# https://securecontrolsframework.com llms-full.txt
## Cybersecurity Framework
[](https://securecontrolsframework.com/scf-download/)
## Cybersecurity & Data Privacy Metaframework
The Common Controls Framework
[\\
\\
**Cybersecurity & Data Privacy (C\|P) Principles** Learn More](https://securecontrolsframework.com/domains-principles/)
[\\
\\
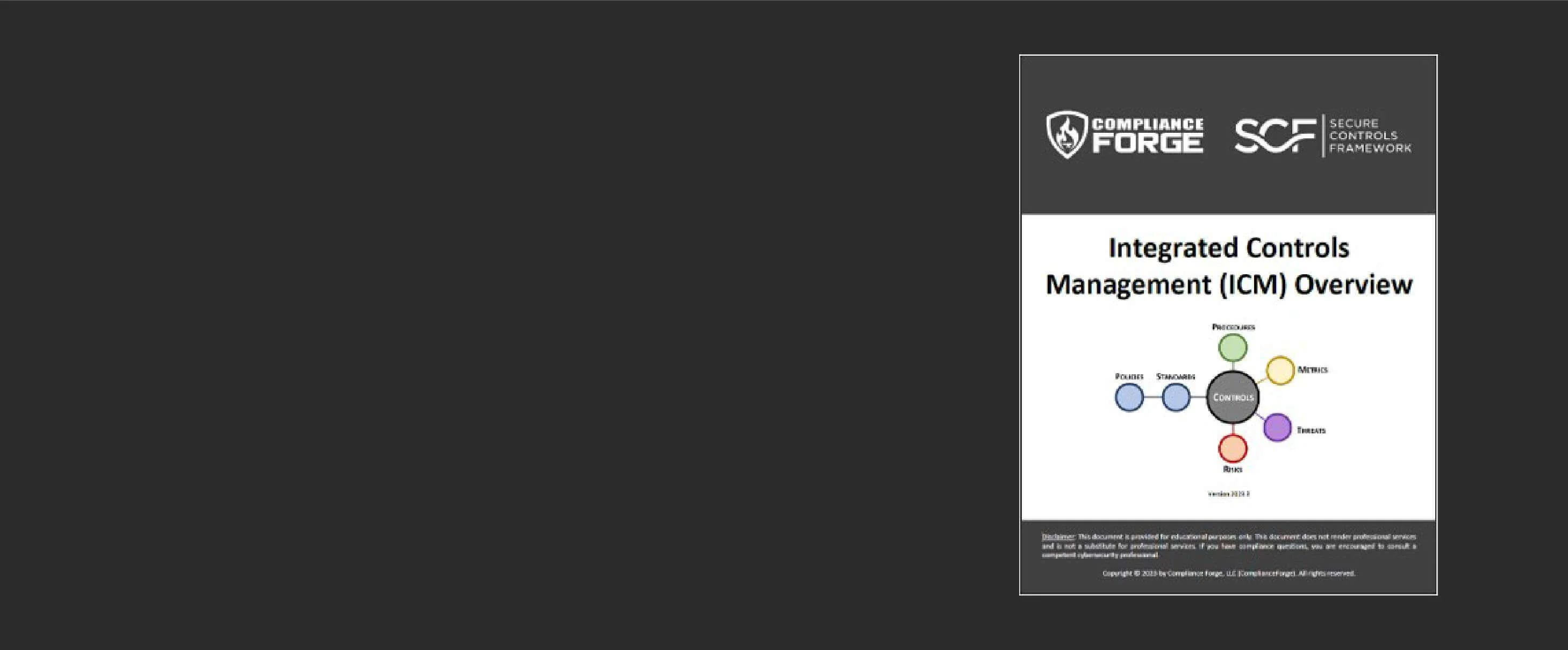
**Integrated Controls Management (ICM)** Learn More](https://securecontrolsframework.com/integrated-controls-management/)
[\\
\\
**Capability Maturity Model** Learn More](https://securecontrolsframework.com/capability-maturity-model/)
[\\
\\
**Risk Management Model** Learn More](https://securecontrolsframework.com/risk-management-model/)
[\\
\\
**Data Privacy Principles** Learn More](https://securecontrolsframework.com/data-privacy-management-principles/)
## Our Story
a little bit about us
Like it or not, cybersecurity is a protracted war on an asymmetric battlefield - the threats are everywhere and as defenders we have to make the effort to work together to help improve cybersecurity and data privacy practices, since we all suffer when massive data breaches occur or when cyber attacks have physical impacts.
Hackers share information on attack methods with other hackers, so why shouldn’t the good guys share information on how to best protect an organization? We decided to take action and make a difference.
The SCF is made up of volunteers, mainly specialists within the cybersecurity profession, who want to make a difference. The end product is "expert-derived content" that makes up the SCF.
[read more](https://securecontrolsframework.com/about-us/)
## SCF News & Updates
If it’s worth knowing about, you’ll find it here.
##### SCF Launches Registered Provider Organization (RPO) Designation
The Secure Controls Framework (SCF) Council announced the official launch of the SCF Regis...
[read more](https://securecontrolsframework.com/blog/scf-launches-registered-provider-organization-rpo-designation/)
SCF Council

Apr 22nd 2025
[read more](https://securecontrolsframework.com/blog)
[](https://securecontrolsframework.com/)
© 2025 Secure Controls Framework
All rights reserved.
\| [Sitemap](https://securecontrolsframework.com/sitemap.php)
We use cookies (and other similar technologies) to collect data to improve your shopping experience. By using our website, you're agreeing to the collection of data as described in our [Privacy Policy](https://securecontrolsframework.com/privacy-notice/).
SettingsReject allAccept All Cookies
## Secure Controls Framework FAQ
# SCF Frequently Asked Questions (FAQ)
## What Is The SCF?
The SCF stands for the Secure Controls Framework. It is more than just an assortment of cybersecurity and data privacy controls, since it is focused on designing, implementing and maintaining SECURE solutions to address all applicable statutory, regulatory and contractual requirements that an organization faces. Our belief is that if you scope your requirements with security in mind, compliance will generally be a natural byproduct of those actions. We want organizations to be both secure and compliant!
Secure Controls Framework (SCF) - YouTube
[Photo image of Secure Controls Framework SCF](https://www.youtube.com/channel/UCDRJ_Zq_8oKOv68wz18j_-g?embeds_referring_euri=https%3A%2F%2Fsecurecontrolsframework.com%2F)
Secure Controls Framework SCF
126 subscribers
[Secure Controls Framework (SCF)](https://www.youtube.com/watch?v=xt_Fgbxa2KY)
Secure Controls Framework SCF
Search
Info
Shopping
Tap to unmute
If playback doesn't begin shortly, try restarting your device.
You're signed out
Videos you watch may be added to the TV's watch history and influence TV recommendations. To avoid this, cancel and sign in to YouTube on your computer.
CancelConfirm
Share
Include playlist
An error occurred while retrieving sharing information. Please try again later.
Watch later
Share
Copy link
Watch on
0:00
0:00 / 1:01
•Live
•
[Watch on YouTube](https://www.youtube.com/watch?v=xt_Fgbxa2KY "Watch on YouTube")
### How Do I Use The SCF?
You can start in one of two ways:
1. Download the Excel version of the SCF [here](https://securecontrolsframework.com/scf-download/ "SCF download") and create your own set of controls from the complete listing of SCF controls; or
2. Use a GRC tool, such as [SCF Connect](https://scfconnect.com/ "SCF Connect") or others listed on the [SCF Marketplace](https://scf-marketplace.com/).
Realistically, pour yourself a cup of coffee (or your favorite beverage) and read through the SCF to get an understanding for its overall layout and what it contains. Being an Excel spreadsheet, you can do wonders with sorting out what is applicable to you. We even wrote a " [start here guide](https://securecontrolsframework.com/content/SCF-Recommended-Practices.pdf "SCF start here guide")" to help you understand the possibilities with the SCF.
What happens if you get stuck and don't know how to tailor the SCF or what steps you need to take to operationalize it? We have thought of that and we have a resource where you can find a [SCF Practitioner](https://scf-marketplace.com/ "SCF Practitioner") \- specialists within the cybersecurity and privacy fields who you can contract with. We give away the SCF for free, but if you want to get a consultant to walk you through setting up or operationalizing your control set, you will have to pay for a consultant to assist and that is outside of the scope of what this website offers.
## How Often Is The SCF Updated?
The general cadence for updates is one (1) update per quarter. There may be situations where out-of-cycle updates are released, but the goal is to publish updates on a quarterly basis.
## Why Is the SCF Free To Use?
Quite simply, the SCF is free to help fix the broken nature of cybersecurity and privacy practices in many organizations. We cannot rely on politicians to fix anything, so it is up to us to provide solutions.
The quality of the SCF could easily justify a costly subscription service, but we know that would exclude most organizations and defeat our broader goal of improving cybersecurity and privacy practices on a macro scale. While our contributors are volunteers, we rely on our generous [sponsors](https://securecontrolsframework.com/sponsors/) to maintain the SCF.
## Are There Restrictions On The Use of the SCF?
The Secure Controls Framework is copyrighted material, but we leverage the Creative Commons licensing model to keep it free for businesses to use. Please see the [Terms & Conditions](https://securecontrolsframework.com/terms-conditions/) page for more details on this where you will see the open license that is granted for organizations to freely the use of the SCF.
## Why Does The SCF Say It Is The Common Controls Framework?
The use of Common Controls Framework™ is trademarked and the SCF has exclusive rights to say the SCF is the Common Controls Framework™. Additionally, the domains [common-controls-framework.com](http://common-controls-framework.com/ "Common Controls Framework") and [commoncontrolsframework.com](http://commoncontrolsframework.com/ "Common Controls Framework") point to the SCF.
## What Does "Mechanisms Exist" Mean?
We wrote the controls to be flexible to meet the needs of organizations, regardless of the size or industry. As you might imagine, that can make wording a challenge. Given that, you will see text within the controls, such as "Mechanisms exist to..." and if you do not like the term mechanism, you can replace that with "solution," "processes," or some other term of your preference.
