavor and is why the DPP leverages the SCF's Privacy Management Principles. This provides flexibility, due to its mapping to these commonly cited privacy laws, regulations and frameworks:
- AICPA’s Trust Services Criteria (TSC) (2017)
- Asia-Pacific Economic Cooperation (APEC)
- California Privacy Rights Act (CPRA)
- European Union General Data Protection Regulation (EU GDPR)
- Fair Information Practice Principles (FIPPs) - Department of Homeland Security (DHS)
- Fair Information Practice Principles (FIPPs) - Office of Management and Budget (OMB)
- Generally Accepted Privacy Principles (GAPP)
- HIPAA Privacy Rule
- ISO/IEC 27701:2019
- ISO/IEC 29100:2011
- Nevada SB820
- NIST SP 800-53 R4
- NIST SP 800-53 R5
- NIST Privacy Framework v1.0
- OASIS Privacy Management Reference Model (PMRM)
- Organization for Economic Co-operation and Development (OECD)
- Office of Management and Budget (OMB) - Circular A-130
- Personal Information Protection and Electronic Documents Act (PIPEDA)
- Privacy by Design (PbD) – The 7 Foundational Principles
The DPP is a one-time purchases with no software to install - you are buying content in the form of Microsoft Office-based documentation templates that you can edit for your specific needs. If you can use Microsoft Office or OpenOffice, you can use the DPP!
The Data Privacy Program (DPP) is an editable "privacy program template" that exists to ensure data protection-related controls are adequately identified and implemented across your systems, applications, services, processes and other initiatives, including third-party service providers. The DPP prescribes a comprehensive framework for the collection, creation, use, dissemination, maintenance, retention, and/or disclosure of Personal Data / sensitive Personal Data (PD / sPD).
ComplianceForge designed the DPP for cybersecurity and privacy personnel who are tasked to with "privacy compliance" for their organization. This involves advising data privacy stakeholders on Privacy by Design (PbD) matters, while providing oversight to your organization's executive management that stakeholders are being held accountable for their associated data privacy practices.
At its core, the DPP is an editable Microsoft Word document that establishes your organization's privacy program. It is designed to address the who / what / when / where / why / how concepts that need to exist to operationalize privacy principles. If you take a look through the table of contents in the example listed below, you will see coverage for reasonable privacy program expectations:
- Stakeholder identification and accountability structure
- Applicable privacy-specific laws, regulations and frameworks
- Concept of Operations (CONOPS) - mission, vision, strategy and mulit-year roadmap to operationalize the privacy program
- Targeted privacy maturity level
- Organization-specific criteria to meet privacy management principles
- Data classification and handling guidelines
- And more!
The DPP is a one-time purchases with no software to install - you are buying Microsoft Office-based documentation templates that you can edit for your specific needs. If you can use Microsoft Office or OpenOffice, you can use this product! The DPP is capable of scaling for any sized company.
- The DPP is an editable Microsoft Word document that providers program-level guidance to directly supports your company's policies and standards for ensuring secure engineering and privacy principles are operationalized.
- This product addresses the “how?” questions for how your company ensures privacy principles are operationalized.
Based on our experience, we understand that most smaller-to-medium-sized businesses lack the knowledge and experience to undertake such privacy program documentation efforts. That means businesses are faced to either outsource the work to expensive privacy consultants, write it themselves or ignore the requirement in hopes of not get in trouble for being non-compliant. To solve this issue, ComplianceForge chose to leverage the the Secure Controls Framework Privacy Management Principles (SCF PMP) as an efficient way to align with an assortment of "privacy principles" that organizations are faced with.
When you look at a comparison of privacy-relevant laws, regulations and frameworks, you will see a wide variety of expectations. The SCF PMP's solution to the apples-to-oranges comparison was to create a metaframework of privacy principles that covers nineteen (19) privacy frameworks to provide the ability to demonstrate adherence to multiple privacy principles.