However, the term "mechanism" can mean a manual process, technology solution, outsourced contract or a combination of those that come together to address the needs of the control. Some smaller companies may lack technology solutions for many controls, so manual processes will likely prevail. However, getting into Fortune 500 environments, technology solutions will most often exist to address the controls.
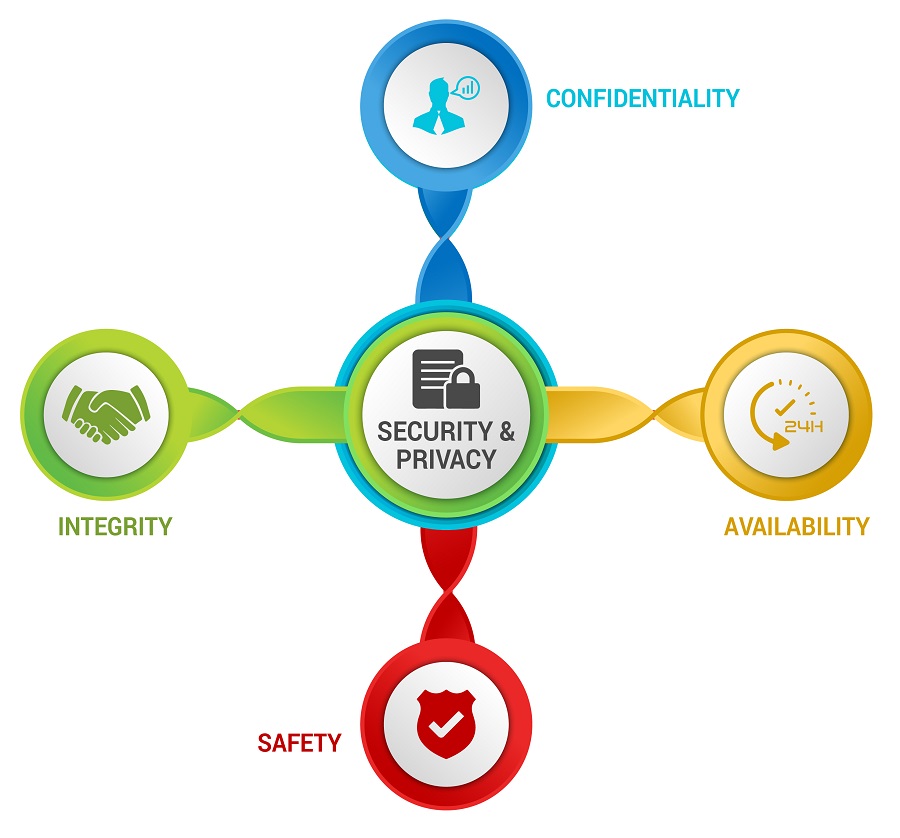
## What The CIAS Model and Why Should It Replace The "CIA Triad"?
With the rise of Artificial Intelligence (AI) and autonomous technologies, the traditional Confidentiality, Integrity & Availability "CIA Triad" is insufficient to address the needs of a modern, digital cybersecurity and privacy program due to its avoidance of a safety component. The CIA Triad does not adequately represent a digital world with embedded technologies (e.g., Internet of Things (IoT) and Operational Technology (OT)) and AI-powered capabilities. The security of systems, applications and services must include controls to offset possible threats, as well as controls to ensure Confidentiality, Integrity, Availability and Safety (CIAS):
- **CONFIDENTIALITY**– This addresses preserving authorized restrictions on access and disclosure to authorized users and services, including means for protecting personal privacy and proprietary information.
- **INTEGRITY**– This addresses protecting against improper modification or destruction, including ensuring non-repudiation and authenticity.
- **AVAILABILITY**– This addresses timely, reliable access to data, systems and services for authorized users, services and processes.
- **SAFETY**– This addresses reducing risk associated with technologies that could fail or be manipulated by nefarious actors to cause death, injury, illness, damage to or loss of equipment.
If your organization utilizes IoT/OT devices and/or is utilizing (or planning to) AI and autonomous technologies, risk management discussions should include considerations for how the technology could be used for nefarious purposes or how safety could be jeopardized from emergent behaviors:
- Device Tampering: Can this technology lead to harm? (e.g., turn off a pacemaker; too much/too little drug dispensing; open/close physical access; etc.)
- Cyber Stalking: Can this technology lead to real-world stalking risks? (e.g., geolocation; travel patterns; recent contacts; etc.)
- Physical Damage: Can this technology lead to real-world physical damage (e.g., [Aurora Generator Test](https://en.wikipedia.org/wiki/Aurora_Generator_Test)) that could lead to physical harm?
- Cyber Warfare: Can this technology be weaponized by a nation state to support military or intelligence-gathering gains?
- Terrorism: Can this technology be weaponized by terrorists?
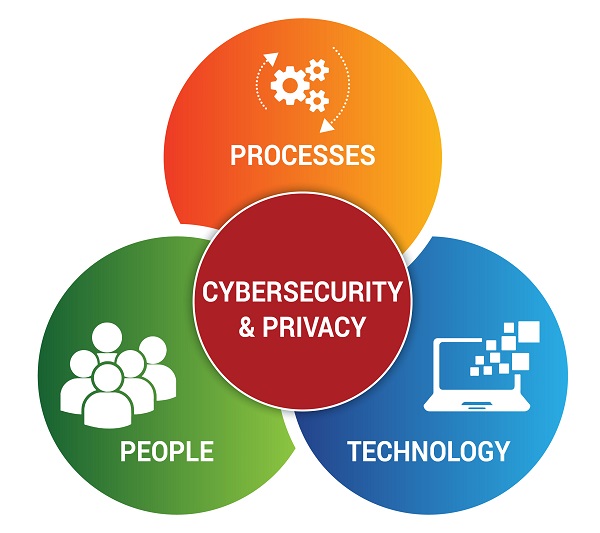
## What Is Cybersecurity For Privacy by Design (C4P)?
Cybersecurity For Privacy by Design (C4P) is simply the concept of designing, implementing and maintaining the appropriate cybersecurity controls that address the confidentiality and integrity side of data privacy concerns with Personal Information (PI).
Surprising to many people, data privacy protections overlay most existing security protection mechanisms. In a C4P model, the focus is on People, Processes and Technology (PPT) to:
- Enable privacy.
- Preset security configuration settings so that they are secure by default.
- "Bake in” security mechanisms, as compared to “bolt on” protections as an afterthought.
- Value keeping things simple to save resources and avoid negatively affecting users.
- Integrate throughout the lifecycle of projects / applications / systems.
- Support a common method to “trust but verify” projects / applications / systems.
- Set security up to be seen as an enabler through educating users, managing expectations, and supporting change.
[](https://securecontrolsframework.com/)
© 2025 Secure Controls Framework
All rights reserved.
\| [Sitemap](https://securecontrolsframework.com/sitemap.php)
We use cookies (and other similar technologies) to collect data to improve your shopping experience. By using our website, you're agreeing to the collection of data as described in our [Privacy Policy](https://securecontrolsframework.com/privacy-notice/).
SettingsReject allAccept All Cookies
## ESG Cybersecurity Compliance

# Cybersecurity Environmental, Social & Governance (ESG)
Environmental, Social & Governance (ESG) is a concept that is easily abused, where **ESG is only as good as the executive leadership team involved in enforcing those self-imposed mandates**. Any critical review of an ESG program should evaluate exceptions management practices to determine if ESG is merely "virtue signaling" to promote the organization through fraudulent marketing purposes or if the organization is willing to operationalize difficult decisions that could lead to lost profits in the pursuit of being a good corporate citizen. The SCF Council is fundamentally against this concept of ESG virtue signaling, since it offers no benefit to society in any form.
In 2021, the SCF added five (5) ESG-specific controls that are intended to identify potentially harmful compliance requirements that have profound, life-changing implications from complying with a law or regulation from a hostile nation / oppressive regime. The goal of these ESG-specific controls is to elevate risk / decision making away from cybersecurity & data privacy practitioners by directing those issues to the organization’s executive leadership to address the moral and legal ramifications of such compliance actions. The implications include, but are not limited to:
- Foreign government espionage;
- Intellectual property theft; and
- Human rights abuses.
These controls focus on potentially ruinous corporate practices that organizations often agree to in order to gain market access to hostile nations / oppressive regimes. These are also concepts that should be included in any organization's Cybersecurity Supply Chain Risk Management (C-SCRM) strategy and implementation plan:
### **GOV-12: Forced Technology Transfer**
_Mechanisms exist to avoid and/or constrain the forced exfiltration of sensitive / regulated information (e.g., Intellectual Property) to the host government for purposes of market access or market management practices._
### **GOV-13: State-Sponsored Espionage**
_Mechanisms exist to constrain the host government's ability to leverage the organization's technology assets for economic or political espionage and/or cyberwarfare activities._
### **CPL-06: Government Surveillance**
_Mechanisms exist to constrain the host government from having unrestricted and non-monitored access to the organization's systems, applications, services that could potentially violate other applicable statutory, regulatory and/or contractual obligations._
### **DCH-26: Data Localization**
_Mechanisms exist to constrain the impact of "digital sovereignty laws," that require localized data within the host country, where data and processes may be subjected to arbitrary enforcement actions that potentially violate other applicable statutory, regulatory and/or contractual obligations._
### **PRI-16: Potential Human Rights Abuses**
_Mechanisms exist to constrain the supply of physical and/or digital activity logs to the host government that can directly lead to contravention of the [Universal Declaration of Human Rights (UDHR)](https://www.un.org/en/about-us/universal-declaration-of-human-rights "Cybersecurity ESG Universal Declaration of Human Rights"), as well as other applicable statutory, regulatory and/or contractual obligations._
## Beware of "Garbage In Garbage Out" ESG Practices
Fraud Magazine has a [good article](https://www.fraud-magazine.com/article.aspx?id=4295015764) on concerns related to abusing ESG principles that is well worth reading. The very real existence of sham practices associated with ESG puts the entire concept of ESG on shaky ground, such as:
- Making an organization look better than it is through the purchase of carbon credits to offset manufacturing practices; or
- Selectively enforcing prohibitions on choosing supply chain partners (e.g., Uyghur forced labor).
**The issue of choosing the harder right over the easier (and more profitable) wrong is the fundamental flaw with ESG in many organizations, since "faithful ESG practices" will often lead to a decision that would avoid engaging in or put an end to a profitable business venture.**
On the cybersecurity & data privacy side of ESG, unlike buying carbon credits, an organization cannot make up for its own lacking cybersecurity & data privacy practices by buying goodwill from another organization that implements its own responsible cybersecurity & data privacy practices. This means organizations need to step up and actually do what they should be doing to earn a good "social" rating, in the scope of ESG compliance. In cybersecurity, "a standard is a standard for a reason" and that concept needs to be enforced, even if it means making difficult choices that could negatively affect profits. **Without an ethical, morally-rigid leadership team, ESG is not only meaningless, but fundamentally dishonest and indicative of fraudulent business practices**. ESG must be driven from the highest levels of the organization's leadership team, but only if they are willing to chose the harder right over the easier wrong.
## Cybersecurity & Data Privacy Implications For ESG
ESG criteria are considerations of interest for "social responsibility" at the corporate level. ESG is traditionally used to screen potential investments as a way to support and maintain ethical conduct across organizations. However, with the evolving landscape of statutory, regulatory and contractual obligations, the SCF identified two significant points of intersection between the SCF's cybersecurity & data privacy controls with the "social" component of ESG factors:
1. Data protection / data privacy; and
2. Human rights.
The social criteria component of ESG takes into account the human factor at the individual level, as well as what occurs within those organizations as part of normal business operations. This is where cybersecurity & data privacy come into play with the social criteria of the ESG model with the real-world ramifications associated with access to sensitive data and critical systems.
ESG is inexplicitly intertwined with cybersecurity & data privacy practices, since these functions have the ability to directly affect individuals, organizations, governments and society as a whole. Therefore, IT/cyber/privacy operations cannot merely “check the box” by providing access or data without understanding the real-world ramifications associated with compliance with a law, regulation or contractual obligation. How an organization responds to potentially hostile compliance requirements will determine its genuine adherence to ESG principles for corporate responsibility, since non-compliance might be the morally-correct path for an organization to take.
## Integrated Controls Management (ICM) Approach To ESG
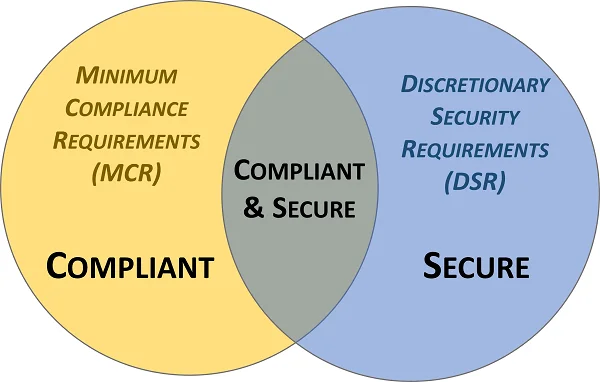
There are no "cookie cutter" controls that specifically apply for ESG, since every organization is unique. Therefore, when trying to figure "how to do ESG" from a practical approach, it is recommended to look at it through an [Integrated Controls Management (ICM)](https://securecontrolsframework.com/integrated-controls-management/) perspective. ICM specifically focuses on the need to understand and clarify the difference between "compliant" versus "secure" since that is necessary to have coherent risk management discussions.
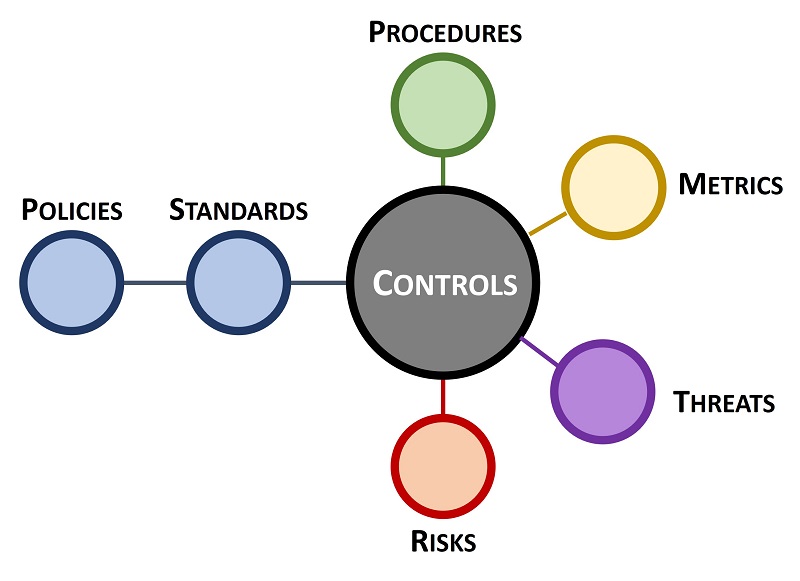

To assist in this process, ICM helps an organization categorize its applicable controls according to
“must have” vs “nice to have” requirements:
- Minimum Compliance Requirements (MCR) are the absolute minimum requirements that must be addressed to comply with applicable laws, regulations and contracts.
- Discretionary Security Requirements (DSR) are tied to the organization’s risk appetite since DSR are “above and beyond” MCR, where the organization self-identifies additional cybersecurity and data protection controls to address voluntary industry practices or internal requirements, such as findings from internal audits or risk assessments.
Secure and compliant operations exist when both MCR and DSR are implemented and properly governed:
- MCR are primarily externally-influenced, based on industry, government, state and local regulations. MCR should never imply adequacy for secure practices and data protection, since they are merely compliance-related.
- DSR are primarily internally-influenced, based on the organization’s respective industry and risk tolerance. While MCC establish the foundational floor that must be adhered to, DSR are where organizations often achieve improved efficiency, automation and enhanced security.
You can read more about ICM by downloading this overview document:
[](https://content.securecontrolsframework.com/Integrated-Controls-Management.pdf "Integrated Controls Management")
[](https://securecontrolsframework.com/)
© 2025 Secure Controls Framework
All rights reserved.
\| [Sitemap](https://securecontrolsframework.com/sitemap.php)
We use cookies (and other similar technologies) to collect data to improve your shopping experience. By using our website, you're agreeing to the collection of data as described in our [Privacy Policy](https://securecontrolsframework.com/privacy-notice/).
SettingsReject allAccept All Cookies
## SCF Sponsors Page
# SCF Sponsors
The SCF could not exist without the generous support from our sponsors.
## Founding Sponsors
These organizations helped get the SCF established in 2018, so with the generous support from these companies, the SCF would not exist:
| | | | | |
| --- | --- | --- | --- | --- |
| [](https://www.complianceforge.com/ "SCF-based policies standards and procedures") | | [](https://www.verutus.com/ "SCF cybersecurity consulting") | | [](https://www.securitywaypoint.com/ "SCF consulting services") |
## Sustaining Sponsors
These organizations continue to demonstrate a strong commitment to the SCF, so we thank them for their outstanding support that helps us do what we do:
| | | |
| --- | --- | --- |
| [](https://howtogrc.com/ "SCF consulting services") | | [](https://www.vigilant.us/ "SCF consulting services") |
| | | |
| | | |
[](https://securecontrolsframework.com/)
© 2025 Secure Controls Framework
All rights reserved.
\| [Sitemap](https://securecontrolsframework.com/sitemap.php)
We use cookies (and other similar technologies) to collect data to improve your shopping experience. By using our website, you're agreeing to the collection of data as described in our [Privacy Policy](https://securecontrolsframework.com/privacy-notice/).
SettingsReject allAccept All Cookies
## SCF Certification Training
| | |
| --- | --- |
| **Get Trained & Earn An SCF Certification Today**
**SCF Assessor and Instructor Certification Organization (SAICO)** |  |
**What Is The SAICO?**
The SCF Assessor and Instructor Certification Organization (SAICO) is a department of the SCF. It is dedicated to upholding the highest standards in cybersecurity and compliance by providing three (3) certification programs that equip cybersecurity professionals with the expertise to evaluate and implement SCF controls effectively, ensuring organizations meet regulatory and security best practices: SCF Practitioner, SCF Architect, and SCF Assessor.
| | | |
| --- | --- | --- |
| [](https://training.securecontrolsframework.com/products/courses/scf-practitioner-training "SCF Practitioner Training") | [](https://training.securecontrolsframework.com/products/courses/scf-architect-training "SCF Architect Training") | [](https://training.securecontrolsframework.com/products/courses/scf-assessor-training "SCF Assessor Training") |
**What Training Is Provided?**
Each of these courses use Computer-Based Training (CBT), which enables you to learn at your own pace and make the most out of your personal education. Additionally, they follow a defined syllabus to meet the specific learning objectives and standards of the specified certifications.
[](https://securecontrolsframework.com/)
© 2025 Secure Controls Framework
All rights reserved.
\| [Sitemap](https://securecontrolsframework.com/sitemap.php)
We use cookies (and other similar technologies) to collect data to improve your shopping experience. By using our website, you're agreeing to the collection of data as described in our [Privacy Policy](https://securecontrolsframework.com/privacy-notice/).
SettingsReject allAccept All Cookies
## SCF Discord Server
# SCF Discord Server
To help people learn best practices around using the Secure Controls Framework (SCF), we established the SCF Discord Server. This is a free resource where you can engage with a worldwide audience of cybersecurity and privacy professionals who use the SCF. It is a place to learn, share and network. We look forward to seeing you there!
[](https://discord.gg/k5BMzbyVQP "SCF discord")
## SCF Discord Invitation Link: [https://discord.gg/k5BMzbyVQP](https://discord.gg/k5BMzbyVQP "SCF Discord Community")
[](https://securecontrolsframework.com/)
© 2025 Secure Controls Framework
All rights reserved.
\| [Sitemap](https://securecontrolsframework.com/sitemap.php)
We use cookies (and other similar technologies) to collect data to improve your shopping experience. By using our website, you're agreeing to the collection of data as described in our [Privacy Policy](https://securecontrolsframework.com/privacy-notice/).
SettingsReject allAccept All Cookies
## Shipping and Returns
# _**Shipping & Returns**_
_**Swag Returns Policy (e.g., SCF-branded t-shirts, sweatshirts, etc.)**_ **You may return most new, unopened items within 30 days of delivery for a full refund. We'll also pay the return shipping costs if the return is a result of our error (you received an incorrect or defective item, etc.).**
**You should expect to receive your refund within four weeks of giving your package to the return shipper, however, in many cases you will receive a refund more quickly. This time period includes the transit time for us to receive your return from the shipper (5 to 10 business days), the time it takes us to process your return once we receive it (3 to 5 business days), and the time it takes your bank to process our refund request (5 to 10 business days).**
**If you need to return an item, please [Contact Us](https://securecontrolsframework.com/contact-us/) with your order number and details about the product you would like to return. We will respond quickly with instructions for how to return items from your order.** **Physical Shipping (**e.g., SCF-branded t-shirts, sweatshirts, etc.)**** **We can ship to virtually any address in the world. Note that there are restrictions on some products, and some products cannot be shipped to international destinations.**
**When you place an order, we will estimate shipping and delivery dates for you based on the availability of your items and the shipping options you choose. Depending on the shipping provider you choose, shipping date estimates may appear on the shipping quotes page.**
**Please also note that the shipping rates for many items we sell are weight-based. The weight of any such item can be found on its detail page. To reflect the policies of the shipping companies we use, all weights will be rounded up to the next full pound.**
[](https://securecontrolsframework.com/)
© 2025 Secure Controls Framework
All rights reserved.
\| [Sitemap](https://securecontrolsframework.com/sitemap.php)
We use cookies (and other similar technologies) to collect data to improve your shopping experience. By using our website, you're agreeing to the collection of data as described in our [Privacy Policy](https://securecontrolsframework.com/privacy-notice/).
SettingsReject allAccept All Cookies
## Cybersecurity Control Framework
# About The SCF
Hackers share information on attack methods with other hackers, so why shouldn’t the good guys share information on how to best protect an organization? We decided to take action and make a difference, since we feel it is too important to wait for someone else to fix the problems that exist.
The SCF is made up of volunteers, mainly specialists within the cybersecurity profession, who focus on Governance, Risk and Compliance (GRC) and the cybersecurity side of data privacy. These are auditors, engineers, architects, incident responders, consultants and other specialists who live and breathe these topics on a daily basis. The end product is "expert-derived content" that makes up the SCF.
We have the ambitious goal of providing cybersecurity and data privacy control guidance to cover the strategic, operational and tactical needs of organizations, regardless of its size, industry or country of origin. The end state is to help companies become and stay compliant with cybersecurity and data privacy requirements. The glue that ties GRC together is a uniform set of controls. Unfortunately, in most organizations, there is no set of shared controls and that leads to poor governance practices and an overall weaker state of security and privacy.
Like it or not, cybersecurity is a protracted war on an asymmetric battlefield \- the threats are everywhere and as defenders we have to make the effort to work together to help improve cybersecurity and data privacy practices, since we all suffer when massive data breaches occur or when cyber attacks have physical impacts.
## SCF Mission
Our mission is to provide a powerful catalyst that will advance how cybersecurity and data privacy controls are utilized at the strategic, operational and tactical layers of an organization, regardless of its size or industry.
## SCF Goals
The SCF Council has a few humble goals:
- From a framework perspective, become the leading metaframework that organizations can use as a "Rosetta Stone" to build secure and compliant cybersecurity and data privacy programs.
- From a process improvement perspective, leverage the [SCF's Conformity Assessment Program (CAP)](https://securecontrolsframework.com/scf-conformity-assessment-program-cap/) to fundamentally disrupt/reform how cybersecurity third-party assessments are performed.
## Like What You See?
The SCF is operated by the Secure Controls Framework Council, LLC (US-based organization). If you like the SCF and you have the means, [please donate](https://buy.stripe.com/eVa8yJ4aIf9c75e288 "SCF Donations") to help cover the expenses to provide this website. The SCF is run entirely through donations from individuals and our [sponsors](https://securecontrolsframework.com/sponsors/).
[](https://buy.stripe.com/eVa8yJ4aIf9c75e288 "SCF donattion link")
[](https://securecontrolsframework.com/)
© 2025 Secure Controls Framework
All rights reserved.
\| [Sitemap](https://securecontrolsframework.com/sitemap.php)
We use cookies (and other similar technologies) to collect data to improve your shopping experience. By using our website, you're agreeing to the collection of data as described in our [Privacy Policy](https://securecontrolsframework.com/privacy-notice/).
SettingsReject allAccept All Cookies
## Secure Controls Framework Overview

# SCF - Make Compliance A Natural Byproduct of Secure Practices
The SCF's mission is to provide a powerful catalyst that will advance how cybersecurity and privacy controls are utilized at the strategic, operational and tactical layers of an organization, regardless of its size or industry.
| | |
| --- | --- |
| [](https://securecontrolsframework.com/content/SCF-Recommended-Practices.pdf "SCF best practices") | The Secure Controls Framework™ (SCF) focuses on internal controls. These are the cybersecurity and privacy-related policies, standards, procedures, technologies and associated processes that are designed to provide reasonable assurance that business objectives will be achieved and undesired events will be prevented, detected and corrected. This page will covers the following topics:
- Level setting what the SCF is and what it is not.
- [Integrated Controls Management (ICM)](https://securecontrolsframework.com/integrated-controls-management/) approach to develop a Plan, Do, Check & Act (PDCA) approach to controls.
- Recommendations to tailor the control set for your needs:
- Defining Minimum Compliance Requirements (MCR)
- Defining Discretionary Security Requirements (DSR)
- Leveraging the [Cybersecurity & Data Privacy Capability Maturity Model (C\|P-CMM)](https://securecontrolsframework.com/capability-maturity-model/)
- Leveraging the [Cybersecurity & Data Privacy Risk Management Model (C\|P-RMM)](https://securecontrolsframework.com/risk-management-model/)
- Ways to operationalize the SCF.
For your off-line reading pleasure, you can [download](https://content.securecontrolsframework.com/SCF_Recommended_Practices.pdf "SCF recommended practices") the PDF version of this helpful information |
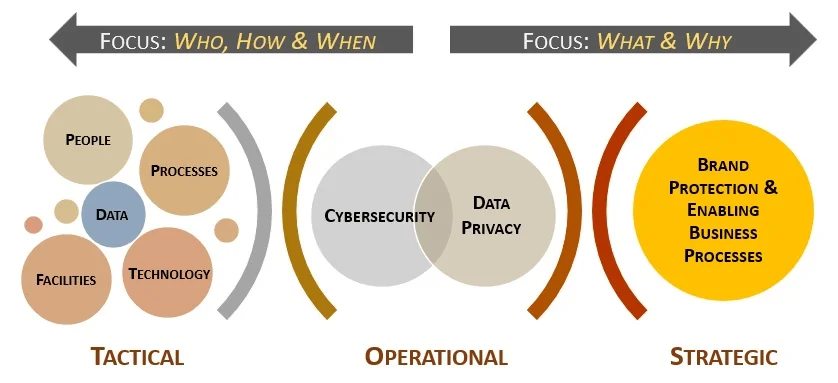
## The Secure Controls Framework™ (SCF) Is The Common Controls Framework™ (CCF)
The SCF is a "Rosetta Stone" approach to cybersecurity and privacy controls, which makes it the [Common Controls Framework™](http://commoncontrolsframework.com/ "Common Controls Framework"). The concept of the SCF is to have a metaframework (e.g., framework of frameworks) that is capable of addressing the broader People, Processes, Technology and Data (PPTD) that are what controls fundamentally exists to govern. The SCF can be used to assist with strategic planning down to tactical needs that impact the people, processes and technologies directly impacting your organization.
| | |
| --- | --- |
|  | Using the SCF should be viewed as a long-term tool to not only help with compliance-related efforts but to ensure security and privacy principles are properly designed, implemented and maintained. The SCF helps implement a holistic approach to protecting the Confidentiality, Integrity, Availability and Safety (CIAS) of your data, systems, applications and other processes. Understanding the requirements for both cybersecurity and privacy principles involves a simple process of distilling expectations. This process is all part of documenting reasonable expectations that are “right-sized” for an organization, since every organization has unique requirements.
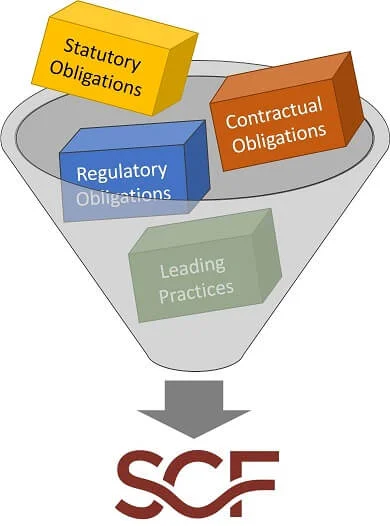
The approach looks at the following spheres of influence to identify applicable controls:
- Statutory obligations
- Regulatory obligations
- Contractual obligations
- Industry-recognized "best practices"
It is best to visualize the SCF as a buffet of cybersecurity and privacy controls, where there is a selection of 1,000+ controls available to you. Once you know what is applicable to you, you can generate a customized control set that gives you the controls you need to address your statutory, regulatory and contractual obligations. |
## Why You Should Use The SCF
**There is no sales pitch for using the SCF –** the SCF is a free resource, so there is no financial incentive for us to make companies use it:
- For companies that have just one 1-2 compliance requirements, the SCF might be considered overkill for your needs.
- For companies that have 3+ compliance requirements (e.g., organization that has requirements to address ISO 27002, SOC 2, PCI DSS and GDPR), then the SCF is a great tool to streamline the management of cybersecurity and privacy controls.
In developing the SCF, we identified and analyzed over 100 statutory, regulatory and contractual frameworks. Through analyzing these thousands of legal, regulatory and framework requirements, we identified commonalities and this allows several thousand unique controls to be addressed by the controls that makeup the SCF. For instance, a requirement to maintain strong passwords is not unique, since it is required by dozens of laws, regulations and frameworks. This allows one well-worded SCF control to address multiple requirements. This focus on simplicity and sustainability is key to the SCF, since it can enable various teams to speak the same controls language, even though they may have entirely different statutory, regulatory or contractual obligations that they are working towards.
The SCF targets silos, since siloed practices within any organization are inefficient and can lead to poor security, due to poor communications and incorrect assumptions.
#### What The SCF Is
The SCF is a comprehensive catalog of controls that is designed to enable companies to design, build and maintain secure processes, systems and applications. The SCF addresses both cybersecurity and privacy, so that these principles are designed to be “baked in” at the strategic, operational and tactical levels.
The SCF is:
- A control set.
- A useful tool to provide a “Rosetta Stone” approach to organizing cybersecurity and privacy controls so that the same controls can be used among companies and teams (e.g., privacy, cybersecurity, IT, project, procurement, etc.).
- Free for businesses to use. A result of a volunteer-led effort that uses “expert derived assessments” to perform the mapping from the controls to applicable laws, regulations and other frameworks.
The SCF also contains helpful guidance on possible tools and solutions to address controls. Additionally, it contains maturity criteria that can help an organization plan for and evaluate controls, based on a target maturity level.
#### What The SCF Is Not
While the SCF is a comprehensive catalog of controls that is designed to enable companies to design, build and maintain secure processes, systems and applications, the SCF will only ever be a control set and is not a “magic bullet” technology solution to address every possible cybersecurity and privacy compliance obligation that an organization faces.
The SCF is not:
- A substitute for performing due diligence and due care steps to understand your specific compliance needs.
- A complete technology or documentation solution to address all your security & privacy needs (e.g., the policies, standards, procedures and processes you need to have in place to be secure and compliant).
- Infallible or guaranteed to meet every compliance requirement your organization offers, since the controls are mapped based on expert-derived assessments to provide the control crosswalking that relies on human expertise and that is not infallible.
## Common Controls Framework - Structured To Address Your Cybersecurity & Privacy Needs
The SCF contains over 1,000 controls that are organized into 33 domains (as shown below) to create a "best in class" approach to structuring the controls in a logical arrangement. Having a user friendly and logical taxonomy is important, since it helps discussing controls easier when there is a logical approach to both the naming and structure. The not only benefits internal teams (e.g., cyber, IT, privacy, procurement, legal, etc.) but it is designed to be used inter-organizationally, where GOV-03 means the same thing to your company as it does to other organizations that leverage the SCF. That is a big deal!
| | | | | |
| --- | --- | --- | --- | --- |
| **#** | **Icon** | **SCF Domain** | **SCF Identifier** | **Cybersecurity & Data Privacy by Design (C\|P) Principles** |
| **1** |  | **Cybersecurity & Data Privacy Governance** | **GOV** | Execute a documented, risk-based program that supports business objectives while encompassing appropriate cybersecurity and data privacy principles that addresses applicable statutory, regulatory and contractual obligations. |
| **2** |  | **Artificial and Autonomous Technology** | **AAT** | Ensure trustworthy and resilient Artificial Intelligence (AI) and autonomous technologies to achieve a beneficial impact by informing, advising or simplifying tasks, while minimizing emergent properties or unintended consequences. |
| **3** |  | **Asset Management** | **AST** | Manage all technology assets from purchase through disposition, both physical and virtual, to ensure secured use, regardless of the asset’s location. |
| **4** |  | **Business Continuity & Disaster Recovery** | **BCD** | Maintain a resilient capability to sustain business-critical functions while successfully responding to and recovering from incidents through well-documented and exercised processes. |
| **5** |  | **Capacity & Performance Planning** | **CAP** | Govern the current and future capacities and performance of technology assets. |
| **6** |  | **Change Management** | **CHG** | Manage change in a sustainable and ongoing manner that involves active participation from both technology and business stakeholders to ensure that only authorized changes occur. |
| **7** |  | **Cloud Security** | **CLD** | Govern cloud instances as an extension of on-premise technologies with equal or greater security protections than the organization’s own internal cybersecurity and privacy controls. |
| **8** |  | **Compliance** | **CPL** | Oversee the execution of cybersecurity and privacy controls to ensure appropriate evidence required due care and due diligence exists to meet compliance with applicable statutory, regulatory and contractual obligations. |
| **9** |  | **Configuration Management** | **CFG** | Enforce secure configurations for systems, applications and services according to vendor-recommended and industry-recognized secure practices. |
| **10** |  | **Continuous Monitoring** | **MON** | Maintain situational awareness of security-related events through the centralized collection and analysis of event logs from systems, applications and services. |
| **11** |  | **Cryptographic Protections** | **CRY** | Utilize appropriate cryptographic solutions and industry-recognized key management practices to protect the confidentiality and integrity of sensitive/regulated data both at rest and in transit. |
| **12** |  | **Data Classification & Handling** | **DCH** | Enforce a standardized data classification methodology to objectively determine the sensitivity and criticality of all data and technology assets so that proper handling and disposal requirements can
be followed. |
| **13** |  | **Embedded Technology** | **EMB** | Provide additional scrutiny to reduce the risks associated with embedded technology, based on the potential damages posed from malicious use of the technology. |
| **14** |  | **Endpoint Security** | **END** | Harden endpoint devices to protect against reasonable threats to those devices and the data those devices store, transmit and process. |
| **15** |  | **Human Resources Security** | **HRS** | Execute sound hiring practices and ongoing personnel management to cultivate a cybersecurity and privacy-minded workforce. |
| **16** |  | **Identification & Authentication** | **IAC** | Enforce the concept of “least privilege” consistently across all systems, applications and services for individual, group and service accounts through a documented and standardized Identity and Access Management (IAM) capability. |
| **17** |  | **Incident Response** | **IRO** | Maintain a viable incident response capability that trains personnel on how to recognize and report suspicious activities so that trained incident responders can take the appropriate steps to handle incidents, in accordance with a documented Incident Response Plan (IRP). |
| **18** |  | **Information Assurance** | **IAO** | Execute an impartial assessment process to validate the existence and functionality of appropriate cybersecurity and privacy controls, prior to a system, application or service being used in a production environment. |
| **19** |  | **Maintenance** | **MNT** | Proactively maintain technology assets, according to current vendor recommendations for configurations and updates, including those supported or hosted by third-parties. |
| **20** |  | **Mobile Device Management** | **MDM** | Implement measures to restrict mobile device connectivity with critical infrastructure and sensitive/regulated data that limit the attack surface and potential data exposure from mobile device usage. |
| **21** |  | **Network Security** | **NET** | Architect and implement a secure and resilient defense-in-depth methodology that enforces the concept of “least functionality” through restricting network access to systems, applications and services. |
| **22** |  | **Physical & Environmental Security** | **PES** | Protect physical environments through layers of physical security and environmental controls that work together to protect both physical and digital assets from theft and damage. |
| **23** |  | **Data Privacy** | **PRI** | Align data privacy practices with industry-recognized data privacy principles to implement appropriate administrative, technical and physical controls to protect regulated personal data throughout the lifecycle of systems, applications and services. |
| **24** |  | **Project & Resource Management** | **PRM** | Operationalize a viable strategy to achieve cybersecurity & privacy objectives that establishes cybersecurity as a key stakeholder within project management practices to ensure the delivery of resilient and secure solutions. |
| **25** |  | **Risk Management** | **RSK** | Proactively identify, assess, prioritize and remediate risk through alignment with industry-recognized risk management principles to ensure risk decisions adhere to the organization's risk threshold. |
| **26** |  | **Secure Engineering & Architecture** | **SEA** | Utilize industry-recognized secure engineering and architecture principles to deliver secure and resilient systems, applications and services. |
| **27** |  | **Security Operations** | **OPS** | Execute the delivery of cybersecurity and privacy operations to provide quality services and secure systems, applications and services that meet the organization's business needs. |
| **28** |  | **Security Awareness & Training** | **SAT** | Foster a cybersecurity and privacy-minded workforce through ongoing user education about evolving threats, compliance obligations and secure workplace practices. |
| **29** |  | **Technology Development & Acquisition** | **TDA** | Develop and test systems, applications or services according to a Secure Software Development Framework (SSDF) to reduce the potential impact of undetected or unaddressed vulnerabilities and design weaknesses. |
| **30** |  | **Third-Party Management** | **TPM** | Execute Supply Chain Risk Management (SCRM) practices so that only trustworthy third-parties are used for products and/or service delivery. |
| **31** |  | **Threat Management** | **THR** | Proactively identify and assess technology-related threats, to both assets and business processes, to determine the applicable risk and necessary corrective action. |
| **32** |  | **Vulnerability & Patch Management** | **VPM** | Leverage industry-recognized Attack Surface Management (ASM) practices to strengthen the security and resilience systems, applications and services against evolving and sophisticated attack vectors. |
| **33** |  | **Web Security** | **WEB** | Ensure the security and resilience of Internet-facing technologies through secure configuration management practices and monitoring for anomalous activity. |
## Integrated Controls Management (ICM) Approach To Building A Security Program
Building a security program that routinely incorporates security and privacy practices into daily operations requires a mastery of the basics. A useful analogy is with the children's toy, LEGO®. With LEGO® you can build nearly anything you want — either through following directions or using your own creativity. However, it first requires an understanding of how various LEGO® shapes either snap together or are incompatible.
Once you master the fundamentals with LEGO®, it is easy to keep building and become immensely creative since you know how everything interacts. However, when the fundamentals are ignored, the LEGO® structure will be weak and include systemic flaws. Security and privacy really are not much different, since those disciplines are made up of numerous building blocks that all come together to build secure systems and processes. The lack of critical building blocks will lead to insecure and poorly architected solutions.
When you envision each component that makes up a security or privacy “best practice” is a LEGO® block, it is possible to conceptualize how certain requirements are the foundation that form the basis for others components to attach to. Only when the all the building blocks come together and take shape do you get a functional security / privacy program!
Think of the SCF as a toolkit for you to build out your overall security program domain-by-domain so that cybersecurity and privacy principles are designed, implemented and managed by default!
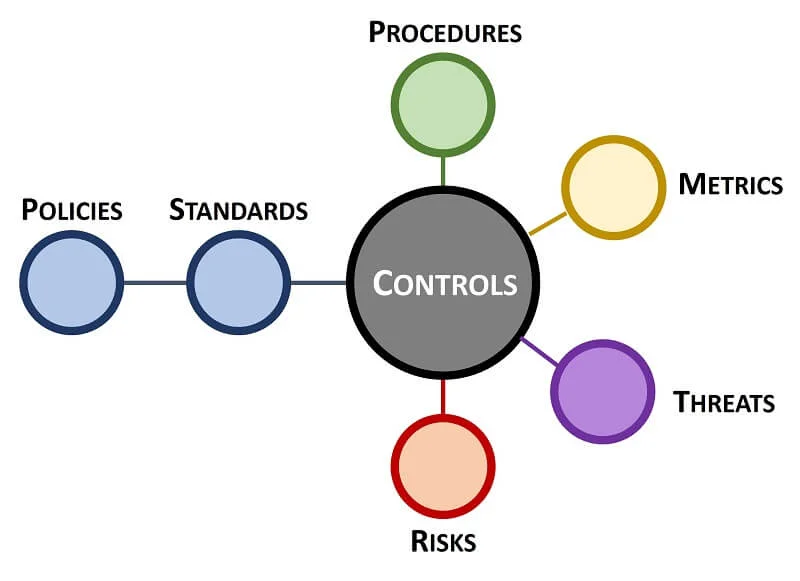
### Controls Are Key To Everything In Cybersecurity & Data Protection
The premise of [Integrated Controls Management (ICM)](https://securecontrolsframework.com/integrated-controls-management/) is that controls are central to cybersecurity and privacy operations, as well as the overall business rhythm of an organization.
ICM is designed to proactively address the strategic, operational and tactical nature of operating an organization’s cybersecurity and privacy program at the control level. ICM is designed to address both internal controls, as well as the broader concept of Supply Chain Risk Management (SCRM).
| | | |
| --- | --- | --- |
| [](https://securecontrolsframework.com/integrated-controls-management/) | | [](https://content.securecontrolsframework.com/Integrated-Controls-Management.pdf "Integrated Controls Management (ICM) framework") |
ICM specifically focuses on the need to understand and clarify the difference between "compliant" versus "secure" since that is necessary to have coherent risk management discussions. To assist in this process, an organization’s applicable controls are categorized according to “must have” vs “nice to have” requirements:
- **Minimum Compliance Requirements (MCR)** are the absolute minimum requirements that must be addressed to comply with applicable laws, regulations and contracts. MCR are primarily externally-influenced, based on industry, government, state and local regulations. MCR should never imply adequacy for secure practices and data protection, since they are merely compliance-related.
- **Discretionary Security Requirements (DSR)** are tied to the organization’s risk appetite since DSR are “above and beyond” MCR, where the organization self-identifies additional cybersecurity and data protection controls to address voluntary industry practices or internal requirements, such as findings from internal audits or risk assessments. DSR are primarily internally-influenced, based on the organization’s respective industry and risk tolerance. While MCR establish the foundational floor that must be adhered to, DSR are where organizations often achieve improved efficiency, automation and enhanced security.
## Using The SCF Starts With Defining "Must Have" & "Nice to Have" Requirements
As described above, the concept of MCR & DSR are a crucial step to get right, otherwise you will likely design it incorrectly that will leave gaps that can expose your organization to issues of non-compliance and/or inadequate security practices.
When you add MCR & DSR, you are able to define "what right looks like" for your organization, which equates to your Minimum Security Requirements (MSR) that can be published to project teams, risk management, engineers, etc. The MSR is the blueprint for an organization to build security and privacy in by design across the SDLC and business-as-usual operations.
## Plan, Do, Check & Act (PDCA) Approach To Cybersecurity & Data Protection
Within the ICM, its principles are overlaid onto the following graphic to show how a PDCA approach for continuous improvement of your cybersecurity and data protection program is possible:
1. Establish Context
2. Define Applicable Controls
3. Assign Maturity-Based Criteria
4. Publish Policies, Standards & Procedures
5. Assign Stakeholder Accountability
6. Maintain Situational Awareness
7. Manage Risk
8. Evolve Processes
## More Than Just A Control Set
Where the SCF sets itself apart from other metaframeworks is the following:
- Capability maturity criteria for each control
- Proposed control weighting (not all controls are as important in risk management decisions)
- Built-in risk catalog
- Built-in threat catalog
For the capability maturity criteria, we published the [Cybersecurity & Data Privacy Capability Maturity Model](https://securecontrolsframework.com/capability-maturity-model/) [(C\|P-CMM)](https://securecontrolsframework.com/capability-maturity-model/).
To make use of the risk & threat catalogs, we published the [Cybersecurity & Data Privacy Risk Management Model](https://www.securecontrolsframework.com/sp-rmm) [(C\|P-RMM)](https://securecontrolsframework.com/risk-management-model/).
This is where the Integrated Controls Management (ICM) model ties all those capabilities together to help you design the controls that are right for your organization, as well as be able to leverage that same control set to help understand risks and threats. This is a "paint by numbers" approach to operationalizing your cybersecurity and data protection program!
## Understanding Cybersecurity & Privacy By Design
### Security by Design (SbD)
| | |
| --- | --- |
|  | These requirements come from numerous sources. In this context, some of the most important cybersecurity frameworks are:
- International Organization for Standardization (ISO)
- National Institute for Standards & Technology (NIST)
- US Government (HIPAA, FedRAMP, DFARS, FAR & FTC Act)
- Information Systems Audit and Control Association (ISACA)
- Cloud Security Alliance (CSA)
- Center for Internet Security (CIS)
- Open Web Application Security Project (OWASP)
- Payment Card Industry Data Security Standard (PCI DSS)
- European Union General Data Protection Regulation (EU GDPR) |
## Privacy by Design (PbD)
| | |
| --- | --- |
| 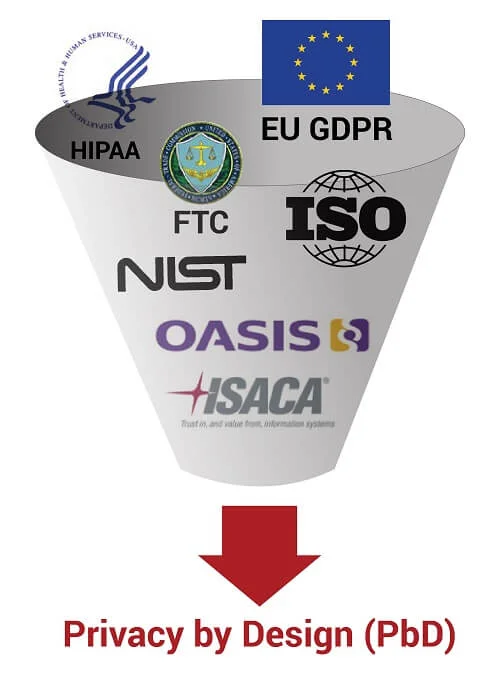 | These requirements come from numerous sources. In this context, some of the most important privacy frameworks are:
- Generally Accepted Privacy Principles (GAPP)
- Fair Information Practice Principles (FIPPs)
- Organization for the Advancement of Structured Information Standards (OASIS)
- International Organization for Standardization (ISO)
- National Institute for Standards & Technology (NIST)
- Information Systems Audit and Control Association (ISACA)
- European Union General Data Protection Regulation (EU GDPR)
- US Government (HIPAA & FTC Act) |
## Statutory Cybersecurity & Privacy Requirements
Statutory obligations are required by law and refer to current laws that were passed by a state or federal government. From a cybersecurity and privacy perspective, statutory compliance requirements include:
- **US - Federal Laws**
- Children's Online Privacy Protection Act (COPPA)
- Fair and Accurate Credit Transactions Act (FACTA) - including "Red Flags" rule
- Family Education Rights and Privacy Act (FERPA)
- Federal Information Security Management Act (FISMA)
- Federal Trade Commission (FTC) Act
- Gramm-Leach-Bliley Act (GLBA)
- Health Insurance Portability and Accountability Act (HIPAA)
- Sarbanes-Oxley Act (SOX)
- **US - State Laws**
- California SB1386
- California Consumer Privacy Act (CCPA)
- Massachusetts 201 CMR 17.00
- Oregon ORS 646A.622
- **International Laws**
- Canada - Personal Information Protection and Electronic Documents Act (PIPEDA)
- UK - Data Protection Act (DPA)
- Other countries' variations of Personal Data Protect Acts (PDPA)
## Regulatory Cybersecurity & Privacy Requirements
Regulatory obligations are required by law, but are different from statutory requirements in that these requirements refer to rules issued by a regulating body that is appointed by a state or federal government. These are legal requirements through proxy, where the regulating body is the source of the requirement. It is important to keep in mind that regulatory requirements tend to change more often than statutory requirements. From a cybersecurity and privacy perspective, regulatory compliance examples include:
- **US Regulations**
- Defense Federal Acquisition Regulation Supplement (DFARS) - NIST 800-171
- Federal Acquisition Regulation (FAR)
- Federal Risk and Authorization Management Program (FedRAMP)
- DoD Information Assurance Risk Management Framework (DIARMF)
- National Industrial Security Program Operating Manual (NISPOM)
- New York Department of Financial Services (NY DFS) 23 NYCRR 500
- **International Regulations**
- European Union General Data Protection Regulation (EU GDPR)
- EU ePrivacy Directive
## Contractual Cybersecurity & Privacy Requirements
Contractual obligations are required by legal contract between private parties. This may be as simple as a cybersecurity or privacy addendum in a vendor contract that calls out unique requirements. It also includes broader requirements from an industry association that membership brings certain obligations. From a cybersecurity and privacy perspective, common contractual compliance requirements include:
- Payment Card Industry Data Security Standard (PCI DSS)
- Financial Industry Regulatory Authority (FINRA)
- Service Organization Control (SOC)
- Generally Accepted Privacy Principles (GAPP)
## Industry-Leading "Best Practices" for Cybersecurity & Privacy
Leading practices may be required under a contractual obligation with a client or partner, but these industry frameworks are commonly referenced for “what right looks like” with how technology is implemented. Leading frameworks generally more technical in nature and provide granular requirements. From a cybersecurity and privacy perspective, common leading frameworks include:
- **Cybersecurity Frameworks**
- Center for Internet Security (CIS) Critical Security Controls (CSC)
- Cloud Security Alliance (CSA) Cloud Controls Matrix (CCM)
- Department of Defense Cybersecurity Agency (DISA) Secure Technology Implementation Guides (STIGs)
- ISO 15288: Systems and Software Engineering -- System Life Cycle Processes
- ISO 27002: Information Technology -- Security Techniques -- Code of Practice for Cybersecurity Controls
- NIST 800-37: Guide for Applying the Risk Management Framework to Federal Information Systems: A Security Life Cycle Approach
- NIST 800-39: Managing Cybersecurity Risk: Organization, Mission and Information System View
- NIST 800-53: Security and Privacy Controls for Federal Information Systems and Organizations
- NIST 800-64: Security Considerations in System Development Lifecycle
- NIST 800-122: Guide to Protecting the Confidentiality of Personally Identifiable Information (PII)
- NIST 800-160: Systems Security Engineering: Considerations for a Multidisciplinary Approach in the Engineering of Trustworthy Secure Systems
- NIST 800-161: Supply Chain Risk Management Practices for Federal Information Systems and Organizations
- NIST 800-171: Protecting Controlled Unclassified Information in Nonfederal Information Systems and Organizations
- NIST IR 7298: Glossary of Key Cybersecurity Terms
- NIST IR 8062: An Introduction to Privacy Engineering and Risk Management in Federal Systems
- NIST IR 8179: Criticality Analysis Process Model: Prioritizing Systems and Components \[draft\]
- Open Web Application Security Project (OWASP)
- OWASP Top 10 Most Critical Web Application Security Risks
- OWASP Application Security Verification Standard Project (ASVS)
- **Privacy Frameworks**
- Fair Information Practice Principles (FIPP)
- Generally Accepted Privacy Practices (GAPP)
- ISO 27018: Information Technology -- Security Techniques -- Code of Practice for Protection of Personally Identifiable Information (PII) in Public Clouds Acting as PII Processors
- OASIS Privacy Management Reference Model and Methodology (PMRM)
- Privacy by Design (PbD)
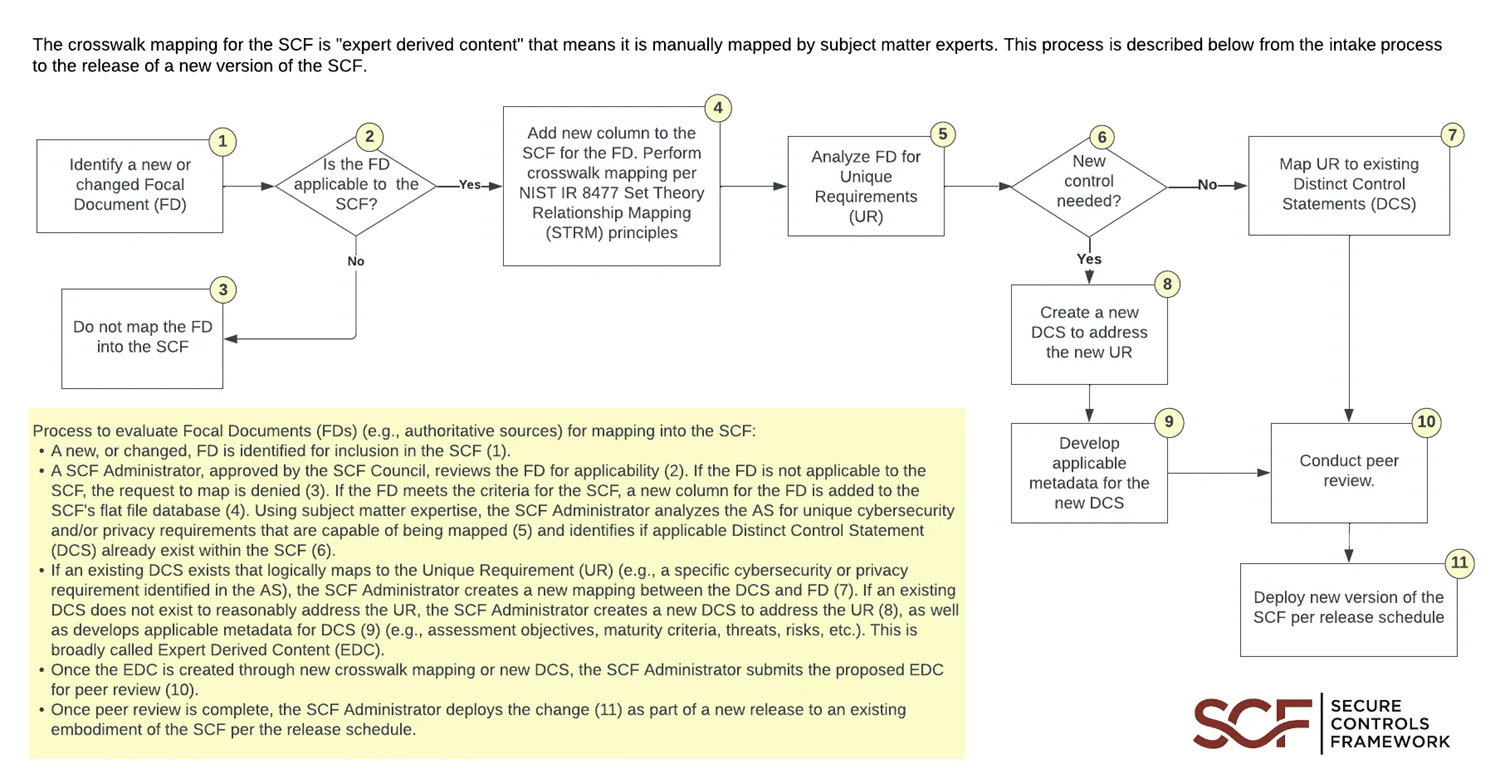
## How The SCF Is Mapped
The crosswalk mapping for the SCF is "expert-derived content" which means it is manually mapped by subject matter experts. This process is described below from the intake process to the release of a new version of the SCF:
[](https://securecontrolsframework.com/)
© 2025 Secure Controls Framework
All rights reserved.
\| [Sitemap](https://securecontrolsframework.com/sitemap.php)
We use cookies (and other similar technologies) to collect data to improve your shopping experience. By using our website, you're agreeing to the collection of data as described in our [Privacy Policy](https://securecontrolsframework.com/privacy-notice/).
SettingsReject allAccept All Cookies
## SCF License Agreement
# Secure Controls Framework (SCF) End User License Agreement (EULA)
We are committed to keeping the SCF a free resource for organizations to use. Therefore, we are using the [Creative Commons Attribution-NoDerivatives 4.0 International Public License](https://creativecommons.org/licenses/by-nd/4.0/) to help maintain the integrity of the SCF.
### Under the SCF's terms and conditions:
- **Attribution**— You must give [appropriate credit](https://creativecommons.org/licenses/by-nd/4.0/), provide a link to the license and [indicate if changes were made](https://creativecommons.org/licenses/by-nd/4.0/). You may do so in any reasonable manner, but not in any way that suggests the licensor endorses you or your use. Providing attribution is as simple as stating SCF controls are used in the solution, such as a GRC platform that includes SCF content is required to provide attribution that SCF controls are used.
- **NoDerivatives**— If you [remix, transform, or build upon](https://creativecommons.org/licenses/by-nd/4.0/) the material, you may not distribute the modified material. For example, you are prohibited from leveraging SCF material to create a derivative solution (e.g., SCF 2.0). **This prohibition on creating derivative works includes utilizing Artificial Intelligence (AI) (or similar technologies) to leverage SCF content to generate policies, standards, procedures, metrics, risks, threats or other derivative content.** An organization needs to be a [Licensed Content Provider (LCP)](https://securecontrolsframework.com/marketplace/scf-licensed-content-provider/ "Licensed Content Provider (LCP)") to offer derivative SCF content, which involves paying for a commercial license.
Effective Date: 22 March 2019
## Creative Commons Attribution-NoDerivatives 4.0 International Public License
By exercising the Licensed Rights (defined below), You accept and agree to be bound by the terms and conditions of this **Creative Commons Attribution-NoDerivatives 4.0 International Public License** ("Public License"). To the extent this Public License may be interpreted as a contract, You are granted the Licensed Rights in consideration of Your acceptance of these terms and conditions, and Secure Controls Framework Council, LLC (Licensor) grants You such rights in consideration of benefits the Licensor receives from making the Licensed Material available under these terms and conditions.
**Section 1 – Definitions.**
a. Adapted Material means material subject to Copyright and Similar Rights that is derived from or based upon the Licensed Material and in which the Licensed Material is translated, altered, arranged, transformed, or otherwise modified in a manner requiring permission under the Copyright and Similar Rights held by the Licensor. For purposes of this Public License, where the Licensed Material is a musical work, performance, or sound recording, Adapted Material is always produced where the Licensed Material is synched in timed relation with a moving image.
b. Copyright and Similar Rights means copyright and/or similar rights closely related to copyright including, without limitation, performance, broadcast, sound recording, and Sui Generis Database Rights, without regard to how the rights are labeled or categorized. For purposes of this Public License, the rights specified in Section 2(b)(1)-(2) are not Copyright and Similar Rights.
c. Effective Technological Measures means those measures that, in the absence of proper authority, may not be circumvented under laws fulfilling obligations under Article 11 of the WIPO Copyright Treaty adopted on December 20, 1996, and/or similar international agreements.
d. Exceptions and Limitations means fair use, fair dealing, and/or any other exception or limitation to Copyright and Similar Rights that applies to Your use of the Licensed Material.
e. Licensed Material means the artistic or literary work, database, or other material to which the Licensor applied this Public License.
f. Licensed Rights means the rights granted to You subject to the terms and conditions of this Public License, which are limited to all Copyright and Similar Rights that apply to Your use of the Licensed Material and that the Licensor has authority to license.
g. Licensor means the individual(s) or entity(ies) granting rights under this Public License.
h. Share means to provide material to the public by any means or process that requires permission under the Licensed Rights, such as reproduction, public display, public performance, distribution, dissemination, communication, or importation, and to make material available to the public including in ways that members of the public may access the material from a place and at a time individually chosen by them.
i. Sui Generis Database Rights means rights other than copyright resulting from Directive 96/9/EC of the European Parliament and of the Council of 11 March 1996 on the legal protection of databases, as amended and/or succeeded, as well as other essentially equivalent rights anywhere in the world.
j. You means the individual or entity exercising the Licensed Rights under this Public License. Your has a corresponding meaning.
**Section 2 – Scope.**
a. License grant.
1\. Subject to the terms and conditions of this Public License, the Licensor hereby grants You a worldwide, royalty-free, non-sublicensable, non-exclusive, irrevocable license to exercise the Licensed Rights in the Licensed Material to:
A. reproduce and Share the Licensed Material, in whole or in part; and
B. produce and reproduce, but not Share, Adapted Material.
2. Exceptions and Limitations. For the avoidance of doubt, where Exceptions and Limitations apply to Your use, this Public License does not apply, and You do not need to comply with its terms and conditions.
3. Term. The term of this Public License is specified in Section 6(a).
4. Media and formats; technical modifications allowed. The Licensor authorizes You to exercise the Licensed Rights in all media and formats whether now known or hereafter created, and to make technical modifications necessary to do so. The Licensor waives and/or agrees not to assert any right or authority to forbid You from making technical modifications necessary to exercise the Licensed Rights, including technical modifications necessary to circumvent Effective Technological Measures. For purposes of this Public License, simply making modifications authorized by this Section 2(a)(4) never produces Adapted Material.
5. Downstream recipients.
A. Offer from the Licensor – Licensed Material. Every recipient of the Licensed Material automatically receives an offer from the Licensor to exercise the Licensed Rights under the terms and conditions of this Public License.
B. No downstream restrictions. You may not offer or impose any additional or different terms or conditions on, or apply any Effective Technological Measures to, the Licensed Material if doing so restricts exercise of the Licensed Rights by any recipient of the Licensed Material.
6. No endorsement. Nothing in this Public License constitutes or may be construed as permission to assert or imply that You are, or that Your use of the Licensed Material is, connected with, or sponsored, endorsed, or granted official status by, the Licensor or others designated to receive attribution as provided in Section 3(a)(1)(A)(i).
b. Other rights.
1\. Moral rights, such as the right of integrity, are not licensed under this Public License, nor are publicity, privacy, and/or other similar personality rights; however, to the extent possible, the Licensor waives and/or agrees not to assert any such rights held by the Licensor to the limited extent necessary to allow You to exercise the Licensed Rights, but not otherwise.
2\. Patent and trademark rights are not licensed under this Public License.
3\. To the extent possible, the Licensor waives any right to collect royalties from You for the exercise of the Licensed Rights, whether directly or through a collecting society under any voluntary or waivable statutory or compulsory licensing scheme. In all other cases the Licensor expressly reserves any right to collect such royalties.
**Section 3 – License Conditions.**
Your exercise of the Licensed Rights is expressly made subject to the following conditions.
a. Attribution.
1\. If You Share the Licensed Material, You must:
A. retain the following if it is supplied by the Licensor with the Licensed Material:
identification of the creator(s) of the Licensed Material and any others designated to receive attribution, in any reasonable manner requested by the Licensor (including by pseudonym if designated);
i. a copyright notice;
ii. a notice that refers to this Public License;
iii. a notice that refers to the disclaimer of warranties;
iv. a URI or hyperlink to the Licensed Material to the extent reasonably practicable;
B. indicate if You modified the Licensed Material and retain an indication of any previous modifications; and
C. indicate the Licensed Material is licensed under this Public License, and include the text of, or the URI or hyperlink to, this Public License.
b. For the avoidance of doubt, You do not have permission under this Public License to Share Adapted Material.
1\. You may satisfy the conditions in Section 3(a)(1) in any reasonable manner based on the medium, means, and context in which You Share the Licensed Material. For example, it may be reasonable to satisfy the conditions by providing a URI or hyperlink to a resource that includes the required information.
2\. If requested by the Licensor, You must remove any of the information required by Section 3(a)(1)(A) to the extent reasonably practicable.
**Section 4 – Sui Generis Database Rights.**
Where the Licensed Rights include Sui Generis Database Rights that apply to Your use of the Licensed Material:
a. for the avoidance of doubt, Section 2(a)(1) grants You the right to extract, reuse, reproduce, and Share all or a substantial portion of the contents of the database, provided You do not Share Adapted Material;
b. if You include all or a substantial portion of the database contents in a database in which You have Sui Generis Database Rights, then the database in which You have Sui Generis Database Rights (but not its individual contents) is Adapted Material; and
c. You must comply with the conditions in Section 3(a) if You Share all or a substantial portion of the contents of the database.
d. For the avoidance of doubt, this Section 4 supplements and does not replace Your obligations under this Public License where the Licensed Rights include other Copyright and Similar Rights.
**Section 5 – Disclaimer of Warranties and Limitation of Liability.**
a. Unless otherwise separately undertaken by the Licensor, to the extent possible, the Licensor offers the Licensed Material as-is and as-available, and makes no representations or warranties of any kind concerning the Licensed Material, whether express, implied, statutory, or other. This includes, without limitation, warranties of title, merchantability, fitness for a particular purpose, non-infringement, absence of latent or other defects, accuracy, or the presence or absence of errors, whether or not known or discoverable. Where disclaimers of warranties are not allowed in full or in part, this disclaimer may not apply to You.
b. To the extent possible, in no event will the Licensor be liable to You on any legal theory (including, without limitation, negligence) or otherwise for any direct, special, indirect, incidental, consequential, punitive, exemplary, or other losses, costs, expenses, or damages arising out of this Public License or use of the Licensed Material, even if the Licensor has been advised of the possibility of such losses, costs, expenses, or damages. Where a limitation of liability is not allowed in full or in part, this limitation may not apply to You.
c. The disclaimer of warranties and limitation of liability provided above shall be interpreted in a manner that, to the extent possible, most closely approximates an absolute disclaimer and waiver of all liability.
**Section 6 – Term and Termination.**
a. This Public License applies for the term of the Copyright and Similar Rights licensed here. However, if You fail to comply with this Public License, then Your rights under this Public License terminate automatically.
b. Where Your right to use the Licensed Material has terminated under Section 6(a), it reinstates:
- automatically as of the date the violation is cured, provided it is cured within 30 days of Your discovery of the violation; or
- upon express reinstatement by the Licensor.
c. For the avoidance of doubt, this Section 6(b) does not affect any right the Licensor may have to seek remedies for Your violations of this Public License.
d. For the avoidance of doubt, the Licensor may also offer the Licensed Material under separate terms or conditions or stop distributing the Licensed Material at any time; however, doing so will not terminate this Public License.
e. Sections 1, 5, 6, 7, and 8 survive termination of this Public License.
**Section 7 – Other Terms and Conditions.**
a. The Licensor shall not be bound by any additional or different terms or conditions communicated by You unless expressly agreed.
b. Any arrangements, understandings, or agreements regarding the Licensed Material not stated herein are separate from and independent of the terms and conditions of this Public License.
**Section 8 – Interpretation.**
a. For the avoidance of doubt, this Public License does not, and shall not be interpreted to, reduce, limit, restrict, or impose conditions on any use of the Licensed Material that could lawfully be made without permission under this Public License.
b. To the extent possible, if any provision of this Public License is deemed unenforceable, it shall be automatically reformed to the minimum extent necessary to make it enforceable. If the provision cannot be reformed, it shall be severed from this Public License without affecting the enforceability of the remaining terms and conditions.
c. No term or condition of this Public License will be waived and no failure to comply consented to unless expressly agreed to by the Licensor.
d. Nothing in this Public License constitutes or may be interpreted as a limitation upon, or waiver of, any privileges and immunities that apply to the Licensor or You, including from the legal processes of any jurisdiction or authority.
Additional languages available: [Bahasa, Indonesia](https://creativecommons.org/licenses/by-nd/4.0/legalcode.id), [euskara](https://creativecommons.org/licenses/by-nd/4.0/legalcode.eu), [Deutsch](https://creativecommons.org/licenses/by-nd/4.0/legalcode.de), [Español](https://creativecommons.org/licenses/by-nd/4.0/legalcode.es), [français](https://creativecommons.org/licenses/by-nd/4.0/legalcode.fr), [hrvatski](https://creativecommons.org/licenses/by-nd/4.0/legalcode.hr), [italiano](https://creativecommons.org/licenses/by-nd/4.0/legalcode.it), [latviski](https://creativecommons.org/licenses/by-nd/4.0/legalcode.lv), [Lietuvių](https://creativecommons.org/licenses/by-nd/4.0/legalcode.lt), [Nederlands](https://creativecommons.org/licenses/by-nd/4.0/legalcode.nl), [norsk](https://creativecommons.org/licenses/by-nd/4.0/legalcode.no), [polski](https://creativecommons.org/licenses/by-nd/4.0/legalcode.pl), [português](https://creativecommons.org/licenses/by-nd/4.0/legalcode.pt), [suomeksi](https://creativecommons.org/licenses/by-nd/4.0/legalcode.fi), [svenska](https://creativecommons.org/licenses/by-nd/4.0/legalcode.sv), [te reo Māori](https://creativecommons.org/licenses/by-nd/4.0/legalcode.mi), [Türkçe](https://creativecommons.org/licenses/by-nd/4.0/legalcode.tr), [Ελληνικά](https://creativecommons.org/licenses/by-nd/4.0/legalcode.el), [русский](https://creativecommons.org/licenses/by-nd/4.0/legalcode.ru), [українська](https://creativecommons.org/licenses/by-nd/4.0/legalcode.uk), [العربية](https://creativecommons.org/licenses/by-nd/4.0/legalcode.ar), [日本語](https://creativecommons.org/licenses/by-nd/4.0/legalcode.ja). Please read the [FAQ](https://wiki.creativecommons.org/FAQ#officialtranslations) for more information about official translations.
[](https://securecontrolsframework.com/)
© 2025 Secure Controls Framework
All rights reserved.
\| [Sitemap](https://securecontrolsframework.com/sitemap.php)
We use cookies (and other similar technologies) to collect data to improve your shopping experience. By using our website, you're agreeing to the collection of data as described in our [Privacy Policy](https://securecontrolsframework.com/privacy-notice/).
SettingsReject allAccept All Cookies